94:
69:, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a
334:. To detect potential attacks, parties check for discrepancies in response times. For example: Say that two parties normally take a certain amount of time to perform a particular transaction. If one transaction, however, were to take an abnormal length of time to reach the other party, this could be indicative of a third party's interference inserting additional latency in the transaction.
299:, in which both the server and the client validate the other's communication, covers both ends of a MITM attack. If the server or client's identity is not verified or deemed as invalid, the session will end. However, the default behavior of most connections is to only authenticate the server, which means mutual authentication is not always employed and MITM attacks can still occur.
312:(HPKP), sometimes called "certificate pinning", helps prevent a MITM attack in which the certificate authority itself is compromised, by having the server provide a list of "pinned" public key hashes during the first transaction. Subsequent transactions then require one or more of the keys in the list must be used by the server in order to authenticate that transaction.
306:), or recorded attestments such as audio/visual recordings of a public key hash are used to ward off MITM attacks, as visual media is much more difficult and time-consuming to imitate than simple data packet communication. However, these methods require a human in the loop in order to successfully initiate the transaction.
76:
As it aims to circumvent mutual authentication, a MITM attack can succeed only when the attacker impersonates each endpoint sufficiently well to satisfy their expectations. Most cryptographic protocols include some form of endpoint authentication specifically to prevent MITM attacks. For example,
246:
This example shows the need for Alice and Bob to have a means to ensure that they are truly each using each other's public keys, and not the public key of an attacker. Otherwise, such attacks are generally possible, in principle, against any message sent using public-key technology.
113:
wishes to intercept the conversation to eavesdrop (breaking confidentiality) with the option to deliver a false message to Bob under the guise of Alice (breaking non-repudiation). Mallory would perform a man-in-the-middle attack as described in the following sequence of events.
416:
surveillance device that mimics a wireless carrier cell tower in order to force all nearby mobile phones and other cellular data devices to connect to it. The tracker relays all communications back and forth between cellular phones and cell towers.
447:
access to its customers' encrypted browser traffic. Nokia responded by saying that the content was not stored permanently, and that the company had organizational and technical measures to prevent access to private information.
295:(CA). If the original key to authenticate this CA has not been itself the subject of a MITM attack, then the certificates issued by the CA may be used to authenticate the messages sent by the owner of that certificate. Use of
267:
All cryptographic systems that are secure against MITM attacks provide some method of authentication for messages. Most require an exchange of information (such as public keys) in addition to the message over a
1124:
Sasikaladevi, N. and D. Malathi. 2019. “Energy
Efficient Lightweight Mutual Authentication Protocol (REAP) for MBAN Based on Genus-2 Hyper-Elliptic Curve.” Wireless Personal Communications 109(4):2471–88.
359:
from what is suspected to be an attack can be analyzed in order to determine whether there was an attack and, if so, determine the source of the attack. Important evidence to analyze when performing
255:
MITM attacks can be prevented or detected by two means: authentication and tamper detection. Authentication provides some degree of certainty that a given message has come from a legitimate source.
876:
1016:
344:. Protocols based on quantum cryptography typically authenticate part or all of their classical communication with an unconditionally secure authentication scheme. As an example
1450:
345:
1404:
221:
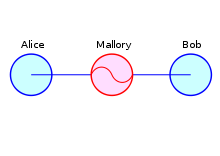
However, because it was actually encrypted with
Mallory's key, Mallory can decrypt it, read it, modify it (if desired), re-encrypt with Bob's key, and forward it to Bob:
1311:
276:, have been developed with different security requirements for the secure channel, though some have attempted to remove the requirement for any secure channel at all.
563: – a cryptographic guarantee of the authenticity of a text, usually the result of a calculation only the author is expected to be able to perform.
1045:
898:"Development of field programmable gate array–based encryption module to mitigate man-in-the-middle attack for nuclear power plant data communication network"
62:
between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two user parties.
726:
291:
against MITM attacks. In such structures, clients and servers exchange certificates which are issued and verified by a trusted third party called a
931:"Detection of man-in-the-middle attacks using physical layer wireless security techniques: Man-in-the-middle attacks using physical layer security"
1156:
330:
Latency examination can potentially detect the attack in certain situations, such as with long calculations that lead into tens of seconds like
1222:
963:
318:
extends the DNS protocol to use signatures to authenticate DNS records, preventing simple MITM attacks from directing a client to a malicious
1674:
1338:
1020:
1426:
461:, a wireless communication protocol, has also been susceptible to man-in-the-middle attacks due to its wireless transmission of data.
