1047:
how to service, which may raise spurious interrupts, it will not interfere with interrupt signaling of other devices. However, it is easy for an edge-triggered interrupt to be missed - for example, when interrupts are masked for a period - and unless there is some type of hardware latch that records the event it is impossible to recover. This problem caused many "lockups" in early computer hardware because the processor did not know it was expected to do something. More modern hardware often has one or more interrupt status registers that latch interrupts requests; well-written edge-driven interrupt handling code can check these registers to ensure no events are missed.
155:
374:
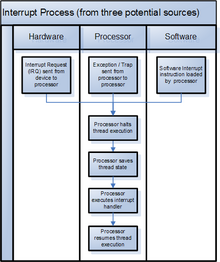
745:, and identifies three types of exceptions: faults, traps, and aborts. (Hardware) interrupts are interrupts triggered asynchronously by an I/O device, and allow the program to be restarted with no loss of continuity. A fault is restartable as well but is tied to the synchronous execution of an instruction - the return address points to the faulting instruction. A trap is similar to a fault except that the return address points to the instruction to be executed after the trapping instruction; one prominent use is to implement
978:
879:
1499:
1169:
47:
1062:
Talking can be triggered in two ways: by accumulation latch or by logic gates. Logic gates expect a continual data flow that is monitored for key signals. Accumulators only trigger when the remote side excites the gate beyond a threshold, thus no negotiated speed is required. Each has its speed versus distance advantages. A trigger, generally, is the method in which excitation is detected: rising edge, falling edge, threshold (
252:
545:
circuit to return to the quiescent state before the current instance of the ISR terminates. The result is the processor will think another interrupt is pending, since the voltage at its interrupt request input will be not high or low enough to establish an unambiguous internal logic 1 or logic 0. The apparent interrupt will have no identifiable source, hence the "spurious" moniker.
1254:
may even be multiple doorbells serving different purposes in this region. It is this act of writing to the doorbell region of memory that "rings the bell" and notifies the hardware device that the data are ready and waiting. The hardware device would now know that the data are valid and can be acted upon. It would typically write the data to a
455:, all interrupts went to the same location, and the OS used a specialized instruction to determine the highest-priority outstanding unmasked interrupt. On contemporary systems, there is generally a distinct interrupt routine for each type of interrupt (or for each interrupt source), often implemented as one or more
771:, and exception-generating instructions. Aborts correspond to x86 exceptions and may be prefetch aborts (failed instruction fetches) or data aborts (failed data accesses), and may be synchronous or asynchronous. Asynchronous aborts may be precise or imprecise. MMU aborts (page faults) are synchronous.
1355:
associated to separate interrupts; by routing each of those interrupts to different cores, processing of the interrupt requests triggered by the network traffic received by a single NIC can be distributed among multiple cores. Distribution of the interrupts among cores can be performed automatically
1107:
A common use of a hybrid interrupt is for the NMI (non-maskable interrupt) input. Because NMIs generally signal major – or even catastrophic – system events, a good implementation of this signal tries to ensure that the interrupt is valid by verifying that it remains active for a period of time. This
1042:
on some buses and trolleys that any passenger can pull to signal the driver that they are requesting a stop.) However, interrupt pulses from different devices may merge if they occur close in time. To avoid losing interrupts the CPU must trigger on the trailing edge of the pulse (e.g. the rising edge
864:
There are several different architectures for handling interrupts. In some, there is a single interrupt handler that must scan for the highest priority enabled interrupt. In others, there are separate interrupt handlers for separate interrupt types, separate I/O channels or devices, or both. Several
830:
then special hardware may be required to detect it. The important part of edge triggering is that the signal must transition to trigger the interrupt; for example, if the signal was high-low-low, there would only be one falling edge interrupt triggered, and the continued low level would not trigger a
1046:
Edge-triggered interrupts do not suffer the problems that level-triggered interrupts have with sharing. Service of a low-priority device can be postponed arbitrarily, while interrupts from high-priority devices continue to be received and get serviced. If there is a device that the CPU does not know
544:
charging/discharging through the interrupt line's bias resistor will cause a small delay before the processor recognizes that the interrupt source has been cleared. If the interrupting device is cleared too late in the interrupt service routine (ISR), there will not be enough time for the interrupt
520:(OS/360) relies on a not-ready to ready device-end interrupt when a tape has been mounted on a tape drive, and will not read the tape label until that interrupt occurs or is simulated. IBM added code in OS/360 so that the VARY ONLINE command will simulate a device end interrupt on the target device.
512:
One failure mode is when the hardware does not generate the expected interrupt for a change in state, causing the operating system to wait indefinitely. Depending on the details, the failure might affect only a single process or might have global impact. Some operating systems have code specifically
2054:
The concept of an interrupt is something that has expanded in scope over the years. The 80x86 family has only added to the confusion surrounding interrupts by introducing the int (software interrupt) instruction. Indeed different manufacturers have used terms like exceptions faults aborts traps and
1439:
A disk interrupt signals the completion of a data transfer from or to the disk peripheral; this may cause a process to run which is waiting to read or write. A power-off interrupt predicts imminent loss of power, allowing the computer to perform an orderly shut-down while there still remains enough
1086:
Some devices with a poorly designed programming interface provide no way to determine whether they have requested service. They may lock up or otherwise misbehave if serviced when they do not want it. Such devices cannot tolerate spurious interrupts, and so also cannot tolerate sharing an interrupt
785:
Each interrupt signal input is designed to be triggered by either a logic signal level or a particular signal edge (level transition). Level-sensitive inputs continuously request processor service so long as a particular (high or low) logic level is applied to the input. Edge-sensitive inputs react
1253:
device that there is some work to be done. Typically, the software system will place data in some well-known and mutually agreed upon memory locations, and "ring the doorbell" by writing to a different memory location. This different memory location is often called the doorbell region, and there
1078:
Multiple devices sharing an interrupt line (of any triggering style) all act as spurious interrupt sources with respect to each other. With many devices on one line, the workload in servicing interrupts grows in proportion to the square of the number of devices. It is therefore preferred to spread
1069:
Triggering for software interrupts must be built into the software (both in OS and app). A 'C' app has a trigger table (a table of functions) in its header, which both the app and OS know of and use appropriately that is not related to hardware. However do not confuse this with hardware interrupts
567:
A spurious interrupt may result in system deadlock or other undefined operation if the ISR does not account for the possibility of such an interrupt occurring. As spurious interrupts are mostly a problem with wired-OR interrupt circuits, good programming practice in such systems is for the ISR to
1455:
instructions may be implemented in hardware on some systems and emulated on lower-cost systems. In the latter case, execution of an unimplemented floating point instruction will cause an "illegal instruction" exception interrupt. The interrupt handler will implement the floating point function in
1033:
Multiple devices may share an edge-triggered interrupt line if they are designed to. The interrupt line must have a pull-down or pull-up resistor so that when not actively driven it settles to its inactive state, which is the default state of it. Devices signal an interrupt by briefly driving the
808:
Level-triggered inputs allow multiple devices to share a common interrupt signal via wired-OR connections. The processor polls to determine which devices are requesting service. After servicing a device, the processor may again poll and, if necessary, service other devices before exiting the ISR.
