512:, which can be subsequently accessed, for example, by typing in a secret key sequence. Hardware keyloggers do not require any software to be installed on a target user's computer, therefore not interfering with the computer's operation and less likely to be detected by software running on it. However, its physical presence may be detected if, for example, it is installed outside the case as an inline device between the computer and the keyboard. Some of these implementations can be controlled and monitored remotely using a wireless communication standard.
159:
151:
459:
2707:
2542:
467:
628:. What is not trivial for an attacker, however, is installing a covert keystroke logger without getting caught and downloading data that has been logged without being traced. An attacker that manually connects to a host machine to download logged keystrokes risks being traced. A trojan that sends keylogged data to a fixed e-mail address or
540:. The repetition frequency of similar acoustic keystroke signatures, the timings between different keyboard strokes and other context information such as the probable language in which the user is writing are used in this analysis to map sounds to letters. A fairly long recording (1000 or more keystrokes) is required so that a large enough
598:
percent accuracy. The technique involves working through probability by detecting pairs of keystrokes, rather than individual keys. It models "keyboard events" in pairs and then works out whether the pair of keys pressed is on the left or the right side of the keyboard and whether they are close together or far apart on the
1022:
Another very similar technique uses the fact that any selected text portion is replaced by the next key typed. e.g., if the password is "secret", one could type "s", then some dummy keys "asdf". These dummy characters could then be selected with the mouse, and the next character from the password "e"
755:
is a possible countermeasure against software keyloggers if the CD is clean of malware and the operating system contained on it is secured and fully patched so that it cannot be infected as soon as it is started. Booting a different operating system does not impact the use of a hardware or BIOS based
515:
Wireless keyboard and mouse sniffers: These passive sniffers collect packets of data being transferred from a wireless keyboard and its receiver. As encryption may be used to secure the wireless communications between the two devices, this may need to be cracked beforehand if the transmissions are to
928:
Keystroke interference software is also available. These programs attempt to trick keyloggers by introducing random keystrokes, although this simply results in the keylogger recording more information than it needs to. An attacker has the task of extracting the keystrokes of interest—the security of
870:
Another common way to protect access codes from being stolen by keystroke loggers is by asking users to provide a few randomly selected characters from their authentication code. For example, they might be asked to enter the 2nd, 5th, and 8th characters. Even if someone is watching the user or using
768:
applications can detect some software based keyloggers and quarantine, disable, or remove them. However, because many keylogging programs are legitimate pieces of software under some circumstances, anti-spyware often neglects to label keylogging programs as spyware or a virus. These applications can
586:
Physical evidence: For a keypad that is used only to enter a security code, the keys which are in actual use will have evidence of use from many fingerprints. A passcode of four digits, if the four digits in question are known, is reduced from 10,000 possibilities to just 24 possibilities (10 versus
420:
are taken to capture graphics-based information. Applications with screen logging abilities may take screenshots of the whole screen, of just one application, or even just around the mouse cursor. They may take these screenshots periodically or in response to user behaviors (for example, when a user
708:
The effectiveness of countermeasures varies because keyloggers use a variety of techniques to capture data and the countermeasure needs to be effective against the particular data capture technique. In the case of
Windows 10 keylogging by Microsoft, changing certain privacy settings may disable it.
610:
Body keyloggers: Body keyloggers track and analyze body movements to determine which keys were pressed. The attacker needs to be familiar with the keys layout of the tracked keyboard to correlate between body movements and keys position. Tracking audible signals of the user' interface (e.g. a sound
738:
specifically designed to detect keyloggers on a computer, typically comparing all files in the computer against a database of keyloggers, looking for similarities which might indicate the presence of a hidden keylogger. As anti-keyloggers have been designed specifically to detect keyloggers, they
1002:
Alternating between typing the login credentials and typing characters somewhere else in the focus window can cause a keylogger to record more information than it needs to, but this could be easily filtered out by an attacker. Similarly, a user can move their cursor using the mouse while typing,
507:
connector-based hardware keyloggers, as well as ones for laptop computers (the Mini-PCI card plugs into the expansion slot of a laptop). More stealthy implementations can be installed or built into standard keyboards so that no device is visible on the external cable. Both types log all keyboard
328:)-based keyloggers perform their logging function by altering the memory tables associated with the browser and other system functions. By patching the memory tables or injecting directly into memory, this technique can be used by malware authors to bypass Windows UAC (User Account Control). The
597:
found in smartphones. The attack is made possible by placing a smartphone near a keyboard on the same desk. The smartphone's accelerometer can then detect the vibrations created by typing on the keyboard and then translate this raw accelerometer signal into readable sentences with as much as 80
788:
No software-based anti-spyware application can be 100% effective against all keyloggers. Software-based anti-spyware cannot defeat non-software keyloggers (for example, hardware keyloggers attached to keyboards will always receive keystrokes before any software-based anti-spyware application).
989:
With the help of many programs, a seemingly meaningless text can be expanded to a meaningful text and most of the time context-sensitively, e.g. "en.wikipedia.org" can be expanded when a web browser window has the focus. The biggest weakness of this technique is that these programs send their
891:
in the face of a successful keylogging attack, as accessing protected information would require both the (hardware) security token as well as the appropriate password/passphrase. Knowing the keystrokes, mouse actions, display, clipboard, etc. used on one computer will not subsequently help an
866:
may prevent unauthorized access to an account which has had its login details exposed to an attacker via a keylogger, as each password is invalidated as soon as it is used. This solution may be useful for someone using a public computer. However, an attacker who has remote control over such a
796:
will defeat keyloggers with lower privileges. For example, a hook-based anti-spyware application cannot defeat a kernel-based keylogger (as the keylogger will receive the keystroke messages before the anti-spyware application), but it could potentially defeat hook- and API-based keyloggers.
602:
keyboard. Once it has worked this out, it compares the results to a preloaded dictionary where each word has been broken down in the same way. Similar techniques have also been shown to be effective at capturing keystrokes on touchscreen keyboards while in some cases, in combination with
842:, thereby reducing the possibility that private data is being recorded. However, someone with physical access to the machine may still be able to install software that can intercept this information elsewhere in the operating system or while in transit on the network. (
1026:
These techniques assume incorrectly that keystroke logging software cannot directly monitor the clipboard, the selected text in a form, or take a screenshot every time a keystroke or mouse click occurs. They may, however, be effective against some hardware keyloggers.
945:
software can also be used against keyloggers, since there are no typing or mouse movements involved. The weakest point of using voice-recognition software may be how the software sends the recognized text to target software after the user's speech has been processed.
531:
can be used to monitor the sound created by someone typing on a computer. Each key on the keyboard makes a subtly different acoustic signature when struck. It is then possible to identify which keystroke signature relates to which keyboard character via
523:
to capture people's PINs. Each keypress is registered by the keyboard of the ATM as well as the criminal's keypad that is placed over it. The device is designed to look like an integrated part of the machine so that bank customers are unaware of its
99:. Termed the "selectric bug", it measured the movements of the print head of IBM Selectric typewriters via subtle influences on the regional magnetic field caused by the rotation and movements of the print head. An early keylogger was written by
183:
has a built-in keylogger in its final version "to improve typing and writing services". However, malicious individuals can use keyloggers on public computers to steal passwords or credit card information. Most keyloggers are not stopped by
295:
submissions by recording the form data on submit events. This happens when the user completes a form and submits it, usually by clicking a button or pressing enter. This type of keylogger records form data before it is passed over the
739:
have the potential to be more effective than conventional antivirus software; some antivirus software do not consider keyloggers to be malware, as under some circumstances a keylogger can be considered a legitimate piece of software.
336:
trojans use this method exclusively. Non-Windows systems have protection mechanisms that allow access to locally recorded data from a remote location. Remote communication may be achieved when one of these methods is used:
1003:
causing the logged keystrokes to be in the wrong order e.g., by typing a password beginning with the last letter and then using the mouse to move the cursor for each subsequent letter. Lastly, someone can also use
640:
Researchers Adam Young and Moti Yung discussed several methods of sending keystroke logging. They presented a deniable password snatching attack in which the keystroke logging trojan is installed using a virus or
1413:
574:
Optical surveillance: Optical surveillance, while not a keylogger in the classical sense, is nonetheless an approach that can be used to capture passwords or PINs. A strategically placed camera, such as a hidden
372:
Since 2006, Keystroke logging has been an established research method for the study of writing processes. Different programs have been developed to collect online process data of writing activities, including
174:
organizations to troubleshoot technical problems with computers and business networks. Families and businesspeople use keyloggers legally to monitor network usage without their users' direct knowledge.