1447:
1526:
745:
315:
1394:
1377:
1315:
1179:
781:
608:
507:
uses MITM attacks to inject JavaScript code to 3rd party web pages, showing their own ads and messages on top of the pages
511:
1827:
256:
1832:
1791:
1482:
1059:
539: – the plot against Elizabeth I of England, where Francis Walsingham intercepted the correspondence.
557: – the art of deciphering encrypted messages with incomplete knowledge of how they were encrypted.
533: – a British radio transmitter used for World War II "intrusion" operations, an early MITM attack.
527:– a technique by which an attacker sends Address Resolution Protocol messages onto a local area network
1679:
1134:
Heinrich, Stuart (November 28, 2013). "Public Key
Infrastructure based on Authentication of Media Attestments".
1822:
1506:
1745:
980:
Callegati, Franco; Cerroni, Walter; Ramilli, Marco (2009). "Man-in-the-Middle Attack to the HTTPS Protocol".
587: – a cryptographic protocol for establishing a key in which both parties can have confidence.
288:
808:
575: – a specific protocol to circumvent a MITM attack when the keys may have been compromised.
452:
1204:
331:
773:
629: – Cyber attack in which a person or program successfully masquerades as another by falsifying data
1765:
877:"From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud"
1633:
280:
200:
Alice encrypts a message with what she believes to be Bob's key, thinking that only Bob can read it:
21:
1091:
1567:
530:
284:
78:
180:
Mallory replaces Bob's key with her own, and relays this to Alice, claiming that it is Bob's key:
1643:
309:
1427:"Comcast using man-in-the-middle attack to warn subscribers of potential copyright infringement"
862:
581: – how to manage cryptographic keys, including generation, exchange and storage.
1694:
1521:
1086:
596:
584:
425:
409:
389:
273:
1628:
1164:
2009 Third
International Conference on Emerging Security Information, Systems and Technologies
605: – how communicating parties establish confidence in one another's identities.
1475:
602:
383:
296:
292:
82:
70:
66:
1801:
1796:
1755:
1684:
1542:
796:
capability from the server response, they can easily downgrade the connection to plaintext.
764:
711:
614:
599: – a similar attack, giving only regular access to a communication channel.
548:
337:
8:
1750:
834:
712:"Monsters in the Middleboxes: Introducing Two New Tools for Detecting HTTPS Interception"
766:
Why TLS Is Better
Without STARTTLS: A Security Analysis of STARTTLS in the Email Context
471: – the first public implementation of MITM attacks against SSL and SSHv1
1735:
1572:
1552:
1185:
1135:
1104:
997:
930:
763:
Poddebniak, Damian; Ising, Fabian; Böck, Hanno; Schinzel, Sebastian (August 13, 2021).
590:
572:
474:
341:
59:
1277:
1760:
1714:
1623:
1373:
1285:
1175:
777:
560:
542:
360:
110:
73:
hosting a network without encryption could insert themselves as a man in the middle.
35:
17:
1189:
1001:
617: – the use of quantum mechanics to provide security in cryptography.
1775:
1740:
1468:
1365:
1167:
1108:
1096:
989:
942:
909:
749:
566:
498:
Content
Gateway – used to perform inspection of SSL traffic at the
623: – a way of communicating resistant to interception and tampering.
1770:
1709:
1613:
1454:
1046:"Comcast still uses MITM javascript injection to serve unwanted ads and messages"
632:
626:
139:
Mallory relays this message to Bob; Bob cannot tell it is not really from Alice:
1357:
1730:
1704:
1511:
1369:
620:
578:
536:
436:
428:. Subsequently, the fraudulent certificates were used to perform MITM attacks.
413:
397:
Whether other clients, elsewhere on the
Internet, received the same certificate
356:
269:
1171:
1077:
Merkle, Ralph C (April 1978). "Secure
Communications Over Insecure Channels".
914:
897:
1816:
1689:
1608:
1516:
1289:
554:
455:
withdrew its mobile phone apps following concern about MITM vulnerabilities.
106:
102:
1547:
839:
524:
499:
440:
93:
31:
1362:
2012 International
Conference on Computing, Communication and Applications
1249:
1100:
1699:
1618:
55:
993:
1658:
1638:
1603:
495:
444:
319:
639:
protocol that requires an adversary with a man-in-the-middle position.
