1199:
25:
238:
168:
cryptographic machine (not a rotor machine) in 1912. At the time he had no funds to be able to spend time working on such a device, but he continued to produce designs. Hebern made his first drawings of a rotor-based machine in 1917, and in 1918 he built a model of it. In 1921 he applied for a patent for it, which was issued in 1924. He continued to make improvements, adding more rotors.
269:, with the exception that it required no manual lookup of the keys or cyphertext. Operators simply turned the rotor to a pre-chosen starting position and started typing. To decrypt the message, they turned the rotor around in its socket so it was "backwards", thus reversing all the substitutions. They then typed in the ciphertext and out came the plaintext.
122:
277:
on the one beside it, each one being turned one position after the one beside it rotates a full turn. In this way the number of such alphabets increases dramatically. For a rotor with 26 letters in its alphabet, five such rotors "stacked" in this fashion allows for 26 = 11,881,376 different possible
252:
When the user pressed a key on the typewriter keyboard, a small amount of current from a battery flowed through the key into one of the contacts on the input side of the disk, through the wiring, and back out a different contact. The power then operated the mechanicals of an electric typewriter to
264:
Normally such a system would be no better than the single-alphabet systems of the 16th century. However the rotor in the Hebern machine was geared to the keyboard on the typewriter, so that after every keypress, the rotor turned and the substitution alphabet thus changed slightly. This turns the
167:
was a building contractor who was jailed in 1908 for stealing a horse. It is claimed that, with time on his hands, he started thinking about the problem of encryption, and eventually devised a means of mechanizing the process with a typewriter. He filed his first patent application for a
203:'s confidential analysis of the Hebern machine's weaknesses (substantial, though repairable) that its sales to the US government were so limited; Hebern was never told of them. Perhaps the best indication of a general distaste for such matters was the statement by
284:
attacked the Hebern machine soon after it came on the market in the 1920s. He quickly "solved" any machine that was built similar to the Hebern, in which the rotors were stacked with the rotor at one end or the other turning with each keypress, the so-called
272:
Better yet, several rotors can be placed such that the output of the first is connected to the input of the next. In this case the first rotor operates as before, turning once with each keypress. Additional rotors are then spun with a
289:. In these cases the resulting ciphertext consisted of a series of single-substitution cyphers, each one 26 letters long. He showed that fairly standard techniques could be used against such systems, given enough effort.
372:
From p. 188: "Stinson, as
Secretary of State, was dealing as a gentleman with the gentlemen sent as ambassadors and ministers from friendly nations, and as he later said, 'Gentlemen do not read each other's mail.'
249:. Linking the contacts on either side of the rotor were wires, with each letter on one side being wired to another on the far side in a random fashion. The wiring encoded a single substitution alphabet.
225:
There were three other patents for rotor machines issued in 1919, and several other rotor machines were designed independently at about the same time. The most successful and widely used was the
199:, as well as to commercial interests such as banks. None was terribly interested, as at the time cryptography was not widely considered important outside governments. It was probably because of
222:. He spent another brief period in jail, but never gave up on the idea of his machine. In 1931 the Navy finally purchased several systems, but this was to be his only real sale.
141:
with the electrical parts of an electric typewriter, connecting the two through a scrambler. It is the first example (though just barely) of a class of machines known as
1179:
1009:
207:
in his memoirs that "Gentlemen do not read each other's mail." It was
Stimson, as Secretary of State under Hoover, who withdrew State Department support for
292:
Of course, this fact was itself a great secret. This may explain why the Army and Navy were unwilling to use Hebern's design, much to his surprise.
704:
421:
862:
89:
61:
42:
68:
414:
191:
company with money from several investors. Over the next few years he repeatedly tried to sell the machines both to the
75:
855:
108:
1227:
57:
1058:
407:
46:
848:
365:
1174:
1129:
942:
1053:
1169:
800:
719:
1159:
1149:
1004:
484:
709:
386:
245:
The key to the Hebern design was a disk with electrical contacts on either side, known today as a
184:, spent some time working with Hebern before returning to Washington and OP-20-G in the mid-'20s.