1133:
Message-signalled interrupts behave very much like edge-triggered interrupts, in that the interrupt is a momentary signal rather than a continuous condition. Interrupt-handling software treats the two in much the same manner. Typically, multiple pending message-signaled interrupts with the same
1061:
There are three ways multiple devices "sharing the same line" can be raised. First is by exclusive conduction (switching) or exclusive connection (to pins). Next is by bus (all connected to the same line listening): cards on a bus must know when they are to talk and not talk (i.e., the ISA bus).
846:
The processor samples the interrupt trigger signals or interrupt register during each instruction cycle, and will process the highest priority enabled interrupt found. Regardless of the triggering method, the processor will begin interrupt processing at the next instruction boundary following a
482:
register, which allows selective enabling (and disabling) of hardware interrupts. Each interrupt signal is associated with a bit in the mask register. On some systems, the interrupt is enabled when the bit is set, and disabled when the bit is clear. On others, the reverse is true, and a set bit
1079:
devices evenly across the available interrupt lines. Shortage of interrupt lines is a problem in older system designs where the interrupt lines are distinct physical conductors. Message-signaled interrupts, where the interrupt line is virtual, are favored in new system architectures (such as
1144:
Because the identity of the interrupt is indicated by a pattern of data bits, not requiring a separate physical conductor, many more distinct interrupts can be efficiently handled. This reduces the need for sharing. Interrupt messages can also be passed over a serial bus, not requiring any
831:
further interrupt. The signal must return to the high level and fall again in order to trigger a further interrupt. This contrasts with a level trigger where the low level would continue to create interrupts (if they are enabled) until the signal returns to its high level.
1324:
at low load, but degrade significantly at high interrupt rate unless care is taken to prevent several pathologies. The phenomenon where the overall system performance is severely hindered by excessive amounts of processing time spent handling interrupts is called an
1400:), handle keyboard and mouse events, and to respond to any other time-sensitive events as required by the application system. Non-maskable interrupts are typically used to respond to high-priority requests such as watchdog timer timeouts, power-down signals and
1054:(ISA) bus uses edge-triggered interrupts, without mandating that devices be able to share IRQ lines, but all mainstream ISA motherboards include pull-up resistors on their IRQ lines, so well-behaved ISA devices sharing IRQ lines should just work fine. The
443:
with respect to the processor clock, and at any time during instruction execution. Consequently, all incoming hardware interrupt signals are conditioned by synchronizing them to the processor clock, and acted upon only at instruction execution boundaries.
825:
on the interrupt line, either a falling edge (high to low) or a rising edge (low to high). A device wishing to signal an interrupt drives a pulse onto the line and then releases the line to its inactive state. If the pulse is too short to be detected by
1336:, when the system spends all of its time processing interrupts to the exclusion of other required tasks. Under extreme conditions, a large number of interrupts (like very high network traffic) may completely stall the system. To avoid such problems, an
1285:, and sometimes the doorbell region is hardwired directly to physical device registers. When either writing through or directly to physical device registers, this may cause a real interrupt to occur at the device's central processor unit (
1371:
functionality. Advantages of RPS over RSS include no requirements for specific hardware, more advanced traffic distribution filters, and reduced rate of interrupts produced by a NIC. As a downside, RPS increases the rate of
297:, ISR) to deal with the event. This interruption is often temporary, allowing the software to resume normal activities after the interrupt handler finishes, although the interrupt could instead indicate a fatal error.
802:. A device invokes a level-triggered interrupt by driving the signal to and holding it at the active level. It negates the signal when the processor commands it to do so, typically after the device has been serviced.
576:
A software interrupt is requested by the processor itself upon executing particular instructions or when certain conditions are met. Every software interrupt signal is associated with a particular interrupt handler.
568:
check all interrupt sources for activity and take no action (other than possibly logging the event) if none of the sources is interrupting. They may even lead to crashing of the computer in adverse scenarios.
1958:
In Cortex-M4 system, the interrupts and exceptions have the following properties: ... Generally, a single bit in a mask register is used to mask (disable) or unmask (enable) certain interrupt/exceptions to
1103:
Some systems use a hybrid of level-triggered and edge-triggered signaling. The hardware not only looks for an edge, but it also verifies that the interrupt signal stays active for a certain period of time.
1407:
Hardware timers are often used to generate periodic interrupts. In some applications, such interrupts are counted by the interrupt handler to keep track of absolute or elapsed time, or used by the OS task
532:
is a hardware interrupt for which no source can be found. The term "phantom interrupt" or "ghost interrupt" may also be used to describe this phenomenon. Spurious interrupts tend to be a problem with a
447:
In many systems, each device is associated with a particular IRQ signal. This makes it possible to quickly determine which hardware device is requesting service, and to expedite servicing of that device.
2055:
interrupts to describe the phenomena this chapter discusses. Unfortunately there is no clear consensus as to the exact meaning of these terms. Different authors adopt different terms to their own use.
483:
disables the interrupt. When the interrupt is disabled, the associated interrupt signal may be ignored by the processor, or it may remain pending. Signals which are affected by the mask are called
1892:
1769:
Then it's just a matter of cleaning up, running software interrupts, and getting back to regular work. The "regular work" may well have changed as a result of an interrupt (the handler could
964:(SoC) implementations, interrupts come from different blocks of the chip and are usually aggregated in an interrupt controller attached to one or several processors (in a multi-core system).
279:
currently executing code (when permitted), so that the event can be processed in a timely manner. If the request is accepted, the processor will suspend its current activities, save its
1456:
software and then return to the interrupted program as if the hardware-implemented instruction had been executed. This provides application software portability across the entire line.