611: – a protocol for establishing a key using a password.
1648:
1598:
1254:
946:
881:
489:
458:
421:
1339:"Here's Why Equifax Yanked Its Apps From Apple And Google Last Week"
1140:
302:
Attestments, such as verbal communications of a shared value (as in
793:
569: – attack used against full disk encryption systems
340:, in theory, provides tamper-evidence for transactions through the
1312:"Nokia: Yes, we decrypt your HTTPS data, but don't worry about it"
964:"Comcast continues to inject its own code into websites you visit"
242:
Bob thinks that this message is a secure communication from Alice.
1653:
1562:
1491:
1460:
1017:"How to defend yourself against MITM or Man-in-the-middle attack"
504:
1593:
1588:
484:
468:
464:
Other notable real-life implementations include the following:
118:
Alice sends a message to Bob, which is intercepted by
Mallory:
420:
In 2011, a security breach of the Dutch certificate authority
81:
can authenticate one or both parties using a mutually trusted
1250:"Florida Cops' Secret Weapon: Warrantless Cellphone Tracking"
432:
373:
1278:"DigiNotar Files for Bankruptcy in Wake of Devastating Hack"
728:
Usable Authentication Ceremonies in Secure Instant Messaging
259:
merely shows evidence that a message may have been altered.
1399:
896:
Elakrat, Mohamed Abdallah; Jung, Jae Cheon (June 1, 2018).
762:
303:
58:
where the attacker secretly relays and possibly alters the
1358:"Analysis of Bluetooth threats and v4.0 security features"
636:
545: – the design of secure computer systems.
480:
709:
1157:"Detecting Man-in-the-Middle Attacks by Precise Timing"
979:
439:
was revealed to be decrypting HTTPS traffic on Nokia's
382:
Whether the certificate has been signed by a trusted
929:
Wang, Le; Wyglinski, Alexander M. (October 1, 2014).
1395:"NSA disguised itself as Google to spy, say reports"
1060:"diffie hellman - MiTM on RSA public key encryption"
394:Whether the certificate has been changed recently
1814:
1356:Sandhya, S; Devi, K A Sumithra (February 2012).
1223:"Network Forensic Analysis of SSL MITM Attacks"
551: – a man-in-the-middle exploit.
97:An illustration of the man-in-the-middle attack
1014:
1476:
1337:Weissman, Cale Guthrie (September 15, 2017).
1113:Received August, 1975; revised September 1977
928:
710:Gabbi Fisher; Luke Valenta (March 18, 2019).
635: – a downgrade attack on the
593: – a type of web browser MITM
1154:
935:Wireless Communications and Mobile Computing
379:Whether the certificate has been self signed
1355:
1241:
1070:
895:
746:"Fact Sheet: Machine-in-the-Middle Attacks"
1483:
1469:
1205:"5. Unconditionally secure authentication"
734:(Dipl.-Ing.). Technische Universität Wien.
1139:
1090:
913:
703:
1448:Finding Hidden Threats by Decrypting SSL
1336:
1155:Aziz, Benjamin; Hamilton, Geoff (2009).
1133:
250:
92:
1407:from the original on September 15, 2013
150:"Hi Bob, it's Alice. Give me your key."
125:"Hi Bob, it's Alice. Give me your key."
65:One example of a MITM attack is active
1815:
1527:Timeline of computer viruses and worms
1275:
1247:
1076:
424:resulted in the fraudulent issuing of
160:Bob responds with his encryption key:
1464:
1392:
1309:
1040:
1038:
975:
973:
958:
956:
724:
1393:Moyer, Edward (September 12, 2013).
1202:
1015:Tanmay Patange (November 10, 2013).
982:IEEE Security & Privacy Magazine
609:Password-authenticated key agreement
403:
351:
512:Kazakhstan man-in-the-middle attack
325:
13:
1490:
1276:Zetter, Kim (September 20, 2011).
1035:
970:
953:
902:Nuclear Engineering and Technology
809:"Manipulator-in-the-middle attack"
725:Fassl, Matthias (April 23, 2018).
718:
14:
1844:
1792:Computer and network surveillance
1441:
1310:Meyer, David (January 10, 2013).