994:, i.e. sending mouse clicks to non-responsive areas of the target program, sending meaningless keys, sending another mouse click to the target area (e.g. password field) and switching back-and-forth.
1452:
808:(also known as reverse-firewalls) can be used to alert the user whenever an application attempts to make a network connection. This gives the user the chance to prevent the keylogger from "
1260:, "Today, keyloggers are mainly used to steal user data relating to various online payment systems, and virus writers are constantly writing new keylogger Trojans for this very purpose."
792:
The particular technique that the anti-spyware application uses will influence its potential effectiveness against software keyloggers. As a general rule, anti-spyware applications with
397:
Keystroke logging can be used to research writing, specifically. It can also be integrated into educational domains for second language learning, programming skills, and typing skills.
45:, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A
64:
While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other
2564:
611:
the device produce to informs the user that a keystroke was logged) may reduce the complexity of the body keylogging algorithms, as it marks the moment at which a key was pressed.
696:
to the US in an elaborate ruse, and captured their usernames and passwords with a keylogger that was covertly installed on a machine that they used to access their computers in
435:
allows programs to request the text 'value' in some controls. This means that some passwords may be captured, even if they are hidden behind password masks (usually asterisks).
405:
Software keyloggers may be augmented with features that capture user information without relying on keyboard key presses as the sole input. Some of these features include:
380:
Keystroke logging is used legitimately as a suitable research instrument in several writing contexts. These include studies on cognitive writing processes, which include
970:
use this principle by using mouse movements instead of a stylus. Mouse gesture programs convert these strokes to user-definable actions, such as typing text. Similarly,
920:) send normal keyboard event messages to the external target program to type text. Software key loggers can log these typed characters sent from one program to another.
238:
that subvert the operating system kernel to gain unauthorized access to the hardware. This makes them very powerful. A keylogger using this method can act as a keyboard
1410:
892:
attacker gain access to the protected resource. Some security tokens work as a type of hardware-assisted one-time password system, and others implement a cryptographic
154:
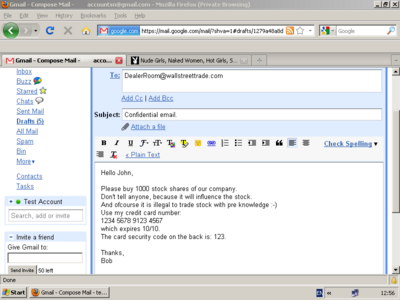
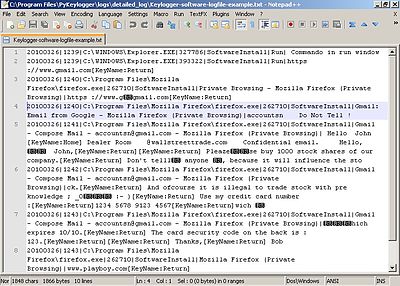
A keylogger example of a screen capture, which holds potentially confidential and private information. The image below holds the corresponding keylogger text result.
68:. Keystroke logging can also be utilized to monitor activities of children in schools or at home and by law enforcement officials to investigate malicious usage.
256:
inside a running application. The keylogger registers keystroke events as if it was a normal piece of the application instead of malware. The keylogger receives an
1665:
V. W. Berninger (Ed., 2012), Past, present, and future contributions of cognitive writing research to cognitive psychology. New York/Sussex: Taylor & Francis.
1556:"Bypassing pre-boot authentication passwords by instrumenting the BIOS keyboard buffer (practical low level attacks against x86 pre-boot authentication software)"
1656:
K.P.H. Sullivan & E. Lindgren (Eds., 2006), Studies in
Writing: Vol. 18. Computer Key-Stroke Logging and Writing: Methods and Applications. Oxford: Elsevier.
1498:
867:
computer can simply wait for the victim to enter their credentials before performing unauthorized transactions on their behalf while their session is active.
230:
to hide in the OS and intercepts keystrokes that pass through the kernel. This method is difficult both to write and to combat. Such keyloggers reside at the
103:
and posted to the Usenet newsgroup net.unix-wizards, net.sources on
November 17, 1983. The posting seems to be a motivating factor in restricting access to
1449:
826:
Automatic form-filling programs may prevent keylogging by removing the requirement for a user to type personal details and passwords using the keyboard.
1738:
1484:
1555:
551:
of a wired keyboard from up to 20 metres (66 ft) away, without being physically wired to it. In 2009, Swiss researchers tested 11 different
2601:
234:, which makes them difficult to detect, especially for user-mode applications that do not have root access. They are frequently implemented as
499:
Keyboard hardware: Hardware keyloggers are used for keystroke logging utilizing a hardware circuit that is attached somewhere in between the
361:
The software enables a remote login to the local machine from the
Internet or the local network, for data logs stored on the target machine.
593:
sensors: Researchers have demonstrated that it is possible to capture the keystrokes of nearby computer keyboards using only the commodity
496:
is required to the machine, and the software loaded into the BIOS needs to be created for the specific hardware that it will be running on.
3383:
1229:
716:
Keylogger program authors may be able to update their program's code to adapt to countermeasures that have proven effective against it.
1607:
1362:
192:
between computers; software-based keyloggers run on the affected user's computer, reading keyboard inputs directly as the user types.
3145:
2046:
Aviv, Adam J.; Sapp, Benjamin; Blaze, Matt; Smith, Jonathan M. (2012). "Practicality of accelerometer side channels on smartphones".
620:
Writing simple software applications for keylogging can be trivial, and like any nefarious computer program, can be distributed as a
2492:
709:
An on-screen keyboard will be effective against hardware keyloggers; transparency will defeat some—but not all—screen loggers. An
480:
Hardware-based keyloggers do not depend upon any software being installed as they exist at a hardware level in a computer system.
1431:
700:. The FBI then used these credentials to gain access to the suspects' computers in Russia to obtain evidence to prosecute them.
3235:
1683:
2360:
838:
information has been entered into the program, it will be automatically entered into forms without ever using the keyboard or
3122:
2277:
2226:
1958:
1291:
893:
271:, etc. are used to poll the state of the keyboard or to subscribe to keyboard events. A more recent example simply polls the
1011:
parts of the typed text without using the keyboard. An attacker who can capture only parts of a password will have a larger
119:
2445:
2111:. Proceedings of the fifth ACM conference on Security and Privacy in Wireless and Mobile Networks. ACM. pp. 113–124.
3153:
2134:. Proceedings of the 10th international conference on Mobile systems, applications, and services. ACM. pp. 323–336.
2157:. Proceedings of the 4th ACM Workshop on Security and Privacy in Smartphones & Mobile Devices. ACM. pp. 51–62.
170:
A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in
2594:
2546:
2470:
1253:
3500:
3191:
3085:
2063:
1670:
1509:
782:
432:
253:
2881:
2346:
2209:
Young, Adam; Yung, Moti (1997). "Deniable password snatching: On the possibility of evasive electronic espionage".
1764:
2570:
3388:
3135:
1872:
674:
2375:
1632:
1394:
384:
descriptions of writing strategies; the writing development of children (with and without writing difficulties),
242:, for example, and thus gain access to any information typed on the keyboard as it goes to the operating system.
3531:
3215:
901:
276:
76:
1742:
137:—apparently because they are immune to such bugs. As of 2013, Russian special services still use typewriters.
115:
program operated by locating and dumping character lists (clients) as they were assembled in the Unix kernel.
3454:
2948:
2587:
713:
application that can only disable hook-based keyloggers will be ineffective against kernel-based keyloggers.
492:
that handles keyboard events can be modified to record these events as they are processed. Physical and/or
3140:
3061:
2861:
1978:. Proceedings of the 18th ACM conference on Computer and communications security. ACM. pp. 561–562.
871:
a keystroke logger, they would only get a few characters from the code without knowing their positions.
2250:
Young, Adam; Yung, Moti (1996). "Cryptovirology: Extortion-based security threats and countermeasures".