82:
1232:
1154:
1144:
947:
907:
900:
890:
885:
785:
444:
35:
895:
646:
509:
504:
212:
1202:
1048:
994:
780:
775:
750:
555:
550:
338:
1164:
1088:
813:
499:
169:
8:
927:
808:
694:
281:
200:
1033:
1017:
964:
219:
196:
192:
172:, the chief civilian employee of the US Navy's cryptography operation (later to become
266:
1093:
1083:
954:
1028:
153:
494:
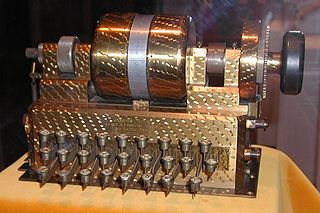
274:
208:
1103:
1023:
984:
932:
917:
595:
580:
545:
489:
449:
226:
187:
Hebern was so convinced of the future success of the system that he formed the
354:
U.S. Patent no. 1,683,072 (filed: 1923 November 20; issued: 1928 September 4).
351:
328:, Karl Maria Michael de Leeuw & Jan Bergstra, eds. Elsevier, 2007, p. 385.
309:
1221:
1184:
1139:
1098:
1078:
974:
937:
912:
641:
436:
341:
U.S. Patent no. 1,510,441 (filed: 1921 March 31; issued: 1924 September 30).
204:
164:
142:
1134:
979:
969:
959:
922:
871:
661:
181:
146:
1113:
699:
565:
312:
U.S. Patent no. 1,086,823 (filed: 3 June 1912; issued: 10 February 1914).
258:
177:
149:
and for some time after, and which included such famous examples as the
1073:
1043:
1038:
999:
674:
265:
basic substitution into a polyalphabetic one similar to the well known
254:
138:
134:
1063:
24:
1108:
1068:
823:
818:
218:
Eventually his investors ran out of patience, and sued Hebern for
729:
714:
669:
621:
600:
173:
150:
237:
989:
790:
770:
734:
724:
651:
524:
519:
514:
474:
454:
253:
type the encrypted letter, or alternately simply lit a bulb or
370:. New York, New York, USA: Harper & Brothers. p. 188.
137:
machine built by combining the mechanical parts of a standard
765:
760:
755:
689:
684:
636:
631:
626:
616:
590:
575:
560:
529:
479:
464:
326:
The
History of Information Security: A Comprehensive Handbook
324:
Bauer, FL. The origin of the rotor idea. 14.1.3.1 Hebern. In:
679:
585:
570:
469:
121:
145:
that would become the primary form of encryption during
1010:
Cryptographically secure pseudorandom number generator
391:
310:"Cryptographic attachment for type-writing machines"
49:. Unsourced material may be challenged and removed.
1219:
856:
415:
241:Hebern single-rotor machine patent #1,510,441
363:
364:Stinson, Henry L.; Bundy, McGeorge (1948).
863:
849:
422:
408:
109:Learn how and when to remove this message
236:
120:
320:
318:
1220:
844:
403:
16:Electro-mechanical encryption machine
315:
47:adding citations to reliable sources
18:
429:
13:
367:On Active Service in Peace and War
14:
1244:
380:
1198:
1197:
870:
23:
34:needs additional citations for
1059:Information-theoretic security
357:
344:
331:
302:
232:
125:A single-rotor Hebern machine.
1:
295:
7:
1175:Message authentication code
1130:Cryptographic hash function
943:Cryptographic hash function
10:
1249:
1054:Harvest now, decrypt later
339:"Electric coding machine,"
215:, leading to its closing.
159:
133:was an electro-mechanical
1193:
1170:Post-quantum cryptography
1122:
878:
840:
799:
743:
660:
609:
538:
435:
399:
395:
1160:Quantum key distribution
1150:Authenticated encryption
1005:Random number generation
387:The Hebern Code machines
1155:Public-key cryptography
1145:Symmetric-key algorithm
948:Key derivation function
908:Cryptographic primitive
901:Authentication protocol
891:Outline of cryptography
886:History of cryptography
352:"Electric code machine"
1228:Cryptographic hardware
896:Cryptographic protocol
647:Siemens and Halske T52
242:
213:American Black Chamber
126:
58:"Hebern rotor machine"
1049:End-to-end encryption
995:Cryptojacking malware
710:Sectéra Secure Module
240:
124:
1165:Quantum cryptography
1089:Trusted timestamping
814:Intel SHA extensions
189:Hebern Electric Code
131:Hebern Rotor Machine
43:improve this article
928:Cryptographic nonce
809:AES instruction set
337:Hebern, Edward H.,
282:William F. Friedman
201:William F. Friedman
1034:Subliminal channel
1018:Pseudorandom noise
965:Key (cryptography)
350:Hebern, Edward H.
308:Hebern, Edward H.