388:Whether the certificate has been
262:
363:on a suspected attack includes:
1419:
1386:
1349:
1330:
1303:
1269:
1215:
1196:
1148:
1127:
1118:
1052:
1008:
922:
889:
1507:Comparison of computer viruses
1227:NETRESEC Network Security Blog
869:
855:
827:
801:
774:30th USENIX Security Symposium
756:
738:
651:
272:. Such protocols, often using
1:
1746:Data loss prevention software
1314:. Gigaom, Inc. Archived from
1248:Zetter, Kim (March 3, 2014).
696:
289:Transmission Control Protocol
790:Meddler-in-the-Middle (MitM)
346:Wegman-Carter authentication
7:
1064:Cryptography Stack Exchange
517:
207:"Meet me at the bus stop!"
105:wishes to communicate with
10:
1849:
1766:Intrusion detection system
1370:10.1109/iccca.2012.6179149
376:certificate of the server
88:
15:
1828:Computer network security
1784:
1723:
1667:
1634:Privacy-invasive software
1581:
1535:
1499:
1453:October 18, 2017, at the
1172:10.1109/SECURWARE.2009.20
1079:Communications of the ACM
915:10.1016/j.net.2018.01.018
671:manipulator-in-the-middle
281:public key infrastructure
27:Form of message tampering
22:Meet-in-the-middle attack
1833:Transport Layer Security
843:. Mozilla. July 13, 2022
644:
367:IP address of the server
357:Captured network traffic
285:Transport Layer Security
16:Not to be confused with
1644:Rogue security software
683:adversary-in-the-middle
477:HTTP(S) diagnostic tool
310:HTTP Public Key Pinning
274:key-agreement protocols
232:"Meet me at the park!"
1680:Classic Mac OS viruses
1522:List of computer worms
1457:(PDF). SANS Institute.
1364:. IEEE. pp. 1–4.
863:"Person-in-the-middle"
597:Man-on-the-side attack
585:Key-agreement protocol
531:Aspidistra transmitter
410:Stingray phone tracker
370:DNS name of the server
98:
1823:Cryptographic attacks
1101:10.1145/359460.359473
813:OWASP Community Pages
792:attacker removes the
667:meddler-in-the-middle
663:machine-in-the-middle
659:monster-in-the-middle
603:Mutual authentication
443:, giving the company
384:certificate authority
297:mutual authentication
293:certificate authority
251:Defense and detection
96:
83:certificate authority
1802:Operation: Bot Roast
1433:. November 23, 2015.
1048:. December 28, 2016.
1023:on November 24, 2013
966:. December 11, 2017.
675:person-in-the-middle
615:Quantum cryptography
549:Cookiemonster attack
338:Quantum cryptography
1751:Defensive computing
1668:By operating system
994:10.1109/MSP.2009.12
865:. October 11, 2020.
1736:Antivirus software
1582:Malware for profit
1553:Man-in-the-browser
1500:Infectious malware
1203:Cederlöf, Jörgen.
1166:. pp. 81–86.
815:. OWASP Foundation
591:Man-in-the-browser
573:Interlock protocol
342:no-cloning theorem
99:
71:Wi-Fi access point
1810:
1809:
1761:Internet security
1715:HyperCard viruses
1624:Keystroke logging
1614:Fraudulent dialer
1558:Man-in-the-middle
1379:978-1-4673-0273-9
1181:978-0-7695-3668-2
783:978-1-939133-24-3
752:. March 24, 2020.
561:Digital signature
543:Computer security
483:impersonation of
404:Notable instances
361:network forensics
352:Forensic analysis
40:man-in-the-middle
36:computer security
18:Man-in-the-Mobile
1840:
1776:Network security
1741:Browser security
1485:
1478:
1471:
1462:
1461:
1435:
1434:
1423:
1417:
1416:
1414:
1412:
1390:
1384:
1383:
1353:
1347:
1346:
1334:
1328:
1327:
1325:
1323:
1318:on April 8, 2019
1307:
1301:
1300:
1298:
1296:
1273:
1267:
1266:
1264:
1262:
1245:
1239:
1238:
1236:
1234:
1229:. March 27, 2011
1219:
1213:
1212:
1200:
1194:
1193:
1161:
1152:
1146:
1145:
1143:
1131:
1125:
1122:
1116:
1115:
1094:
1074:
1068:
1067:
1056:
1050:
1049:
1042:
1033:
1032:
1030:
1028:
1019:. Archived from
1012:
1006:
1005:
977:
968:
967:
960:
951:
950:
947:10.1002/wcm.2527
926:
920:
919:
917:
893:
887:
886:
885:. July 12, 2022.