1276:
2022 Fifth
International Conference on Computational Intelligence and Communication Technologies (CCICT)
3551:
3474:
3117:
3075:
2731:
2511:
955:
908:
where an attacker substitutes the card reader/PIN entry hardware for one which records the user's PIN.
17:
2407:"Anti-keylogging measures for secure Internet login: An example of the law of unintended consequences"
2406:
2327:
1562:
3342:
2978:
2696:
564:
548:
516:
be read. In some cases, this enables an attacker to type arbitrary commands into a victim's computer.
221:
2302:
1593:
1540:
438:
The recording of every program/folder/window opened including a screenshot of every website visited.
3276:
3266:
2963:
2841:
2736:
2260:
1935:
1857:
1817:
1081:
1012:
843:
793:
621:
580:
520:
315:
231:
65:
2080:
1934:
Maggi, Federico; Volpatto, Alberto; Gasparini, Simone; Boracchi, Giacomo; Zanero, Stefano (2011).
1839:
421:
clicks the mouse). Screen logging can be used to capture data inputted with an on-screen keyboard.
3352:
3051:
3003:
2666:
1041:
2303:"Mafia trial to test FBI spying tactics: Keystroke logging used to spy on mob suspect using PGP"
449:
conversations, FTP downloads and other
Internet-based activities (including the bandwidth used).
302:
A malicious script tag is injected into a targeted web page, and listens for key events such as
209:
running underneath the operating system, which thus remains untouched. It effectively becomes a
3403:
3230:
2255:
1714:
528:
341:
171:
134:
3337:
1945:. 7th International Conference on Information Assurance and Security. IEEE. pp. 320–325.
1328:
1315:
3541:
3184:
3092:
2826:
2130:
Miluzzo, Emiliano; Varshavsky, Alexander; Balakrishnan, Suhrid; Choudhury, Romit Roy (2012).
2050:. Proceedings of the 28th Annual Computer Security Applications Conference. ACM. p. 41.
1580:
1527:
1233:
1046:
556:
2391:
2027:. Proceedings of the Thirteenth Workshop on Mobile Computing Systems and Applications. ACM.
1469:
3510:
3505:
3464:
3393:
3251:
3112:
3024:
2973:
2918:
2786:
2759:
2741:
2639:
2610:
1890:
Martin
Vuagnoux and Sylvain Pasini (2009-06-01). Vuagnoux, Martin; Pasini, Sylvain (eds.).
1370:
1008:
839:
685:
552:
504:
410:
307:
214:
2706:
2187:
1813:
8:
3546:
3459:
2896:
2671:
2629:
2496:
2109:
TapLogger: inferring user inputs on smartphone touchscreens using on-board motion sensors
1997:
905:
834:
to fill in checkout pages and log users into their accounts. Once the user's account and
678:
576:
541:
42:
3444:
3281:
3261:
3080:
3008:
2913:
2518:
2283:
2232:
2158:
2048:
Proceedings of the 28th Annual
Computer Security Applications Conference on - ACSAC '12
1976:(sp)iPhone: decoding vibrations from nearby keyboards using mobile phone accelerometers
1297:
1199:
1140:
1066:
1061:
1016:
942:
805:
587:
4! ). These could then be used on separate occasions for a manual "brute force attack".
537:
503:
and the computer, typically inline with the keyboard's cable connector. There are also
475:
325:
311:
72:
3469:
3423:
3128:
2821:
2771:
2718:
2676:
2624:
2426:
2273:
2222:
2059:
1954:
1666:
1301:
1287:
1203:
1191:
1186:
1132:
1056:
981:
The same potential weakness of speech recognition applies to this technique as well.
896:, which can improve security in a manner conceptually similar to one time passwords.
863:
500:
446:
429:
257:
158:
58:
2287:
2236:
1691:
1485:"Microsoft Windows 10 has a keylogger enabled by default – here's how to disable it"
3536:
3484:
3449:
3177:
3097:
3037:
2801:
2791:
2686:
2418:
2387:
2265:
2214:
2168:
2135:
2112:
2051:
2028:
1979:
1946:
1279:
1181:
1171:
1144:
1124:
1086:
568:
563:
and found them all vulnerable, primarily because of the prohibitive cost of adding
560:
442:
150:
100:
1283:
990:
keystrokes directly to the target program. However, this can be overcome by using
3479:
3418:
3322:
2988:
2968:
2866:
2691:
2681:
2559:
1891:
1456:
1417:
1158:
Conijn, Rianne; Cook, Christine; van Zaanen, Menno; Van Waes, Luuk (2021-08-24).
971:
959:
847:
689:
645:. An attacker who is caught with the virus or worm can claim to be a victim. The
571:
to tune into the specific frequency of the emissions radiated from the keyboards.
509:
210:
189:
1909:
133:
Soviet embassies used manual typewriters, rather than electric typewriters, for
3439:
3413:
3220:
3158:
3056:
2906:
2856:
2831:
2796:
2776:
2656:
2644:
2422:
2269:
2218:
1950:
1505:
1272:"A Systematic Review of Encryption and Keylogging for Computer System Security"
1271:
1216:
1176:
1159:
1112:
1071:
1036:
967:
884:
731:
725:
625:
329:
260:
each time the user presses or releases a key. The keylogger simply records it.
978:
can be used to input these gestures, however, these are becoming less common.
3525:
3398:
3317:
3225:
3068:
3029:
2998:
2993:
2846:
2836:
2806:
2555:
2430:
1943:
2011 7th
International Conference on Information Assurance and Security (IAS)
1790:
1342:
1316:
Robustness of keystroke-dynamics based biometrics against synthetic forgeries
1195:
1136:
1128:
930:
888:
693:
658:
642:
594:
348:
333:
288:
239:
2211:
Proceedings. 1997 IEEE Symposium on
Security and Privacy (Cat. No.97CB36097)
2172:
2139:
2116:
2088:. Proceedings of the 6th USENIX conference on Hot topics in security. USENIX
2055:
2032:
1983:
3256:
3102:
2958:
2661:
2023:
Owusu, Emmanuel; Han, Jun; Das, Sauvik; Perrig, Adrian; Zhang, Joy (2012).
1974:
Marquardt, Philip; Verma, Arunabh; Carter, Henry; Traynor, Patrick (2011).
1091:
1004:
851:
809:
765:
710:
646:
92:
3408:
3327:
3042:
2876:
2851:
2816:
2651:
2405:
Goring, Stuart P.; Rabaiotti, Joseph R.; Jones, Antonia J. (2007-09-01).
1892:"Compromising Electromagnetic Emanations of Wired and Wireless Keyboards"
963:
916:
Most on-screen keyboards (such as the on-screen keyboard that comes with
897:
835:
831:
827:
821:
519:
Keyboard overlays: Criminals have been known to use keyboard overlays on
458:
185:
2082:
TouchLogger: inferring keystrokes on touch screen from smartphone motion
1768:
3367:
3347:
3312:
3107:
2923:
2871:
2754:
2634:
2579:
1608:"Web-Based Keylogger Used to Steal Credit Card Data from Popular Sites"
1051:
917:
880:
774:
770:
681:
654:
650:
629:
590:
533:
425:
417:
292:
206:
180:
96:
2512:"How To Login From an Internet Cafe Without Worrying About Keyloggers"
2129:
1429:
1270:
Rai, Swarnima; Choubey, Vaaruni; Suryansh; Garg, Puneet (2022-07-08).
3357:
3307:
2983:
2938:
2933:
2781:
2749:
1718:
975:
604:
493:
227:
176:
127:
112:
1858:"Researchers recover typed text using audio recording of keystrokes"
649:
asymmetrically encrypts the pilfered login/password pairs using the
2943:
2901:
2764:
2155:
PIN Skimming: Exploiting the Ambient-Light Sensor in Mobile Devices
1840:"Cracking Passwords using Keyboard Acoustics and Language Modeling"
752:
735:
489:
374:
355:
80:
54:
2163:
1889:
1450:"Russian security agency to buy typewriters to avoid surveillance"
846:(TLS) reduces the risk that data in transit may be intercepted by
166:
from a software-based keylogger, based on the screen capture above
3362:
3271:
3200:
3169:
2953:
2928:
2891:
2509:
2025:
ACCessory: password inference using accelerometers on smartphones
1076:
904:
entry may be vulnerable to keystroke logging through a so-called
778:
748:
249:
235:
203:
163:
1395:"Russia Turns To Typewriters To Protect Against Cyber Espionage"
962:
can already convert pen (also called stylus) movements on their
583:, can allow a criminal to watch a PIN or password being entered.