2070:
300:
Interrupts are commonly used by hardware devices to indicate electronic or physical state changes that require time-sensitive attention. Interrupts are also commonly used to implement
1384:; further performance improvements are achieved by processing interrupt requests by the same cores on which particular network packets will be consumed by the targeted application.
805:
The processor samples the interrupt input signal during each instruction cycle. The processor will recognize the interrupt request if the signal is asserted when sampling occurs.
2123:
339:(1951) "Arithmetic overflow either triggered the execution of a two-instruction fix-up routine at address 0, or, at the programmer's option, caused the computer to stop." The
408:(IRQ) line on a PC, or detected by devices embedded in processor logic (e.g., the CPU timer in IBM System/370), to communicate that the device needs attention from the
786:
to signal edges: a particular (rising or falling) edge will cause a service request to be latched; the processor resets the latch when the interrupt handler executes.
2606:
1126:
does not use a physical interrupt line. Instead, a device signals its request for service by sending a short message over some communications medium, typically a
1034:
line to its non-default state, and let the line float (do not actively drive it) when not signaling an interrupt. This type of connection is also referred to as
504:, the Non-Maskable Interrupt (NMI), despite having the highest priority among interrupts, can be prevented from occurring through the use of an interrupt mask.
1670:
Some operating systems can recover from severe errors, e.g., paging in a page from a paging file after an uncorrectable ECC error in an unaltered page.
1058:
also uses edge-triggered interrupts. Many older devices assume that they have exclusive use of IRQ lines, making it electrically unsafe to share them.
1467:(IPC), mediated by the kernel (possibly via system calls) and handled by processes, while interrupts are mediated by the processor and handled by the
749:. An abort is used for severe errors, such as hardware errors and illegal values in system tables, and often does not allow a restart of the program.
2693:
1277:. It is similar to an interrupt, because it causes some work to be done by the device; however, the doorbell region is sometimes implemented as a
851:
The processor status is saved in a known manner. Typically the status is stored in a known location, but on some systems it is stored on a stack.
1392:
Interrupts are commonly used to service hardware timers, transfer data to and from storage (e.g., disk I/O) and communication interfaces (e.g.,
691:
may refer to any interrupt, to any software interrupt, to any synchronous software interrupt, or only to interrupts caused by instructions with
865:
interrupt causes may have the same interrupt type and thus the same interrupt handler, requiring the interrupt handler to determine the cause.
945:
If an additional component is used, that component would be connected between the interrupting device and the processor's interrupt pin to
603:
will catch and handle such interrupts. Some interrupts are handled transparently to the program - for example, the normal resolution of a
2640:
2562:
537:
interrupt circuit attached to a level-sensitive processor input. Such interrupts may be difficult to identify when a system misbehaves.
857:
No instruction beyond the one pointed to by the PC has been executed, or any such instructions are undone before handling the interrupt.
1513:
404:
A hardware interrupt is a condition related to the state of the hardware that may be signaled by an external hardware device, e.g., an
638:, which may either call a signal handler or execute a default action (terminating the program). On Windows the callback is made using
687:
are used to distinguish types of interrupts, although "there is no clear consensus as to the exact meaning of these terms". The term
1043:
if the line is pulled up and driven low). After detecting an interrupt the CPU must check all the devices for service requirements.
2171:
2038:
1607:
Typically, interrupt events associated with I/O remain pending until the interrupt is enabled or explicitly cleared, e.g., by the
1451:
Interrupts are sometimes used to emulate instructions which are unimplemented on some computers in a product family. For example
838:
that retains the status of pending interrupts. Systems with interrupt registers generally have interrupt mask registers as well.
1773:
a process, for example), so the last thing that happens on return from an interrupt is a possible rescheduling of the processor.
496:(NMIs). These indicate high-priority events which cannot be ignored under any circumstances, such as the timeout signal from a
160:
2969:
2940:
2596:
2321:
2104:
1943:
1564:
1786:
1134:
message (the same virtual interrupt line) are allowed to merge, just as closely spaced edge-triggered interrupts can merge.
1091:
cards, due to often cheap design and construction, are notorious for this problem. Such devices are becoming much rarer, as
1130:. The message might be of a type reserved for interrupts, or it might be of some pre-existing type such as a memory write.
1971:
934:
Interrupts may be fully handled in hardware by the CPU, or may be handled by both the CPU and another component such as a
31:
649:, it is often the case that some types of software interrupts are not supposed to happen. If they occur nonetheless, an
592:(e.g., to read or write storage media). Software interrupts may also be triggered by program execution errors or by the
111:
1141:
can be shared, to the extent that the underlying communication medium can be shared. No additional effort is required.
159:
83:
2420:
1844:
1216:
1020:
935:
921:
130:
2501:
1198:
2744:
2688:
777:
uses interrupt as the overall term as well as for the external subset; internal interrupts are called exceptions.
358:, with a "transfer trap", which could invoke a special routine when a branch instruction was encountered. The MIT
2663:
2633:
1574:
987:
888:
490:
Some interrupt signals are not affected by the interrupt mask and therefore cannot be disabled; these are called
90:
2856:
2754:
2197:
2145:
2000:
1913:
1559:
1194:
1088:
1051:
581:
177:
161:
68:
1343:
With multi-core processors, additional performance improvements in interrupt handling can be achieved through
949:
several sources of interrupt onto the one or two CPU lines typically available. If implemented as part of the
650:
3134:
2683:
2668:
2591:
2286:
2277:
2263:
2016:
1554:
1421:
639:
35:
2508:
2231:
1070:
which signal the CPU (the CPU enacts software from a table of functions, similarly to software interrupts).
396:, respectively. For any particular processor, the number of interrupt types is limited by the architecture.
2729:
2714:
2673:
2612:
2124:"Intel® 64 and IA-32 architectures software developer's manual volume 3A: System programming guide, part 1"
344:
238:
97:
1632:
are 0 (disabled), the corresponding overflow and significance events do not result in a pending interrupt.