873:
867:
866:
859:
853:
852:
850:
848:
831:
825:
824:
822:
820:
805:
799:
798:
776:. p. 4366.
771:
760:
754:
753:
750:Internet Society
742:
736:
735:
733:
722:
716:
715:
707:
690:
657:Also known as a
655:
567:Evil maid attack
326:Tamper detection
257:Tamper detection
237:
234:→
230:
226:
216:
212:
209:→
205:
195:
191:
186: ←
185:
175:
170: ←
169:
165:
155:
152:→
148:
144:
134:
130:
127:→
123:
1848:
1847:
1843:
1842:
1841:
1839:
1838:
1837:
1813:
1812:
1811:
1806:
1785:Countermeasures
1780:
1771:Mobile security
1719:
1710:Palm OS viruses
1675:Android malware
1663:
1577:
1573:Zombie computer
1531:
1495:
1489:
1455:Wayback Machine
1444:
1439:
1438:
1425:
1424:
1420:
1410:
1408:
1391:
1387:
1380:
1354:
1350:
1335:
1331:
1321:
1319:
1308:
1304:
1294:
1292:
1274:
1270:
1260:
1258:
1246:
1242:
1232:
1230:
1221:
1220:
1216:
1201:
1197:
1182:
1159:
1153:
1149:
1132:
1128:
1123:
1119:
1092:10.1.1.364.5157
1075:
1071:
1058:
1057:
1053:
1044:
1043:
1036:
1026:
1024:
1013:
1009:
978:
971:
962:
961:
954:
927:
923:
894:
890:
875:
874:
870:
861:
860:
856:
846:
844:
833:
832:
828:
818:
816:
807:
806:
802:
784:
769:
761:
757:
744:
743:
739:
731:
723:
719:
708:
704:
699:
694:
693:
656:
652:
647:
642:
633:Terrapin attack
627:Spoofing attack
520:
406:
354:
328:
265:
253:
235:
228:
224:
214:
210:
203:
193:
189:
183:
173:
167:
163:
153:
146:
142:
132:
128:
121:
91:
28:
25:
12:
11:
5:
1846:
1836:
1835:
1830:
1825:
1808:
1807:
1805:
1804:
1799:
1794:
1788:
1786:
1782:
1781:
1779:
1778:
1773:
1768:
1763:
1758:
1753:
1748:
1743:
1738:
1733:
1731:Anti-keylogger
1727:
1725:
1721:
1720:
1718:
1717:
1712:
1707:
1705:Mobile malware
1702:
1697:
1692:
1687:
1682:
1677:
1671:
1669:
1665:
1664:
1662:
1661:
1656:
1651:
1646:
1641:
1636:
1631:
1626:
1621:
1616:
1611:
1606:
1601:
1596:
1591:
1585:
1583:
1579:
1578:
1576:
1575:
1570:
1565:
1560:
1555:
1550:
1545:
1539:
1537:
1533:
1532:
1530:
1529:
1524:
1519:
1514:
1512:Computer virus
1509:
1503:
1501:
1497:
1496:
1488:
1487:
1480:
1473:
1465:
1459:
1458:
1443:
1442:External links
1440:
1437:
1436:
1418:
1385:
1378:
1348:
1329:
1302:
1268:
1240:
1214:
1195:
1180:
1147:
1126:
1117:
1085:(4): 294–299.
1069:
1051:
1034:
1007:
969:
952:
941:(4): 408–426.
921:
908:(5): 780–787.