367:
3302:
3297:
2811:
2726:
2574:
2541:
697:
662:
599:
123:
79:. Numerous keylogging methods exist, ranging from hardware and
1933:
306:. Scripts can be injected via a variety of methods, including
1164:
International Journal of Artificial Intelligence in Education
1160:"Early prediction of writing quality using keystroke logging"
949:
466:
1157:
195:
From a technical perspective, there are several categories:
41:, is the action of recording (logging) the keys struck on a
1973:
1432:"Wanted: 20 electric typewriters for Russia to avoid leaks"
653:
of the trojan author and covertly broadcasts the resulting
485:
272:
108:
2446:"Organized crime tampers with European card swipe devices"
1363:"Soviet Spies Bugged World's First Electronic Typewriters"
1111:
Nyang, DaeHun; Mohaisen, Aziz; Kang, Jeonil (2014-11-01).
393:
specialist skill areas such as translation and subtitling.
1254:
Keyloggers: How they work and how to detect them (Part 1)
547:
Electromagnetic emissions: It is possible to capture the
2347:"3 methods to disable Windows 10 built-in Spy Keylogger"
409:
Clipboard logging. Anything that has been copied to the
2376:"The strange world of keyloggers - an overview, Part I"
2252:
Proceedings 1996 IEEE Symposium on Security and Privacy
1998:"iPhone Accelerometer Could Spy on Computer Keystrokes"
1430:
Agence France-Presse, Associated Press (13 July 2013).
118:
In the 1970s, spies installed keystroke loggers in the
1269:
1217:
Use of legal software products for computer monitoring
1113:"Keylogging-Resistant Visual Authentication Protocols"
929:
this mechanism, specifically how well it stands up to
769:
detect software-based keyloggers based on patterns in
661:
encoded and posted to a public bulletin board such as
95:
developed and deployed a hardware keylogger targeting
1314:
Stefan, Deian, Xiaokui Shu, and Danfeng Daphne Yao. "
759:
567:
during manufacture. The researchers used a wide-band
2490:
2404:
692:. Also in 2000, the FBI lured two suspected Russian
1023:typed, which replaces the dummy characters "asdf".
2045:
1936:"A fast eavesdropping attack against touchscreens"
1873:"A Year Ago: Cypherpunks publish proof of Tempest"
923:
358:transmitted employing an attached hardware system.
2471:"Prevent keyloggers from grabbing your passwords"
2022:
1896:Proceedings of the 18th Usenix Security Symposium
1553:
1318:." computers & security 31.1 (2012): 109-121.
1110:
815:
27:Action of recording the keys struck on a keyboard
3523:
2510:Cormac Herley and Dinei Florencio (2006-02-06).
991:
966:to computer understandable text successfully.
347:Data is periodically emailed to a pre-defined
340:Data is uploaded to a website, database or an
202:: The keylogger can theoretically reside in a
3185:
2595:
2443:
2132:Tapprints: your finger taps have fingerprints
1612:Threatpost | The first stop for security news
1411:"Learning from the Enemy: The GUNMAN Project"
368:Keystroke logging in writing process research
83:-based approaches to acoustic cryptanalysis.
1837:
1389:
1387:
984:
777:and keylogger behaviors (such as the use of
657:. They mentioned that the ciphertext can be
453:
145:
2325:
2300:
1855:
1811:
1633:"SpyEye Targets Opera, Google Chrome Users"
992:the 'alternating' technique described below
857:
140:
130:II and Selectric III electric typewriters.
3192:
3178:
2602:
2588:
2468:
2373:
1767:. SpyReveal Anti Keylogger. Archived from
1482:
950:Handwriting recognition and mouse gestures
3146:Security information and event management
2344:
2259:
2249:
2208:
2162:
2152:
1681:
1405:
1403:
1384:
1185:
1175:
424:Programmatically capturing the text in a
2609:
2106:
465:
457:
318:, or a compromise of the remote website.
157:
149:
2392:10.2352/ISSN.2470-1173.2017.6.MOBMU-313
2185:
2107:Xu, Zhi; Bai, Kun; Zhu, Sencun (2012).
2078:
279:that have not been cleared from memory.
14:
3524:
3236:Timeline of computer viruses and worms
2495:. Networkintercept.com. Archived from
2328:"Russians accuse FBI Agent of Hacking"
1684:"Keystroke Logging in SpyWareLoop.com"
1561:. www.ivizsecurity.com. Archived from
1400:
1015:to attack if they choose to execute a
911:
390:first and second language writing, and
188:encryption because that only protects
3173:
3123:Host-based intrusion detection system
2583:
1712:
1499:"The Evolution of Malicious IRC Bots"
1232:. Oxford dictionaries. Archived from
1117:IEEE Transactions on Mobile Computing
936:
71:Keylogging can also be used to study
2202:
470:A connected hardware-based keylogger
3154:Runtime application self-protection
2491:Christopher Ciabarra (2009-06-10).
1675:
1508:. 2005-11-26: 23–24. Archived from
997:
800:
677:used FlashCrest iSpy to obtain the
400:
226:: A program on the machine obtains
24:
3199:
2705:
1870:
874:
760:Anti-spyware / Anti-virus programs
719:
703:
377:, Scriptlog, Translog and GGXLog.
25:
3563:
3501:Computer and network surveillance
3086:Security-focused operating system
2535:
2374:Creutzburg, Reiner (2017-01-29).
1856:Sarah Young (14 September 2005).
1741:. Digital Society. Archived from
900:and their associated keypads for
894:challenge–response authentication
607:or with the ambient-light sensor.
2882:Insecure direct object reference
2540:
1814:"Tampered Credit Card Terminals"
1554:Jonathan Brossard (2008-09-03).
941:Similar to on-screen keyboards,
812:" with their typed information.
668:
3136:Information security management
2503:
2484:
2462:
2437:
2398:
2367:
2353:
2338:
2319:
2294:
2243:
2179:
2146:
2123:
2100:
2072:
2039:
2016:
1990:
1967:
1927:
1902:
1883:
1864:
1849:
1831:
1805:
1783:
1757:
1731:
1706:
1659:
1650:
1625:
1600:
1547:
1491:
1476:
1462:
1442:
1423:
1355:
924:Keystroke interference software
747:Rebooting the computer using a
559:and laptop keyboards in a semi-
413:can be captured by the program.
3216:Comparison of computer viruses
2079:Cai, Liang; Chen, Hao (2011).
1343:"The Security Digest Archives"
1335:
1321:
1308:
1263:
1247:
1222:
1210:
1151:
1104:
816:Automatic form filler programs
742:
13:
1:
3455:Data loss prevention software
1284:10.1109/CCiCT56684.2022.00039
1097:
887:may improve security against
632:risks exposing the attacker.
126:. They installed the bugs in
2444:Austin Modine (2008-10-10).
275:for pre-boot authentication
7:
3141:Information risk management
3062:Multi-factor authentication
2618:Related security categories
2192:Hakin9 IT Security Magazine
2153:Spreitzer, Raphael (2014).
1838:Andrew Kelly (2010-09-10).
1030:
830:are primarily designed for
615:
122:and Consulate buildings in
10:
3568:
3475:Intrusion detection system
3118:Intrusion detection system
3076:Computer security software
2732:Advanced persistent threat
2423:10.1016/j.cose.2007.05.003
2326:John Leyden (2002-08-16).
2301:John Leyden (2000-12-06).
2270:10.1109/SECPRI.1996.502676
2219:10.1109/SECPRI.1997.601339
1951:10.1109/ISIAS.2011.6122840
1812:Jeremy Kirk (2008-12-16).
1793:. SpyReveal Anti Keylogger
1682:Vincentas (11 July 2013).
1278:. IEEE. pp. 157–163.
1177:10.1007/s40593-021-00268-w
819:
723:
635:
473:
462:A hardware-based keylogger
86:
77:human-computer interaction
3493:
3432:
3376:
3343:Privacy-invasive software
3290:
3244:
3208:
3017:
2717:
2703:
2697:Digital rights management
2617:
2469:Scott Dunn (2009-09-10).