588:
and are used for a variety of purposes, such as requesting operating system services and interacting with
2895:
2842:
2301:
1464:
1429:
1417:
1293:
1152:
1117:
708:
2910:
2749:
2626:
1352:
1309:
1278:
1190:
440:
321:
64:
17:
2254:
79:
2945:
2764:
2724:
2719:
2678:
1468:
1373:
600:
1416:, or both. Periodic interrupts are also commonly used to invoke sampling from input devices such as
2988:
2875:
2739:
2206:
1524:
1471:. The kernel may pass an interrupt as a signal to the process that caused it (typical examples are
1179:
280:
158:
30:
This article is about computer interrupts conceptually. For interrupts on the PC architecture, see
2391:
662:
2734:
1183:
939:
899:
752:
553:
320:
Hardware interrupts were introduced as an optimization, eliminating unproductive waiting time in
272:
57:
3122:
3061:
2950:
2930:
2879:
2837:
1409:
1038:. The line then carries all the pulses generated by all the devices. (This is analogous to the
991:
892:
492:
456:
436:
triggers hardware interrupts that cause the processor to read the keystroke or mouse position.
284:
584:
which, by design, invokes an interrupt when executed. Such instructions function similarly to
2905:
2871:
2773:
2709:
1933:
1659:
1569:
1534:
541:
517:
301:
2071:"Intel® 64 and IA-32 Architectures Software Developer's Manual Volume 1: Basic Architecture"
373:
335:
computer is generally credited with the earliest use of interrupts in 1953. Earlier, on the
3102:
3076:
1539:
1381:
1344:
425:
1002:
903:
8:
3155:
3071:
3023:
2900:
1684:
1642:
1595:
1519:
1413:
1340:
must schedule network interrupt handling as carefully as it schedules process execution.
715:. It may also refer to a synchronous interrupt caused by an exceptional condition (e.g.,
646:
642:
with an exception code such as STATUS_ACCESS_VIOLATION or STATUS_INTEGER_DIVIDE_BY_ZERO.
607:
is to make the required page accessible in physical memory. But in other cases such as a
309:
3008:
2915:
2363:
2313:
1529:
1504:
1401:
1367:(RPS), distributes received traffic among cores later in the data path, as part of the
1363:
A purely software-based implementation of the receiving traffic distribution, known as
720:
608:
471:
an interrupt is to disable it, so it is deferred or ignored by the processor, while to
359:
104:
1871:
3117:
3066:
2998:
2955:
2796:
2367:
2317:
2100:
1996:
1949:
1939:
1840:
1756:
1616:
1549:
1544:
1368:
1321:
1282:
1250:
950:
429:
416:
program running on the CPU. Such external devices may be part of the computer (e.g.,
405:
381:
289:
207:
187:
1641:
The mask register may be a single register or multiple registers, e.g., bits in the
798:
is requested by holding the interrupt signal at its particular (high or low) active
3097:
2649:
2355:
2309:
1646:
1433:
1337:
1259:
1234:
1138:
961:
716:
615:
409:
260:
231:
202:
146:
1743:
3041:
3003:
2974:
1834:
1790:
1680:
1326:
1255:
585:
417:
3127:
3051:
3013:
2885:
2343:
2095:
Bryant, Randal E.; O’Hallaron, David R. (2016). "8.1.2 Classes of exceptions".
1629:
1452:
1348:
1305:
1108:
2-step approach helps to eliminate false interrupts from affecting the system.
1092:
1035:
724:
704:
593:
497:
365:
system (1957) was the first to provide multiple levels of priority interrupts.
2601:
2536:
1719:
1356:
by the operating system, or the routing of interrupts (usually referred to as
3149:
3036:
2993:
2832:
2786:
1811:
1055:
954:
589:
328:, completed in 1954, although earlier systems provided error trap functions.
324:, waiting for external events. The first system to use this approach was the
312:. Systems that use interrupts in these ways are said to be interrupt-driven.
197:
1308:
systems, a processor may send an interrupt request to another processor via
759:
to refer to all types of interrupts, and divides exceptions into (hardware)
2920:
1745:
1460:
1127:
1095:
becomes cheaper and new system architectures mandate shareable interrupts.
1063:
946:
619:
561:
332:
212:
2359:
3046:
3028:
2811:
2801:
2791:
1230:
1148:
1080:
854:
All instructions before the one pointed to by the PC have fully executed.
822:
799:
746:
305:
224:
192:
1281:
region, sometimes the doorbell region writes through to physical device
580:
A software interrupt may be intentionally caused by executing a special
2399:
1441:
827:
700:
604:
421:
413:
2607:
University of
Alberta CMPUT 296 Concrete Computing Notes on Interrupts
1935:
Microcontroller
Engineering with MSP432: Fundamentals and Applications
2983:
2816:
2781:
1445:
1039:
860:
The execution state of the instruction pointed to by the PC is known.
612:
557:
433:
355:
2618:
1168:
251:
46:
3112:
2476:
2450:
1498:
1397:
1333:
1274:
1246:
712:
534:
452:
385:
343:(1954) incorporated the first occurrence of interrupt masking. The
336:
1953:
1380:(RFS) takes the software-based approach further by accounting for
3107:
2806:
2480:
2454:
1472:
1263:
623:
351:
340:
1744:
Jonathan Corbet; Alessandro Rubini; Greg Kroah-Hartman (2005).
1484:
1480:
1476:
774:
635:
631:
627:
549:
347:
325:
2039:"Chapter Seventeen: Interrupts, Traps and Exceptions (Part 1)"
1921:. Control Data Corporation. July 1964. pp. 4–6. 60021300.
27:
Signal to a computer processor emitted by hardware or software
3056:
2427:
2199:
Control Data 6400/6500/6600 Computer
Systems Reference Manual
501:
2344:"Eliminating receive livelock in an interrupt-driven kernel"
998:
2510:
IBM System/360 Operating System - Guide to Model 91 Support
2389:
1425:
1393:
362:
2421:"Intel 82574 Gigabit Ethernet Controller Family Datasheet"
2306:
The
Definitive Guide to the ARM Cortex-M3 (Second Edition)
1073:
548:
A spurious interrupt may also be the result of electrical
3092:
2240:
1286:
734:
834:
Computers with edge-triggered interrupts may include an
2516:. Systems Reference Library. pp. 11–12. C28-6666-0
1066:
can trigger a wide variety of shapes and conditions).
1696:
Known as shoulder taps on some IBM operating systems.
1083:) and relieve this problem to a considerable extent.
611:
the operating system executes a process callback. On
2385:
2383:
2178:. ARM Cortex-A Series Programmer's Guide for ARMv7-A
2152:. ARM Cortex-A Series Programmer's Guide for ARMv7-A
1494:
1440:
power to do so. Keyboard interrupts typically cause
350:(1954) was the first to use interrupts for I/O. The
71:. Unsourced material may be challenged and removed.