888:
868:
854:
826:
800:
782:
755:
737:
717:
701:
700:
698:
695:
692:
691:
649:
648:
646:
643:
641:
640:
630:
624:
621:Secure channel
618:
612:
606:
600:
594:
588:
582:
579:Key management
576:
570:
564:
558:
552:
546:
540:
537:Babington Plot
534:
528:
521:
519:
516:
515:
514:
508:
502:
493:
487:
478:
472:
437:Xpress Browser
414:cellular phone
405:
402:
401:
400:
399:
398:
395:
392:
386:
380:
371:
368:
353:
350:
332:hash functions
327:
324:
270:secure channel
264:
263:Authentication
261:
252:
249:
244:
243:
240:
239:
238:
227:
219:
218:
217:
213:
198:
197:
196:
192:
178:
177:
176:
166:
158:
157:
156:
145:
137:
136:
135:
131:
90:
87:
60:communications
52:on-path attack
26:
9:
6:
4:
3:
2:
1845:
1834:
1831:
1829:
1826:
1824:
1821:
1820:
1818:
1803:
1800:
1798:
1795:
1793:
1790:
1789:
1787:
1783:
1777:
1774:
1772:
1769:
1767:
1764:
1762:
1759:
1757:
1754:
1752:
1749:
1747:
1744:
1742:
1739:
1737:
1734:
1732:
1729:
1728:
1726:
1722:
1716:
1713:
1711:
1708:
1706:
1703:
1701:
1698:
1696:
1695:MacOS malware
1693:
1691:
1690:Linux malware
1688:
1686:
1683:
1681:
1678:
1676:
1673:
1672:
1670:
1666:
1660:
1657:
1655:
1652:
1650:
1647:
1645:
1642:
1640:
1637:
1635:
1632:
1630:
1627:
1625:
1622:
1620:
1617:
1615:
1612:
1610:
1609:Form grabbing
1607:
1605:
1602:
1600:
1597:
1595:
1592:
1590:
1587:
1586:
1584:
1580:
1574:
1571:
1569:
1566:
1564:
1561:
1559:
1556:
1554:
1551:
1549:
1546:
1544:
1541:
1540:
1538:
1534:
1528:
1525:
1523:
1520:
1518:
1517:Computer worm
1515:
1513:
1510:
1508:
1505:
1504:
1502:
1498:
1493:
1486:
1481:
1479:
1474:
1472:
1467:
1466:
1463:
1456:
1452:
1449:
1446:
1445:
1432:
1428:
1422:
1406:
1402:
1401:
1396:
1389:
1381:
1375:
1371:
1367:
1363:
1359:
1352:
1344:
1340:
1333:
1317:
1313:
1306:
1291:
1287:
1283:
1279:
1272:
1257:
1256:
1251:
1244:
1228:
1224:
1218:
1210:
1206:
1199:
1191:
1187:
1183:
1177:
1173:
1169:
1165:
1158:
1151:
1142:
1137:
1130:
1121:
1114:
1110:
1106:
1102:
1098:
1093:
1088:
1084:
1080:
1073:
1065:
1061:
1055:
1047:
1041:
1039:
1022:
1018:
1011:
1003:
999:
995:
991:
987:
983:
976:
974:
965:
959:
957:
948:
944:
940:
936:
932:
925:
916:
911:
907:
903:
899:
892:
884:
883:
878:
872:
864:
858:
842:
841:
836:
830:
814:
810:
804:
797:
795:
791:
785:
779:
775:
768:
767:
759:
751:
747:
741:
730:
729:
721:
713:
706:
702:
688:
684:
680:
676:
672:
668:
664:
660:
654:
650:
638:
634:
631:
628:
625:
622:
619:
616:
613:
610:
607:
604:
601:
598:
595:
592:
589:
586:
583:
580:
577:
574:
571:
568:
565:
562:
559:
556:
555:Cryptanalysis
553:
550:
547:
544:
541:
538:
535:
532:
529:
526:
523:
522:
513:
509:
506:
503:
501:
497:
494:
491:
488:
486:
482:
479:
476:
473:
470:
467:
466:
465:
462:
460:
456:
454:
449:
446:
442:
441:proxy servers
438:
434:
429:
427:
423:
418:
415:
411:
396:
393:
391:
387:
385:
381:
378:
377:
375:
372:
369:
366:
365:
364:
362:
358:
349:
347:
343:
339:
335:
333:
323:
321:
317:
313:
311:
307:
305:
300:
298:
294:
290:
287:, may harden
286:
282:
277:
275:
271:
260:
258:
248:
241:
233:
223:
222:
220:
208:
202:
201:
199:
188:
182:
181:
179:
172:
162:
161:
159:
151:
141:
140:
138:
126:
120:
119:
117:
116:
115:
112:
109:. Meanwhile,
108:
104:
95:
86:
84:
80:
74:
72:
68:
67:eavesdropping
63:
61:
57:
53:
49:
45:
41:
37:
33:
23:
19:
1568:Trojan horse
1557:
1548:Clickjacking
1430:
1421:
1409:. Retrieved
1398:
1388:
1361:
1351:
1343:Fast Company
1342:
1332:
1320:. Retrieved
1316:the original
1305:
1293:. Retrieved
1281:
1271:
1259:. Retrieved
1253:
1243:
1231:. Retrieved
1226:
1217:
1208:
1198:
1163:
1150:
1129:
1120:
1112:
1082:
1078:
1072:
1063:
1054:
1027:November 25,
1025:. Retrieved
1021:the original
1010:
985:
981:
938:
934:
924:
905:
901:
891:
880:
871:
857:
845:. Retrieved
840:MDN Web Docs
838:
829:
817:. Retrieved
812:
803:
789:
787:
765:
758:
740:
727:
720:
705:
686:
682:
678:
674:
670:
666:
662:
658:
653:
525:ARP spoofing
463:
457:
450:
430:
426:certificates
419:
407:
355:
336:
329:
314:
308:
301:
278:
266:
254:
245:
231:
206:
187:
171:
149:
124:
100:
75:
64:
51:
47:
43:
39:
32:cryptography
29:
1700:Macro virus
1685:iOS malware
1659:Web threats
1619:Infostealer
1536:Concealment
1141:1311.7182v1
56:cyberattack
1817:Categories
1724:Protection
1639:Ransomware
1604:Fleeceware
697:References
496:Forcepoint
445:clear text
320:IP address
283:, such as
1649:Scareware
1599:Crimeware
1295:March 22,
1290:1059-1028
1255:Wired.com
1233:March 27,
1087:CiteSeerX
988:: 78–81.
882:Microsoft
847:August 1,
819:August 1,
689:) attack.
490:Superfish
459:Bluetooth
451:In 2017,
431:In 2013,
422:DigiNotar
1797:Honeypot
1756:Firewall
1543:Backdoor
1451:Archived
1431:TechSpot
1405:Archived
1322:June 13,
1261:June 23,
1190:18489395
1002:32996015
794:STARTTLS
518:See also
475:Fiddler2
101:Suppose
1654:Spyware
1563:Rootkit
1492:Malware
1109:6967714
788:When a
505:Comcast
492:malware
453:Equifax
390:revoked
229:Mallory
211:Mallory
190:Mallory
168:Mallory
147:Mallory
129:Mallory
111:Mallory
89:Example
54:, is a
1629:Malbot
1594:Botnet
1589:Adware
1494:topics
1411:May 8,
1376:
1288:
1209:liu.se
1188:
1178:
1107:
1089:
1000:
835:"MitM"
780:
681:), or
485:Google
469:DSniff
316:DNSSEC
48:attack
1282:Wired
1186:S2CID
1160:(PDF)
1136:arXiv
1105:S2CID
998:S2CID
770:(PDF)
732:(PDF)
645:Notes
510:2015
500:proxy
433:Nokia
412:is a
374:X.509
225:Alice
204:Alice
184:Alice
164:Alice
143:Alice
122:Alice
103:Alice
50:, or
1413:2024
1400:CNET
1374:ISBN
1324:2014
1297:2019
1286:ISSN
1263:2014
1235:2011
1176:ISBN
1029:2014
849:2022
821:2022
778:ISBN
687:AITM
679:PITM
304:ZRTP
44:MITM
38:, a
34:and
1366:doi
1168:doi
1097:doi
990:doi
943:doi
910:doi
637:ssh
481:NSA
435:'s
236:Bob
215:Bob
194:Bob
174:Bob
154:Bob
133:Bob
107:Bob
79:TLS
30:In
20:or
1819::
1429:.
1403:.
1397:.
1372:.
1360:.
1341:.
1284:.
1280:.
1252:.
1225:.
1207:.
1184:.
1174:.
1162:.
1111:.
1103:.
1095:.
1083:21
1081:.
1062:.
1037:^
996:.
984:.
972:^
955:^
939:16
937:.
933:.
906:50
904:.
900:.
879:.
837:.
811:.
786:.
772:.
748:.
673:,
669:,
665:,
661:,
408:A
348:.
322:.
279:A
85:.
46:)
1484:e
1477:t
1470:v
1415:.
1382:.
1368::
1345:.
1326:.
1299:.
1265:.
1237:.
1211:.
1192:.
1170::
1144:.
1138::
1099::
1066:.
1031:.
1004:.
992::
986:7
949:.
945::
918:.
912::
851:.
823:.
714:.
685:(
677:(
42:(
24:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.