2361:"What is Anti Keylogger?"
1860:. UC Berkeley NewsCenter.
1483:Caleb Chen (2017-03-20).
1187:10067/1801420151162165141
985:Macro expanders/recorders
943:speech-to-text conversion
549:electromagnetic emissions
454:Hardware-based keyloggers
146:Software-based keyloggers
2842:Denial-of-service attack
2737:Arbitrary code execution
2411:Computers & Security
2345:Alex Stim (2015-10-28).
1129:10.1109/TMC.2014.2307331
858:One-time passwords (OTP)
844:Transport Layer Security
217:is a conceptual example.
141:Application of keylogger
66:confidential information
3353:Rogue security software
3052:Computer access control
3004:Rogue security software
2667:Electromagnetic warfare
2565:considered for deletion
2173:10.1145/2666620.2666622
2140:10.1145/2307636.2307666
2117:10.1145/2185448.2185465
2056:10.1145/2420950.2420957
2033:10.1145/2162081.2162095
1984:10.1145/2046707.2046771
1042:Black-bag cryptanalysis
33:, often referred to as
3389:Classic Mac OS viruses
3231:List of computer worms
3098:Obfuscation (software)
2827:Browser Helper Objects
2711:
1715:"EM_GETLINE Message()"
1588:Cite journal requires
1535:Cite journal requires
1470:"What is a Keylogger?"
529:Acoustic cryptanalysis
471:
463:
443:search engines queries
322:Memory-injection-based
291:-based keyloggers log
167:
155:
135:classified information
91:In the mid-1970s, the
3532:Cryptographic attacks
3093:Data-centric security
2974:Remote access trojans
2709:
2549:at Wikimedia Commons
2186:Hameiri, Paz (2019).
1739:"Apple keyboard hack"
1047:Computer surveillance
527:Acoustic keyloggers:
469:
461:
269:GetForegroundWindow()
263:Windows APIs such as
179:publicly stated that
161:
153:
3511:Operation: Bot Roast
3025:Application security
2919:Privilege escalation
2787:Cross-site scripting
2640:Cybersex trafficking
2611:Information security
2254:. pp. 129–140.
2213:. pp. 224–235.
1393:Geoffrey Ingersoll.
1009:cut, copy, and paste
686:Nicodemo Scarfo, Jr.
324:: Memory Injection (
308:cross-site scripting
3460:Defensive computing
3377:By operating system
2672:Information warfare
2630:Automotive security
1791:"Keylogger Removal"
1765:"Keylogger Removal"
912:On-screen keyboards
906:supply chain attack
751:or write-protected
577:surveillance camera
534:statistical methods
285:Form grabbing based
248:: These keyloggers
3445:Antivirus software
3291:Malware for profit
3262:Man-in-the-browser
3209:Infectious malware
3081:Antivirus software
2949:Social engineering
2914:Polymorphic engine
2867:Fraudulent dialers
2772:Hardware backdoors
2712:
2519:Microsoft Research
2380:Electronic Imaging
1694:on 7 December 2013
1455:2013-12-21 at the
1416:2017-12-03 at the
1409:Sharon A. Maneki.
1067:Reverse connection
1062:Hardware keylogger
1017:brute-force attack
937:Speech recognition
864:one-time passwords
688:, son of mob boss
659:steganographically
538:frequency analysis
508:activity to their
476:Hardware keylogger
472:
464:
312:man-in-the-browser
265:GetAsyncKeyState()
168:
156:
73:keystroke dynamics
47:keystroke recorder
39:keyboard capturing
3552:Security breaches
3519:
3518:
3470:Internet security
3424:HyperCard viruses
3333:Keystroke logging
3323:Fraudulent dialer
3267:Man-in-the-middle
3167:
3166:
3129:Anomaly detection
3034:Secure by default
2887:Keystroke loggers
2822:Drive-by download
2710:vectorial version
2677:Internet security
2625:Computer security
2547:Keystroke logging
2545:Media related to
2473:. Windows Secrets
2363:. 23 August 2018.
2279:978-0-8186-7417-4
2228:978-0-8186-7828-8
2188:"Body Keylogging"
2004:. 19 October 2011
1960:978-1-4577-2155-7
1916:. 19 January 2004
1745:on 26 August 2009
1637:Krebs on Security
1515:on March 15, 2006
1293:978-1-6654-7224-1
1123:(11): 2566–2579.
1057:Digital footprint
898:Smartcard readers
794:higher privileges
501:computer keyboard
494:root-level access
447:instant messenger
441:The recording of
430:Microsoft Windows
316:man-in-the-middle
300:JavaScript-based:
31:Keystroke logging
16:(Redirected from
3559:
3485:Network security
3450:Browser security
3194:
3187:
3180:
3171:
3170:
3038:Secure by design
2969:Hardware Trojans
2802:History sniffing
2792:Cross-site leaks
2687:Network security
2604:
2597:
2590:
2581:
2580:
2568:
2544:
2529:
2528:
2526:
2525:
2516:
2507:
2501:
2500:
2493:"Anti Keylogger"
2488:
2482:
2481:
2479:
2478:
2466:
2460:
2459:
2457:
2456:
2441:
2435:
2434:
2402:
2396:
2395:
2371:
2365:
2364:
2357:
2351:
2350:
2342:
2336:
2335:
2323:
2317:
2316:
2314:
2313:
2298:
2292:
2291:
2263:
2247:
2241:
2240:
2206:
2200:
2199:
2183:
2177:
2176:
2166:
2150:
2144:
2143:
2127:
2121:
2120:
2104:
2098:
2097:
2095:
2093:
2087:
2076:
2070:
2069:
2043:
2037:
2036:
2020:
2014:
2013:
2011:
2009:
1994:
1988:
1987:
1971:
1965:
1964:
1940:
1931:
1925:
1924:
1922:
1921:
1906:
1900:
1899:
1887:
1881:
1880:
1868:
1862:
1861:
1853:
1847:
1846:
1844:
1835:
1829:
1828:
1826:
1825:
1809:
1803:
1802:
1800:
1798:
1787:
1781:
1780:
1778:
1776:
1771:on 29 April 2011
1761:
1755:
1754:
1752:
1750:
1735:
1729:
1728:
1726:
1725:
1710:
1704:
1703:
1701:
1699:
1690:. Archived from
1679:
1673:
1663:
1657:
1654:
1648:
1647:
1645:
1643:
1629:
1623:
1622:
1620:
1619:
1604:
1598:
1597:
1591:
1586:
1584:
1576:
1574:
1573:
1567:
1560:
1551:
1545:
1544:
1538:
1533:
1531:
1523:
1521:
1520:
1514:
1503:
1495:
1489:
1488:
1480:
1474:
1473:
1466:
1460:
1448:Anna Arutunyan.
1446:
1440:
1439:
1427:
1421:
1407:
1398:
1391:
1382:
1381:
1379:
1378:
1369:. Archived from
1359:
1353:
1352:
1350:
1349:
1339:
1333:
1332:
1325:
1319:
1312:
1306:
1305:
1267:
1261:
1251:
1245:
1244:
1242:
1241:
1226:
1220:
1214:
1208:
1207:
1189:
1179:
1155:
1149:
1148:
1108:
1087:Virtual keyboard
998:Deceptive typing
972:graphics tablets
848:network sniffers
806:Network monitors
801:Network monitors
624:or as part of a
561:anechoic chamber
484:Firmware-based:
416:Screen logging.