2560:
1915:Control Data 3600 Computer System Reference Manual
1594:The operating system might resume the interrupted
2380:
2341:
1463:, the difference being that signals are used for
953:, interrupts are mapped into the system's memory
3147:
2256:PDP-11 Processor Handbook PDP11/04//34a/44/60/70
2094:
1750:, Third Edition, Chapter 10. Interrupt Handling"
1245:is often used to describe a mechanism whereby a
2448:
2342:Mogul, Jeffrey C.; Ramakrishnan, K. K. (1997).
380:Interrupt signals may be issued in response to
157:
2609:, archived from the original on March 13, 2012
1428:inputs, and to program output devices such as
1351:are used. Such NICs provide multiple receive
2634:
2390:Tom Herbert; Willem de Bruijn (May 9, 2014).
2300:Yiu, Joseph (2010-01-01), Yiu, Joseph (ed.),
1714:
1712:
232:
2597:Interrupts for Microchip PIC Microcontroller
2097:Computer systems: a programmer's perspective
2032:
2030:
1865:
1863:
2279:PDP-11 Peripherals and Interfacing Handbook
2099:(Third, Global ed.). Harlow: Pearson.
1984:
1197:. Unsourced material may be challenged and
2641:
2627:
1836:Computer structures: readings and examples
1832:
1709:
1514:Advanced Programmable Interrupt Controller
1001:. Please do not remove this message until
902:. Please do not remove this message until
239:
225:
2474:
2243:. September 1968. p. 77. A22-6821-7.
2118:
2116:
2090:
2088:
2065:
2063:
2027:
1860:
1784:
1565:Interrupts on IBM System/360 architecture
1320:Interrupts provide low overhead and good
1217:Learn how and when to remove this message
1021:Learn how and when to remove this message
922:Learn how and when to remove this message
695:in their names. In some usages, the term
131:Learn how and when to remove this message
2043:The Art Of Assembly Language Programming
997:Relevant discussion may be found on the
898:Relevant discussion may be found on the
868:
451:On some older systems, such as the 1964
372:
255:Interrupt sources and processor handling
250:
2302:"CHAPTER 2 - Overview of the Cortex-M3"
2226:
2224:
1993:Real-Time Concepts for Embedded Systems
1833:Bell, C. Gordon; Newell, Allen (1971).
1598:or might switch to a different process.
1292:Doorbell interrupts can be compared to
1074:Difficulty with sharing interrupt lines
14:
3148:
2392:"Documentation/networking/scaling.txt"
2233:IBM System/360 Principles of Operation
2113:
2085:
2060:
1869:
571:
523:
478:Processors typically have an internal
399:
2648:
2622:
2449:Jonathan Corbet (November 17, 2009).
1990:
1299:
841:
780:
507:
412:(OS) or, if there is no OS, from the
2348:ACM Transactions on Computer Systems
2221:
2036:
1739:
1737:
1628:E.g., when program mask bits on the
1195:adding citations to reliable sources
1162:
971:
872:
663:Exception handling § Definition
354:was the first to use interrupts for
69:adding citations to reliable sources
40:
2299:
2164:
1931:
1111:
737:divides interrupts into (hardware)
552:due to faulty circuit design, high
32:Interrupt request (PC architecture)
24:
2534:
2314:10.1016/b978-1-85617-963-8.00005-3
2308:, Oxford: Newnes, pp. 11–24,
1444:to be buffered so as to implement
1296:, as they have some similarities.
789:
153:
25:
3167:
2585:
1734:
936:programmable interrupt controller
847:detected trigger, thus ensuring:
812:
560:, timing issues, or more rarely,
2745:Object-oriented operating system
1991:Li, Qing; Yao, Caroline (2003).
1810:
1720:"The Jargon File, version 4.4.7"
1497:
1167:
976:
877:
599:Typically, the operating system
388:events. These are classified as
45:
2615:- Article by Adityapratap Singh
2554:
2528:
2494:
2468:
2442:
2413:
2335:
2293:
2270:
2247:
2190:
2138:
2009:
1964:
1925:
1690:
1673:
1664:
1652:
1635:
1622:
1601:
1575:Autonomous peripheral operation
1412:to manage execution of running
1387:
439:Hardware interrupts can arrive
56:needs additional citations for
2755:Supercomputer operating system
1905:
1885:
1826:
1804:
1778:
1588:
1422:incremental encoder interfaces
1360:) can be manually configured.
1315:
1249:system can signal or notify a
1151:, a serial computer bus, uses
1052:Industry Standard Architecture
967:
821:is an interrupt signaled by a
656:
475:an interrupt is to enable it.
13:
1:
2613:Arduino Pin change Interrupts
2535:Thusoo, Shalesh; et al.
2287:Digital Equipment Corporation
2264:Digital Equipment Corporation
2209:. October 11, 1966. 60021300K
1785:Rosenthal, Scott (May 1995).
1703:
1555:Interrupts in 65xx processors
640:Structured Exception Handling
2730:Just enough operating system
2715:Distributed operating system
1430:digital-to-analog converters
1418:analog-to-digital converters
345:National Bureau of Standards
267:(sometimes referred to as a
7:
2843:User space and kernel space
2564:Nios II Processor Reference
2561:Altera Corporation (2009).
2475:Jake Edge (April 7, 2010).
1839:. McGraw-Hill. p. 46.
1560:Ralf Brown's Interrupt List
1490:
1465:inter-process communication
1332:There are various forms of
1294:Message Signaled Interrupts
1158:
1153:message-signaled interrupts
1118:Message Signaled Interrupts
1003:conditions to do so are met
904:conditions to do so are met
10:
3172:
2750:Real-time operating system
2396:Linux kernel documentation
1995:. CRC Press. p. 163.
1912:"Interrupt Instructions".
1459:Interrupts are similar to
1374:inter-processor interrupts
1310:inter-processor interrupts
1124:message-signaled interrupt
1115:
660:
462:
424:. For example, pressing a
420:) or they may be external
315:
29:
3085:
3022:
2968:
2946:Multilevel feedback queue
2941:Fixed-priority preemptive
2929:
2864:
2855:
2825:
2772:
2763:
2725:Hobbyist operating system
2720:Embedded operating system
2702:
2656:
2451:"Receive packet steering"
2266:. 1979. pp. 128–131.