243:
220:stock manipulation
165:Edward Hugh Hebern
127:
1215:
1214:
1211:
1210:
1094:Key-based routing
1084:Trapdoor function
955:Digital signature
836:
835:
832:
831:
801:Computer hardware
546:Bazeries cylinder
119:
118:
111:
93:
1240:
1201:
1200:
1029:Insecure channel
865:
858:
851:
842:
841:
424:
417:
410:
401:
400:
397:
396:
393:
392:
374:
371:
361:
355:
348:
342:
335:
329:
322:
313:
306:
114:
107:
103:
100:
94:
92:
51:
27:
19:
1248:
1247:
1243:
1242:
1241:
1239:
1238:
1237:
1218:
1217:
1216:
1207:
1189:
1118:
874:
869:
828:
795:
739:
656:
642:Lorenz SZ 40/42
605:
534:
431:
430:Cipher machines
428:
383:
378:
377:
362:
358:
349:
345:
336:
332:
323:
316:
307:
303:
298:
278:substitutions.
267:Vigenère cipher
235:
209:Herbert Yardley
162:
115:
104:
98:
95:
52:
50:
40:
28:
17:
12:
11:
5:
1246:
1236:
1235:
1233:Rotor machines
1230:
1213:
1212:
1209:
1208:
1206:
1205:
1194:
1191:
1190:
1188:
1187:
1182:
1180:Random numbers
1177:
1172:
1167:
1162:
1157:
1152:
1147:
1142:
1137:
1132:
1126:
1124:
1120:
1119:
1117:
1116:
1111:
1106:
1104:Garlic routing
1101:
1096:
1091:
1086:
1081:
1076:
1071:
1066:
1061:
1056:
1051:
1046:
1041:
1036:
1031:
1026:
1024:Secure channel
1021:
1015:
1014:
1013:
1002:
997:
992:
987:
985:Key stretching
982:
977:
972:
967:
962:
957:
952:
951:
950:
945:
935:
933:Cryptovirology
930:
925:
920:
918:Cryptocurrency
915:
910:
905:
904:
903:
893:
888:
882:
880:
876:
875:
868:
867:
860:
853:
845:
838:
837:
834:
833:
830:
829:
827:
826:
821:
816:
811:
805:
803:
797:
796:
794:
793:
788:
783:
778:
773:
768:
763:
758:
753:
747:
745:
741:
740:
738:
737:
732:
727:
722:
717:
712:
707:
702:
697:
692:
687:
682:
677:
672:
666:
664:
658:
657:
655:
654:
649:
644:
639:
634:
629:
624:
619:
613:
611:
607:
606:
604:
603:
598:
596:Reihenschieber
593:
588:
583:
581:Jefferson disk
578:
573:
568:
563:
558:
553:
548:
542:
540:
536:
535:
533:
532:
527:
522:
517:
512:
507:
502:
497:
492:
487:
482:
477:
472:
467:
462:
457:
452:
447:
441:
439:
437:Rotor machines
433:
432:
427:
426:
419:
412:
404:
390:
389:
382:
381:External links
379:
376:
375:
356:
343:
330:
314:
300:
299:
297:
294:
234:
231:
227:Enigma machine
170:Agnes Driscoll
161:
158:
143:rotor machines
117:
116:
31:
29:
22:
15:
9:
6:
4:
3:
2:
1245:
1234:
1231:
1229:
1226:
1225:
1223:
1204:
1196:
1195:
1192:
1186:
1185:Steganography
1183:
1181:
1178:
1176:
1173:
1171:
1168:
1166:
1163:
1161:
1158:
1156:
1153:
1151:
1148:
1146:
1143:
1141:
1140:Stream cipher
1138:
1136:
1133:
1131:
1128:
1127:
1125:
1121:
1115:
1112:
1110:
1107:
1105:
1102:
1100:
1099:Onion routing
1097:
1095:
1092:
1090:
1087:
1085:
1082:
1080:
1079:Shared secret
1077:
1075:
1072:
1070:
1067:
1065:
1062:
1060:
1057:
1055:
1052:
1050:
1047:
1045:
1042:
1040:
1037:
1035:
1032:
1030:
1027:
1025:
1022:
1019:
1016:
1011:
1008:
1007:
1006:
1003:
1001:
998:
996:
993:
991:
988:
986:
983:
981:
978:
976:
975:Key generator
973:
971:
968:
966:
963:
961:
958:
956:
953:
949:
946:
944:
941:
940:
939:
938:Hash function
936:
934:
931:
929:
926:
924:
921:
919:
916:
914:
913:Cryptanalysis
911:
909:
906:
902:
899:
898:
897:
894:
892:
889:
887:
884:
883:
881:
877:
873:
866:
861:
859:
854:
852:
847:
846:
843:
839:
825:
822:
820:
817:
815:
812:
810:
807:
806:
804:
802:
798:
792:
789:
787:
784:
782:
779:
777:
774:
772:
769:
767:
764:
762:
759:
757:
754:
752:
749:
748:
746:
742:
736:
733:
731:
728:
726:
723:
721:
718:
716:
713:
711:
708:
706:
703:
701:
698:
696:
693:
691:
688:
686:
683:
681:
678:
676:
673:
671:
668:
667:
665:
663:
659:
653:
650:
648:
645:
643:
640:
638:
635:
633:
630:
628:
625:
623:
620:
618:
615:
614:
612:
608:
602:
599:
597:
594:
592:
589:
587:
584:
582:
579:
577:
574:
572:
569:
567:
564:
562:
559:
557:
554:
552:
549:
547:
544:
543:
541:
537:
531:
528:
526:
523:
521:
518:
516:
513:
511:
508:
506:
503:
501:
498:
496:
493:
491:
488:
486:
483:
481:
478:
476:
473:
471:
468:
466:
463:
461:
458:
456:
453:
451:
448:
446:
443:
442:
440:
438:
434:
425:
420:
418:
413:
411:
406:
405:
402:
398:
394:
388:
385:
384:
369:
368:
360:
353:
347:
340:
334:
327:
321:
319:
311:
305:
301:
293:
290:
288:
283:
279:
276:
270:
268:
262:
260:
257:punch from a
256:
250:
248:
239:
230:
228:
223:
221:
216:
214:
210:
206:
205:Henry Stimson
202:
198:
194:
190:
185:
183:
179:
175:
171:
166:
157:
155:
152:
148:
144:
140:
136:
132:
123:
113:
110:
102:
99:November 2015
91:
88:
84:
81:
77:
74:
70:
67:
63:
60: –
59:
55:
54:Find sources:
48:
44:
38:
37:
32:This article
30:
26:
21:
20:
1135:Block cipher
980:Key schedule
970:Key exchange
960:Kleptography
923:Cryptosystem
872:Cryptography
662:Secure voice
459:
455:M-125 Fialka
366:
359:
346:
333:
325:
304:
291:
286:
280:
271:
263:
251:
246:
244:
224:
217:
188:
186:
163:
147:World War II
130:
128:
105:
96:
86:
79:
72:
65:
53:
41:Please help
36:verification
33:
1123:Mathematics
1114:Mix network
610:Teleprinter
566:Cipher disk
233:Description
1222:Categories
1074:Ciphertext
1044:Decryption
1039:Encryption
1000:Ransomware
675:FASCINATOR
539:Mechanical
296:References
287:fast rotor
255:paper tape
176:) between
139:typewriter
135:encryption
69:newspapers
1064:Plaintext
261:machine.
1203:Category
1109:Kademlia
1069:Codetext
1012:(CSPRNG)
824:IBM 4764
819:IBM 4758
786:Pinwheel
259:teletype
879:General
730:STU-III
715:SIGSALY
670:BID 150
622:BID 770
601:Scytale
525:Singlet
485:Mercury
193:US Navy
174:OP-20-G
160:History
83:scholar
990:Keygen
791:Rockex
781:Purple
771:Noreen
735:VINSON
725:STU-II
695:NESTOR
652:SIGTOT
520:SIGCUM
515:SIGABA
475:Lacida
460:Hebern
450:Enigma
154:Enigma
151:German
85:
78:
71:
64:
56:
1020:(PRN)
766:KL-51
761:KL-43
756:KG-84
744:Other
690:KY-68
685:KY-58
637:KW-37
632:KW-26
627:DUDEK
617:5-UCO
591:M-209
576:Kryha
561:CD-57
530:Typex
510:SG-41
505:SG-39
480:M-325
465:HX-63
247:rotor
90:JSTOR
76:books
751:JADE
705:SCIP
700:OMNI
680:KY-3
586:M-94
571:HC-9
556:C-52
551:C-36
490:NEMA
470:KL-7
197:Army
195:and
182:WWII
180:and
129:The
62:news
776:Red
720:STE
500:RED
495:OMI
445:CCM
275:cam
211:'s
178:WWI
45:by
1224::
317:^
229:.
156:.
864:e
857:t
850:v
423:e
416:t
409:v
373:"
112:)
106:(
101:)
97:(
87:·
80:·
73:·
66:·
39:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.