401:Related features
305:
270:
266:
200:Hypervisor-based
106:
101:Perry Kivolowitz
21:
3567:
3566:
3562:
3561:
3560:
3558:
3557:
3556:
3522:
3521:
3520:
3515:
3494:Countermeasures
3489:
3480:Mobile security
3428:
3419:Palm OS viruses
3384:Android malware
3372:
3286:
3282:Zombie computer
3240:
3204:
3198:
3168:
3163:
3013:
2713:
2701:
2692:Copy protection
2682:Mobile security
2613:
2608:
2553:
2538:
2533:
2532:
2523:
2521:
2514:
2508:
2504:
2489:
2485:
2476:
2474:
2467:
2463:
2454:
2452:
2442:
2438:
2403:
2399:
2372:
2368:
2359:
2358:
2354:
2343:
2339:
2324:
2320:
2311:
2309:
2299:
2295:
2280:
2248:
2244:
2229:
2207:
2203:
2184:
2180:
2151:
2147:
2128:
2124:
2105:
2101:
2091:
2089:
2085:
2077:
2073:
2066:
2044:
2040:
2021:
2017:
2007:
2005:
1996:
1995:
1991:
1972:
1968:
1961:
1938:
1932:
1928:
1919:
1917:
1908:
1907:
1903:
1888:
1884:
1869:
1865:
1854:
1850:
1842:
1836:
1832:
1823:
1821:
1810:
1806:
1796:
1794:
1789:
1788:
1784:
1774:
1772:
1763:
1762:
1758:
1748:
1746:
1737:
1736:
1732:
1723:
1721:
1711:
1707:
1697:
1695:
1680:
1676:
1664:
1660:
1655:
1651:
1641:
1639:
1631:
1630:
1626:
1617:
1615:
1606:
1605:
1601:
1589:
1587:
1578:
1577:
1571:
1569:
1565:
1558:
1552:
1548:
1536:
1534:
1525:
1524:
1518:
1516:
1512:
1501:
1497:
1496:
1492:
1481:
1477:
1468:
1467:
1463:
1457:Wayback Machine
1447:
1443:
1428:
1424:
1418:Wayback Machine
1408:
1401:
1392:
1385:
1376:
1374:
1361:
1360:
1356:
1347:
1345:
1341:
1340:
1336:
1329:"Selectric bug"
1327:
1326:
1322:
1313:
1309:
1294:
1268:
1264:
1252:
1248:
1239:
1237:
1228:
1227:
1223:
1219:, keylogger.org
1215:
1211:
1156:
1152:
1109:
1105:
1100:
1033:
1000:
987:
952:
939:
926:
914:
885:security tokens
877:
875:Security tokens
860:
824:
818:
803:
771:executable code
762:
745:
728:
722:
720:Anti-keyloggers
706:
704:Countermeasures
690:Nicodemo Scarfo
671:
638:
618:
510:internal memory
478:
456:
403:
370:
303:
268:
264:
211:virtual machine
190:data in transit
148:
143:
104:
89:
28:
23:
22:
15:
12:
11:
5:
3565:
3555:
3554:
3549:
3544:
3539:
3534:
3517:
3516:
3514:
3513:
3508:
3503:
3497:
3495:
3491:
3490:
3488:
3487:
3482:
3477:
3472:
3467:
3462:
3457:
3452:
3447:
3442:
3440:Anti-keylogger
3436:
3434:
3430:
3429:
3427:
3426:
3421:
3416:
3414:Mobile malware
3411:
3406:
3401:
3396:
3391:
3386:
3380:
3378:
3374:
3373:
3371:
3370:
3365:
3360:
3355:
3350:
3345:
3340:
3335:
3330:
3325:
3320:
3315:
3310:
3305:
3300:
3294:
3292:
3288:
3287:
3285:
3284:
3279:
3274:
3269:
3264:
3259:
3254:
3248:
3246:
3242:
3241:
3239:
3238:
3233:
3228:
3223:
3221:Computer virus
3218:
3212:
3210:
3206:
3205:
3197:
3196:
3189:
3182:
3174:
3165:
3164:
3162:
3161:
3159:Site isolation
3156:
3151:
3150:
3149:
3143:
3133:
3132:
3131:
3126:
3115:
3110:
3105:
3100:
3095:
3090:
3089:
3088:
3083:
3073:
3072:
3071:
3066:
3065:
3064:
3057:Authentication
3049:
3048:
3047:
3046:
3045:
3035:
3032:
3021:
3019:
3015:
3014:
3012:
3011:
3006:
3001:
2996:
2991:
2986:
2981:
2976:
2971:
2966:
2961:
2956:
2951:
2946:
2941:
2936:
2931:
2926:
2921:
2916:
2911:
2910:
2909:
2899:
2894:
2889:
2884:
2879:
2874:
2869:
2864:
2859:
2857:Email spoofing
2854:
2849:
2844:
2839:
2834:
2829:
2824:
2819:
2814:
2809:
2804:
2799:
2797:DOM clobbering
2794:
2789:
2784:
2779:
2777:Code injection
2774:
2769:
2768:
2767:
2762:
2757:
2752:
2744:
2739:
2734:
2729:
2723:
2721:
2715:
2714:
2704:
2702:
2700:
2699:
2694:
2689:
2684:
2679:
2674:
2669:
2664:
2659:
2657:Cyberterrorism
2654:
2649:
2648:
2647:
2645:Computer fraud
2642:
2632:
2627:
2621:
2619:
2615:
2614:
2607:
2606:
2599:
2592:
2584:
2578:
2577:
2537:
2536:External links
2534:
2531:
2530:
2502:
2499:on 2010-06-26.
2483:
2461:
2436:
2417:(6): 421–426.
2397:
2386:(6): 139–148.
2366:
2352:
2337:
2318:
2293:
2278:
2261:10.1.1.44.9122
2242:
2227:
2201:
2178:
2145:
2122:
2099:
2071:
2064:
2038:
2015:
1989:
1966:
1959:
1926:
1914:www.snopes.com
1901:
1882:
1871:Knight, Will.
1863:
1848:
1830:
1804:
1782:
1756:
1730:
1705:
1674:
1658:
1649:
1624:
1599:
1590:|journal=
1546:
1537:|journal=
1490:
1475:
1461:
1441:
1422:
1399:
1383:
1354:
1334:
1320:
1307:
1292:
1262:
1246:
1221:
1209:
1170:(4): 835–866.
1150:
1102:
1101:
1099:
1096:
1095:
1094:
1089:
1084:
1079:
1074:
1072:Session replay
1069:
1064:
1059:
1054:
1049:
1044:
1039:
1037:Anti-keylogger
1032:
1029:
999:
996:
986:
983:
968:Mouse gestures
951:
948:
938:
935:
933:, is unclear.