1938:. CRC Press. p. 21.
1609:Test Pending Interruption
1098:
796:level-triggered interrupt
731:is more common for this.
699:refers specifically to a
295:interrupt service routine
2989:General protection fault
2740:Network operating system
2694:User features comparison
2207:Control Data Corporation
1581:
1525:Event-driven programming
819:edge-triggered interrupt
618:this involves sending a
368:
2735:Mobile operating system
2477:"Receive flow steering"
1679:This might be just the
1365:receive packet steering
703:intended to initiate a
540:In a wired-OR circuit,
493:non-maskable interrupts
457:interrupt vector tables
271:) is a request for the
2838:Loadable kernel module
2602:IBM PC Interrupt Table
2430:. June 2014. p. 1
2073:. pp. 6–12 Vol. 1
2037:Hyde, Randall (1996).
1787:"Basics of Interrupts"
1687:or multiple registers.
1258:, or send them over a
651:operating system crash
377:
256:
164:
34:. For other uses, see
2906:Process control block
2872:Computer multitasking
2710:Disk operating system
2537:"Patent US 5632028 A"
2360:10.1145/263326.263335
2126:. p. 6-5 Vol. 3A
2017:"Hardware exceptions"
1893:"Hardware interrupts"
1816:Advances in Computers
1660:INT (x86 instruction)
1570:Time-triggered system
1535:INT (x86 instruction)
1378:Receive flow steering
869:System implementation
727:), although the term
721:invalid memory access
661:Further information:
542:parasitic capacitance
376:
302:computer multitasking
254:
163:
3077:Virtual tape library
2669:Forensic engineering
2592:Interrupts Made Easy
2172:"Types of exception"
2146:"Exception Handling"
1814:"Multiprogramming".
1748:Linux Device Drivers
1681:Program Counter (PC)
1540:Interrupt coalescing
1436:, and GPIO outputs.
1382:application locality
1345:receive-side scaling
1191:improve this section
518:Operating System/360
65:improve this article
3086:Supporting concepts
3072:Virtual file system
2502:"DECIMAL SIMULATOR"
2239:(Eighth ed.).
1520:BIOS interrupt call
1233:analogy applied to
990:of this section is
891:of this section is
572:Software interrupts
524:Spurious interrupts
516:As an example, IBM
513:to deal with this.
485:maskable interrupts
400:Hardware interrupts
394:software interrupts
390:hardware interrupts
310:real-time computing
3009:Segmentation fault
2857:Process management
2021:docs.microsoft.com
1972:"Interrupt Levels"
1932:Bai, Ying (2017).
1870:Smotherman, Mark.
1645:and other bits in
1530:Exception handling
1505:Electronics portal
1300:Multiprocessor IPI
1289:), if it has one.
1271:doorbell interrupt
1243:doorbell interrupt
1145:additional lines.
1137:Message-signalled
842:Processor response
836:interrupt register
781:Triggering methods
609:segmentation fault
530:spurious interrupt
508:Missing interrupts
378:
360:Lincoln Laboratory
257:
178:Process management
165:
3143:
3142:
2999:Memory protection
2970:Memory management
2964:
2963:
2956:Shortest job next
2851:
2850:
2650:Operating systems
2323:978-1-85617-963-8
2176:developer.arm.com
2150:developer.arm.com
2106:978-1-292-10176-7
1945:978-1-4987-7298-3
1647:control registers
1617:IBM System/370-XA
1615:) instruction of
1550:Interrupt latency
1545:Interrupt handler
1434:motor controllers
1369:interrupt handler
1251:computer hardware
1227:
1226:
1219:
1139:interrupt vectors
1031:
1030:
1023:
962:systems on a chip
951:memory controller
932:
931:
924:
616:operating systems
500:. With regard to
406:interrupt request
290:interrupt handler
261:digital computers
249:
248:
188:Memory management
147:Operating systems
141:
140:
133:
115:
16:(Redirected from
3163:
3098:Computer network
2862:
2861:
2770:
2769:
2643:
2636:
2629:
2620:
2619:
2580:
2579:
2577:
2575:
2569:
2558:
2552:
2551:
2549:
2547:
2532:
2526:
2525:
2523:
2521:
2515:
2506:
2498:
2492:
2491:
2489:
2487:
2472:
2466:
2465:
2463:
2461:
2446:
2440:
2439:
2437:
2435:
2425:
2417:
2411:
2410:
2408:
2406:
2387:
2378:
2377:
2375:
2374:
2339:
2333:
2332:
2331:
2330:
2297:
2291:
2290:
2284:
2274:
2268:
2267:
2261:
2251:
2245:
2244:
2238:
2228:
2219:
2218:
2216:
2214:
2204:
2194:
2188:
2187:
2185:
2183:
2168:
2162:
2161:
2159:
2157:
2142:
2136:
2135:
2133:
2131:
2120:
2111:
2110:
2092:
2083:
2082:
2080:
2078:
2067:
2058:
2057:
2051:
2049:
2034:
2025:
2024:
2023:. 3 August 2021.