925:
922:
913:
910:
889:replay attacks
876:
873:
859:
856:
820:Main article:
817:
814:
802:
799:
761:
758:
744:
741:
734:is a piece of
732:anti-keylogger
726:Anti-keylogger
724:Main article:
721:
718:
705:
702:
694:cybercriminals
670:
667:
637:
634:
617:
614:
613:
612:
608:
588:
584:
572:
545:
525:
517:
513:
497:
474:Main article:
455:
452:
451:
450:
439:
436:
422:
414:
402:
399:
395:
394:
391:
388:
385:
369:
366:
365:
364:
363:
362:
359:
352:
345:
319:
297:
282:
281:
280:
243:
218:
147:
144:
142:
139:
88:
85:
53:can be either
26:
9:
6:
4:
3:
2:
3564:
3553:
3550:
3548:
3545:
3543:
3540:
3538:
3535:
3533:
3530:
3529:
3527:
3512:
3509:
3507:
3504:
3502:
3499:
3498:
3496:
3492:
3486:
3483:
3481:
3478:
3476:
3473:
3471:
3468:
3466:
3463:
3461:
3458:
3456:
3453:
3451:
3448:
3446:
3443:
3441:
3438:
3437:
3435:
3431:
3425:
3422:
3420:
3417:
3415:
3412:
3410:
3407:
3405:
3404:MacOS malware
3402:
3400:
3399:Linux malware
3397:
3395:
3392:
3390:
3387:
3385:
3382:
3381:
3379:
3375:
3369:
3366:
3364:
3361:
3359:
3356:
3354:
3351:
3349:
3346:
3344:
3341:
3339:
3336:
3334:
3331:
3329:
3326:
3324:
3321:
3319:
3318:Form grabbing
3316:
3314:
3311:
3309:
3306:
3304:
3301:
3299:
3296:
3295:
3293:
3289:
3283:
3280:
3278:
3275:
3273:
3270:
3268:
3265:
3263:
3260:
3258:
3255:
3253:
3250:
3249:
3247:
3243:
3237:
3234:
3232:
3229:
3227:
3226:Computer worm
3224:
3222:
3219:
3217:
3214:
3213:
3211:
3207:
3202:
3195:
3190:
3188:
3183:
3181:
3176:
3175:
3172:
3160:
3157:
3155:
3152:
3147:
3144:
3142:
3139:
3138:
3137:
3134:
3130:
3127:
3124:
3121:
3120:
3119:
3116:
3114:
3111:
3109:
3106:
3104:
3101:
3099:
3096:
3094:
3091:
3087:
3084:
3082:
3079:
3078:
3077:
3074:
3070:
3069:Authorization
3067:
3063:
3060:
3059:
3058:
3055:
3054:
3053:
3050:
3044:
3041:
3040:
3039:
3036:
3033:
3031:
3030:Secure coding
3028:
3027:
3026:
3023:
3022:
3020:
3016:
3010:
3007:
3005:
3002:
3000:
2999:SQL injection
2997:
2995:
2992:
2990:
2987:
2985:
2982:
2980:
2979:Vulnerability
2977:
2975:
2972:
2970:
2967:
2965:
2964:Trojan horses
2962:
2960:
2959:Software bugs
2957:
2955:
2952:
2950:
2947:
2945:
2942:
2940:
2937:
2935:
2932:
2930:
2927:
2925:
2922:
2920:
2917:
2915:
2912:
2908:
2905:
2904:
2903:
2900:
2898:
2895:
2893:
2890:
2888:
2885:
2883:
2880:
2878:
2875:
2873:
2870:
2868:
2865:
2863:
2860:
2858:
2855:
2853:
2850:
2848:
2847:Eavesdropping
2845:
2843:
2840:
2838:
2837:Data scraping
2835:
2833:
2830:
2828:
2825:
2823:
2820:
2818:
2815:
2813:
2810:
2808:
2807:Cryptojacking
2805:
2803:
2800:
2798:
2795:
2793:
2790:
2788:
2785:
2783:
2780:
2778:
2775:
2773:
2770:
2766:
2763:
2761:
2758:
2756:
2753:
2751:
2748:
2747:
2745:
2743:
2740:
2738:
2735:
2733:
2730:
2728:
2725:
2724:
2722:
2720:
2716:
2708:
2698:
2695:
2693:
2690:
2688:
2685:
2683:
2680:
2678:
2675:
2673:
2670:
2668:
2665:
2663:
2660:
2658:
2655:
2653:
2650:
2646:
2643:
2641:
2638:
2637:
2636:
2633:
2631:
2628:
2626:
2623:
2622:
2620:
2616:
2612:
2605:
2600:
2598:
2593:
2591:
2586:
2585:
2582:
2576:
2572:
2566:
2562:
2561:
2557:
2552:
2551:
2550:
2548:
2543:
2520:
2513:
2506:
2498:
2494:
2487:
2472:
2465:
2451:
2447:
2440:
2432:
2428:
2424:
2420:
2416:
2412:
2408:
2401:
2393:
2389:
2385:
2381:
2377:
2370:
2362:
2356:
2348:
2341:
2333:
2329:
2322:
2308:
2304:
2297:
2289:
2285:
2281:
2275:
2271:
2267:
2262:
2257:
2253:
2246:
2238:
2234:
2230:
2224:
2220:
2216:
2212:
2205:
2197:
2193:
2189:
2182:
2174:
2170:
2165:
2160:
2156:
2149:
2141:
2137:
2133:
2126:
2118:
2114:
2110:
2103:
2084:
2083:
2075:
2067:
2065:9781450313124
2061:
2057:
2053:
2049:
2042:
2034:
2030:
2026:
2019:
2003:
1999:
1993:
1985:
1981:
1977:
1970:
1962:
1956:
1952:
1948:
1944:
1937:
1930:
1915:
1911:
1905:
1897:
1893:
1886:
1878:
1874:
1867:
1859:
1852:
1841:
1834:
1819:
1815:
1808:
1792:
1786:
1770:
1766:
1760:
1744:
1740:
1734:
1720:
1716:
1709:
1693:
1689:
1685:
1678:
1672:
1671:9781848729636
1668:
1662:
1653:
1638:
1634:
1628:
1613:
1609:
1603:
1595:
1582:
1568:on 2008-09-13
1564:
1557:
1550:
1542:
1529:
1511:
1507:
1500:
1494:
1486:
1479:
1471:
1465:
1458:
1454:
1451:
1445:
1437:
1433:
1426:
1419:
1415:
1412:
1406:
1404:
1396:
1390:
1388:
1373:on 2013-12-20
1372:
1368:
1367:qccglobal.com
1364:
1358:
1344:
1338:
1330:
1324:
1317:
1311:
1303:
1299:
1295:
1289:
1285:
1281:
1277:
1273:
1266:
1259:
1255:
1250:
1236:on 2013-09-11
1235:
1231:
1225:
1218:
1213:
1205:
1201:
1197:
1193:
1188:
1183:
1178:
1173:
1169:
1165:
1161:
1154:
1146:
1142:
1138:
1134:
1130:
1126:
1122:
1118:
1114:
1107:
1103:
1093:
1090:
1088:
1085:
1083:
1080:
1078:
1075:
1073:
1070:
1068:
1065:
1063:
1060:
1058:
1055:
1053:
1050:
1048:
1045:
1043:
1040:
1038:
1035:
1034:
1028:
1024:
1020:
1018:
1014:
1010:
1006:
1005:context menus
995:
993:
982:
979:
977:
973:
969:
965:
961:
957:
947:
944:
934:
932:
931:cryptanalysis
921:
919:
909:
907:
903:
899:
895:
890:
886:
882:
872:
868:
865:
855:
853:
849:
845:
841:
837:
833:
829:
823:
813:
811:
807:
798:
795:
790:
786:
784:
780:
776:
772:
767:
757:
754:
750:
740:
737:
733:
727:
717:
714:
712:
701:
699:
695:
691:
687:
683:
680:
676:
673:In 2000, the
669:Use by police
666:
664:
660:
656:
652:
648:
644:
633:
631:
627:
623:
609:
606:
601:
596:
595:accelerometer
592:
589:
585:
582:
578:
573:
570:
566:
562:
558:
554:
550:
546:
544:is collected.
543:
539:
535:
530:
526:
522:
518:
514:
511:
506:
502:
498:
495:
491:
487:
483:
482:
481:
477:
468:
460:
448:
444:
440:
437:
434:
431:
427:
423:
419:
415:
412:
408:
407:
406:
398:
392:
389:
386:
383:
382:
381:
378:
376:
360:
357:
353:
350:
349:email address
346:
343:
339:
338:
335:
331:
327:
323:
320:
317:
313:
309:
301:
298:
294:
290:
289:Form grabbing
286:
283:
278:
274:
262:
261:
259:
255:
251:
247:
244:
241:
240:device driver
237:
233:
229:
225:
223:
219:
216:
212:
208:
205:
201:
198:
197:
196:
193:
191:
187:
182:
178:
173:
165:
160:
152:
138:
136:
131:
129:
125:
121:
116:
114:
111:systems. The
110:
102:
98:
94:
84:
82:
78:
74:
69:
67:
62:
60:
56:
52:
48:
44:
40:
36:
32:
19:
3542:Surveillance
3332:
3277:Trojan horse
3257:Clickjacking
3103:Data masking
2886:
2662:Cyberwarfare
2558:
2539:
2522:. Retrieved
2505:
2497:the original
2486:
2475:. Retrieved
2464:
2453:. Retrieved
2450:The Register
2449:
2439:
2414:
2410:
2400:
2383:
2379:
2369:
2355:
2340:
2332:The Register
2331:
2321:
2310:. Retrieved
2307:The Register
2306:
2296:
2251:
2245:
2210:
2204:
2195:
2191:
2181:
2154:
2148:
2131:
2125:
2108:
2102:
2090:. Retrieved
2081:
2074:
2047:
2041:
2024:
2018:
2006:. Retrieved
2001:
1992:
1975:
1969:
1942:
1929:
1918:. Retrieved
1913:
1910:"ATM camera"
1904:
1895:
1885:
1876:
1866:
1851:
1833:
1822:. Retrieved
1820:News Service
1807:
1795:. Retrieved
1785:
1773:. Retrieved
1769:the original
1759:
1747:. Retrieved
1743:the original
1733:
1722:. Retrieved
1708:
1696:. Retrieved
1692:the original
1688:Spyware Loop
1687:
1677:
1661:
1652:
1640:. Retrieved
1636:
1627:
1616:. Retrieved
1614:. 2016-10-06
1611:
1602:
1581:cite journal
1570:. Retrieved
1563:the original
1549:
1528:cite journal
1517:. Retrieved
1510:the original
1493:
1478:
1464:
1444:
1436:inquirer.net
1435:
1425:
1375:. Retrieved
1371:the original
1366:
1357:
1346:. Retrieved
1337:
1323:
1310:
1275:
1265:
1257:
1249:
1238:. Retrieved
1234:the original
1224:
1212:
1167:
1163:
1153:
1120:
1116:
1106:
1092:Web tracking
1082:Trojan horse
1025:
1021:
1001:
988:
980:
964:touchscreens
953:
940:
927:
915:
878:
869:
861:
832:Web browsers
828:Form fillers
825:
810:phoning home
804:
791:
787:
781:and certain
766:anti-spyware
763:
746:
729:
715:
711:anti-spyware
707:
672:
647:cryptotrojan
639:
622:trojan horse
619:
479:
404:
396:
379:
371:
321:
299:
284:
245:
232:kernel level
220:
199:
194:
169:
132:
117:
93:Soviet Union
90:
70:
63:
50:
46:
38:
34:
30:
29:
3409:Macro virus
3394:iOS malware
3368:Web threats
3328:Infostealer
3245:Concealment
3043:Misuse case
2877:Infostealer
2852:Email fraud
2817:Data breach
2652:Cybergeddon
2198:(7): 79–94.
1797:26 February
1713:Microsoft.
1472:. PC Tools.
1258:Secure List
1230:"Keylogger"
1007:to remove,
958:and lately
881:smart cards
852:proxy tools
836:credit card
822:Form filler
756:keylogger.
743:Live CD/USB
418:Screenshots
228:root access
97:typewriters
3547:Cybercrime
3526:Categories
3433:Protection
3348:Ransomware
3313:Fleeceware
3108:Encryption
2984:Web shells
2924:Ransomware
2872:Hacktivism
2635:Cybercrime
2571:Keyloggers
2524:2008-09-23
2477:2014-05-10
2455:2009-04-18
2312:2009-04-19
2008:August 25,
1920:2009-04-19
1824:2009-04-19
1724:2009-07-15
1618:2017-01-24
1572:2008-09-23
1519:2011-03-25
1377:2013-12-20
1348:2009-11-22
1240:2013-08-03
1098:References
1052:Cybercrime
976:light pens
960:tablet PCs
918:Windows XP
775:heuristics
682:passphrase
655:ciphertext
651:public key
630:IP address
591:Smartphone
356:wirelessly
207:hypervisor
181:Windows 10
120:US Embassy
35:keylogging
18:Keylogging
3358:Scareware
3308:Crimeware
2939:Shellcode
2934:Scareware
2782:Crimeware
2742:Backdoors
2563:is being
2431:0167-4048
2256:CiteSeerX
2164:1405.3760
2092:25 August
1719:Microsoft
1302:252849669
1204:238703970
1196:1560-4292
1137:1536-1233
1013:key space
883:or other
840:clipboard
605:gyroscope
565:shielding
524:presence.
411:clipboard
387:spelling,
304:onKeyUp()
296:Internet.
252:keyboard
246:API-based
215:Blue Pill
177:Microsoft
128:Selectric
113:user-mode
105:/dev/kmem
51:keylogger
3506:Honeypot
3465:Firewall
3252:Backdoor
3113:Firewall
3018:Defenses
2944:Spamming
2929:Rootkits
2902:Phishing
2862:Exploits
2556:template
2288:12179472
2237:14768587
1775:25 April
1642:26 April
1506:Symantec
1453:Archived
1414:Archived
1031:See also
753:Live USB
736:software
616:Cracking
569:receiver
536:such as
490:firmware
375:Inputlog
354:Data is
293:Web form
236:rootkits
81:software
59:hardware
55:software
43:keyboard
3537:Spyware
3363:Spyware
3272:Rootkit
3201:Malware
2954:Spyware
2897:Payload
2892:Malware
2832:Viruses
2812:Botnets
2719:Threats
1898:: 1–16.
1698:27 July
1420:. 2012.
1397:. 2013.
1145:8161528
1077:Spyware
879:Use of
749:Live CD
636:Trojans
488:-level
426:control
344:server.
204:malware
164:logfile
87:History
3338:Malbot
3303:Botnet
3298:Adware
3203:topics
3148:(SIEM)
3125:(HIDS)
3009:Zombie
2746:Bombs
2727:Adware
2575:Curlie
2569:
2560:Curlie
2429:
2286:
2276:
2258:
2235:
2225:
2062:
1957:
1749:9 June
1669:
1300:
1290:
1202:
1194:
1143:
1135:
862:Using
698:Russia
663:Usenet
600:QWERTY
579:at an
542:sample
428:. The
334:SpyEye
224:-based
222:Kernel
124:Moscow
2994:Worms
2989:Wiper
2907:Voice
2755:Logic
2554:‹The
2515:(PDF)
2284:S2CID
2233:S2CID
2159:arXiv
2086:(PDF)
2002:Wired
1939:(PDF)
1877:ZDNet
1843:(PDF)
1566:(PDF)
1559:(PDF)
1513:(PDF)
1502:(PDF)
1298:S2CID
1200:S2CID
1141:S2CID
954:Many
779:hooks
764:Many
626:virus
258:event
186:HTTPS
2760:Time
2750:Fork
2427:ISSN
2384:2017
2274:ISBN
2223:ISBN
2094:2014
2060:ISBN
2010:2014
1955:ISBN
1799:2016
1777:2011
1751:2011
1700:2013
1667:ISBN
1644:2011
1594:help
1541:help
1288:ISBN
1192:ISSN
1133:ISSN
974:and
956:PDAs
850:and
783:APIs
643:worm
557:PS/2
521:ATMs
486:BIOS
332:and
330:Zeus
326:MitB
277:PINs
273:BIOS
254:APIs
250:hook
109:Unix
2765:Zip
2573:at
2419:doi
2388:doi
2266:doi
2215:doi
2169:doi
2136:doi
2113:doi
2052:doi
2029:doi
1980:doi
1947:doi
1818:IDG
1280:doi
1182:hdl
1172:doi
1125:doi
902:PIN
854:.)
785:).
730:An
684:of
679:PGP
675:FBI
581:ATM
553:USB
505:USB
433:API
342:FTP
107:on
75:or
57:or
49:or
37:or
3528::
2567:.›
2517:.
2448:.
2425:.
2415:26
2413:.
2409:.
2382:.
2378:.
2330:.
2305:.
2282:.
2272:.
2264:.
2231:.
2221:.
2196:14
2194:.
2190:.
2167:.
2058:.
2000:.
1953:.
1941:.
1912:.
1894:.
1875:.
1816:.
1717:.
1686:.
1635:.
1610:.
1585::
1583:}}
1579:{{
1532::
1530:}}
1526:{{
1504:.
1434:.
1402:^
1386:^
1365:.
1296:.
1286:.
1274:.
1256:,
1198:.
1190:.
1180:.
1168:32
1166:.
1162:.
1139:.
1131:.
1121:13
1119:.
1115:.
1019:.
773:,
665:.
555:,
445:,
314:,
310:,
287::
267:,
213:.
172:IT
162:A
61:.
3193:e
3186:t
3179:v
2603:e
2596:t
2589:v
2527:.
2480:.
2458:.
2433:.
2421::
2394:.
2390::
2349:.
2334:.
2315:.
2290:.
2268::
2239:.
2217::
2175:.
2171::
2161::
2142:.
2138::
2119:.
2115::
2096:.
2068:.
2054::
2035:.
2031::
2012:.
1986:.
1982::
1963:.
1949::
1923:.
1879:.
1845:.
1827:.
1801:.
1779:.
1753:.
1727:.
1702:.
1646:.
1621:.
1596:)
1592:(
1575:.
1543:)
1539:(
1522:.
1487:.
1459:.
1438:.
1380:.
1351:.
1331:.
1304:.
1282::
1243:.
1206:.
1184::
1174::
1147:.
1127::
351:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.