2013:
2007:
2006:
1988:
1982:
1981:
1979:
1978:
1968:
1962:
1961:
1929:
1923:
1922:
1920:
1909:
1903:
1902:
1900:
1899:
1889:
1883:
1882:
1880:
1878:
1867:
1858:
1857:
1855:
1853:
1830:
1824:
1823:
1808:
1802:
1801:
1799:
1798:
1789:. Archived from
1782:
1776:
1775:
1772:
1766:
1764:
1754:
1741:
1732:
1731:
1729:
1727:
1716:
1697:
1694:
1688:
1677:
1671:
1668:
1662:
1656:
1650:
1639:
1633:
1626:
1620:
1605:
1599:
1592:
1507:
1502:
1501:
1338:operating system
1235:computer systems
1222:
1215:
1211:
1208:
1202:
1171:
1163:
1112:Message-signaled
1026:
1019:
1015:
1012:
1006:
980:
979:
972:
927:
920:
916:
913:
907:
881:
880:
873:
823:level transition
717:division by zero
586:subroutine calls
428:key or moving a
410:operating system
308:, especially in
283:, and execute a
241:
234:
227:
156:
143:
142:
136:
129:
125:
122:
116:
114:
73:
49:
41:
21:
3171:
3170:
3166:
3165:
3164:
3162:
3161:
3160:
3146:
3145:
3144:
3139:
3081:
3042:Defragmentation
3027:
3018:
3004:Protection ring
2973:
2960:
2932:
2925:
2847:
2821:
2759:
2698:
2652:
2647:
2588:
2583:
2573:
2571:
2567:
2559:
2555:
2545:
2543:
2533:
2529:
2519:
2517:
2513:
2504:
2500:
2499:
2495:
2485:
2483:
2473:
2469:
2459:
2457:
2447:
2443:
2433:
2431:
2423:
2419:
2418:
2414:
2404:
2402:
2388:
2381:
2372:
2370:
2340:
2336:
2328:
2326:
2324:
2298:
2294:
2282:
2276:
2275:
2271:
2259:
2253:
2252:
2248:
2236:
2230:
2229:
2222:
2212:
2210:
2202:
2196:
2195:
2191:
2181:
2179:
2170:
2169:
2165:
2155:
2153:
2144:
2143:
2139:
2129:
2127:
2122:
2121:
2114:
2107:
2093:
2086:
2076:
2074:
2069:
2068:
2061:
2047:
2045:
2035:
2028:
2015:
2014:
2010:
2003:
1989:
1985:
1976:
1974:
1970:
1969:
1965:
1946:
1930:
1926:
1918:
1911:
1910:
1906:
1897:
1895:
1891:
1890:
1886:
1876:
1874:
1868:
1861:
1851:
1849:
1847:
1831:
1827:
1809:
1805:
1796:
1794:
1783:
1779:
1770:
1762:
1760:
1752:
1742:
1735:
1725:
1723:
1718:
1717:
1710:
1706:
1701:
1700:
1695:
1691:
1678:
1674:
1669:
1665:
1657:
1653:
1640:
1636:
1627:
1623:
1606:
1602:
1593:
1589:
1584:
1579:
1503:
1496:
1493:
1390:
1349:multiqueue NICs
1327:interrupt storm
1318:
1302:
1256:hard disk drive
1223:
1212:
1206:
1203:
1188:
1172:
1161:
1120:
1114:
1101:
1076:
1027:
1016:
1010:
1007:
996:
981:
977:
970:
928:
917:
911:
908:
897:
882:
878:
871:
844:
815:
792:
790:Level-triggered
783:
709:monitor program
665:
659:
574:
526:
510:
465:
432:plugged into a
418:disk controller
402:
371:
318:
245:
170:Common features
162:
154:
137:
126:
120:
117:
74:
72:
62:
50:
39:
28:
23:
22:
15:
12:
11:
5:
3169:
3159:
3158:
3141:
3140:
3138:
3137:
3132:
3131:
3130:
3128:User interface
3125:
3115:
3110:
3105:
3100:
3095:
3089:
3087:
3083:
3082:
3080:
3079:
3074:
3069:
3064:
3059:
3054:
3052:File attribute
3049:
3044:
3039:
3033:
3031:
3020:
3019:
3017:
3016:
3014:Virtual memory
3011:
3006:
3001:
2996:
2991:
2986:
2980:
2978:
2966:
2965:
2962:
2961:
2959:
2958:
2953:
2948:
2943:
2937:
2935:
2927:
2926:
2924:
2923:
2918:
2913:
2908:
2903:
2898:
2893:
2888:
2886:Context switch
2883:
2868:
2866:
2859:
2853:
2852:
2849:
2848:
2846:
2845:
2840:
2835:
2829:
2827:
2823:
2822:
2820:
2819:
2814:
2809:
2804:
2799:
2794:
2789:
2784:
2778:
2776:
2767:
2761:
2760:
2758:
2757:
2752:
2747:
2742:
2737:
2732:
2727:
2722:
2717:
2712:
2706:
2704:
2700:
2699:
2697:
2696:
2691:
2686:
2681:
2676:
2671:
2666:
2660:
2658:
2654:
2653:
2646:
2645:
2638:
2631:
2623:
2617:
2616:
2610:
2604:
2599:
2594:
2587:
2586:External links
2584:
2582:
2581:
2553:
2541:Google Patents
2527:
2493:
2467:
2441:
2412:
2379:
2354:(3): 217–252.
2334:
2322:
2292:
2269:
2246:
2220:
2205:. Revision K.
2189:
2163:
2137:
2112:
2105:
2084:
2059:
2026:
2008:
2001:
1983:
1963:
1944:
1924:
1904:
1884:
1859:
1845:
1825:
1812:Codd, Edgar F.
1803:
1777:
1757:O'Reilly Media
1733:
1707:
1705:
1702:
1699:
1698:
1689:
1672:
1663:
1651:
1634:
1630:IBM System/360
1621:
1600:
1586:
1585:
1583:
1580:
1578:
1577:
1572:
1567:
1562:
1557:
1552:
1547:
1542:
1537:
1532:
1527:
1522:
1517:
1510:
1509:
1508:
1492:
1489:
1453:floating point
1389:
1386:
1317:
1314:
1306:multiprocessor
1301:
1298:
1225:
1224:
1175:
1173:
1166:
1160:
1157:
1116:Main article:
1113:
1110:
1100:
1097:
1093:hardware logic
1075:
1072:
1036:open collector
1029:
1028:
984:
982:
975:
969:
966:
930:
929:
885:
883:
876:
870:
867:
862:
861:
858:
855:
852:
843:
840:
814:
813:Edge-triggered
811:
791:
788:
782:
779:
755:uses the term
725:illegal opcode
705:context switch
658:
655:
594:virtual memory
590:device drivers
573:
570:
525:
522:
509:
506:
498:watchdog timer
480:interrupt mask
464:
461:
441:asynchronously
401:
398:
370:
367:
317:
314:
247:
246:
244:
243:
236:
229:
221:
218:
217:
216:
215:
210:
205:
200:
198:Device drivers
195:
190:
185:
180:
172:
171:
167:
166:
150:
149:
139:
138:
53:
51:
44:
26:
9:
6:
4:
3:
2:
3168:
3157:
3154:
3153:
3151:
3136:
3133:
3129:
3126:
3124:
3121:
3120:
3119:
3116:
3114:
3111:
3109:
3106:
3104:
3101:
3099:
3096:
3094:
3091:
3090:
3088:
3084:
3078:
3075:
3073:
3070:
3068:
3065:
3063:
3060:
3058:
3055:
3053:
3050:
3048:
3045:
3043:
3040:
3038:
3035:
3034:
3032:
3030:
3025:
3021:
3015:
3012:
3010:
3007:
3005:
3002:
3000:
2997:
2995:
2994:Memory paging
2992:
2990:
2987:
2985:
2982:
2981:
2979:
2976:
2971:
2967:
2957:
2954:
2952:
2949:
2947:
2944:
2942:
2939:
2938:
2936:
2934:
2928:
2922:
2919:
2917:
2914:
2912:
2909:
2907:
2904:
2902:
2899:
2897:
2894:
2892:
2889:
2887:
2884:
2881:
2877:
2873:
2870:
2869:
2867:
2863:
2860:
2858:
2854:
2844:
2841:
2839:
2836:
2834:
2833:Device driver
2831:
2830:
2828:
2824:
2818:
2815:
2813:
2810:
2808:
2805:
2803:
2800:
2798:
2795:
2793:
2790:
2788:
2785:
2783:
2780:
2779:
2777:
2775:
2774:Architectures
2771:
2768:
2766:
2762:
2756:
2753:
2751:
2748:
2746:
2743:
2741:
2738:
2736:
2733:
2731:
2728:
2726:
2723:
2721:
2718:
2716:
2713:
2711:
2708:
2707:
2705:
2701:
2695:
2692:
2690:
2687:
2685:
2682:
2680:
2677:
2675:
2672:
2670:
2667:
2665:
2662:
2661:
2659:
2655:
2651:
2644:
2639:
2637:
2632:
2630:
2625:
2624:
2621:
2614:
2611:
2608:
2605:
2603:
2600:
2598:
2595:
2593:
2590:
2589:
2566:
2565:
2557:
2542:
2538:
2531:
2512:
2511:
2503:
2497:
2482:
2478:
2471:
2456:
2452:
2445:
2429:
2422:
2416:
2401:
2397:
2393:
2386:
2384:
2369:
2365:
2361:
2357:
2353:
2349:
2345:
2338:
2325:
2319:
2315:
2311:
2307:
2303:
2296:
2288:
2281:
2280:
2273:
2265:
2258:
2257:
2250:
2242:
2235:
2234:
2227:
2225:
2208:
2201:
2200:
2193:
2177:
2173:
2167:
2151:
2147:
2141:
2125:
2119:
2117:
2108:
2102:
2098:
2091:
2089:
2072:
2066:
2064:
2056:
2044:
2040:
2033:
2031:
2022:
2018:
2012:
2004:
1998:
1994:
1987:
1973:
1967:
1960:
1955:
1951:
1947:
1941:
1937:
1936:
1928:
1917:
1916:
1908:
1894:
1888:
1873:
1866:
1864:
1848:
1846:9780070043572
1842:
1838:
1837:
1829:
1821:
1817:
1813:
1807:
1793:on 2016-04-26
1792:
1788:
1781:
1774:
1759:. p. 269
1758:
1751:
1749:
1740:
1738:
1721:
1715:
1713:
1708:
1693:
1686:
1682:
1676:
1667:
1661:
1655:
1648:
1644:
1638:
1631:
1625:
1618:
1614:
1610:
1604:
1597:
1591:
1587:
1576:
1573:
1571:
1568:
1566:
1563:
1561:
1558:
1556:
1553:
1551:
1548:
1546:
1543:
1541:
1538:
1536:
1533:
1531:
1528:
1526:
1523:
1521:
1518:
1515:
1512:
1511:
1506:
1500:
1495:
1488:
1486:
1482:
1478:
1474:
1470:
1466:
1462:
1457:
1454:
1449:
1447:
1443:
1437:
1435:
1431:
1427:
1423:
1419:
1415:
1411:
1405:
1403:
1399:
1395:
1385:
1383:
1379:
1375:
1370:
1366:
1361:
1359:
1354:
1350:
1346:
1341:
1339:
1335:
1330:
1328:
1323:
1313:
1311:
1307:
1297:
1295:
1290:
1288:
1284:
1280:
1276:
1273:is usually a
1272:
1267:
1265:
1261:
1257:
1252:
1248:
1244:
1240:
1236:
1232:
1221:
1218:
1210:
1207:December 2020
1200:
1196:
1192:
1186:
1185:
1181:
1176:This section
1174:
1170:
1165:
1164:
1156:
1155:exclusively.
1154:
1150:
1146:
1142:
1140:
1135:
1131:
1129:
1125:
1119:
1109:
1105:
1096:
1094:
1090:
1084:
1082:
1071:
1067:
1065:
1059:
1057:
1056:parallel port
1053:
1048:
1044:
1041:
1037:
1025:
1022:
1014:
1011:December 2021
1004:
1000:
994:
993:
989:
983:
974:
973:
965:
963:
958:
956:
955:address space
952:
948:
943:
941:
937:
926:
923:
915:
905:
901:
895:
894:
890:
884:
875:
874:
866:
859:
856:
853:
850:
849:
848:
839:
837:
832:
829:
824:
820:
810:
806:
803:
801:
797:
787:
778:
776:
772:
770:
766:
762:
758:
754:
750:
748:
744:
741:and software
740:
736:
732:
730:
726:
722:
718:
714:
710:
706:
702:
698:
694:
690:
686:
682:
678:
674:
670:
664:
654:
652:
648:
643:
641:
637:
633:
629:
625:
621:
617:
614:
610:
606:
602:
597:
595:
591:
587:
583:
578:
569:
565:
563:
562:device errata
559:
555:
551:
546:
543:
538:
536:
531:
521:
519:
514:
505:
503:
499:
495:
494:
488:
486:
481:
476:
474:
470:
460:
458:
454:
449:
445:
442:
437:
435:
431:
427:
423:
419:
415:
411:
407:
397:
395:
391:
387:
383:
375:
366:
364:
361:
357:
353:
349:
346:
342:
338:
334:
329:
327:
323:
322:polling loops
313:
311:
307:
303:
298:
296:
292:
291:
286:
282:
278:
274:
270:
266:
262:
253:
242:
237:
235:
230:
228:
223:
222:
220:
219:
214:
211:
209:
206:
204:
201:
199:
196:
194:
191:
189:
186:
184:
181:
179:
176:
175:
174:
173:
169:
168:
152:
151:
148:
145:
144:
135:
132:
124:
121:February 2014
113:
110:
106:
103:
99:
96:
92:
89:
85:
82: –
81:
77:
76:Find sources:
70:
66:
60:
59:
54:This article
52:
48:
43:
42:
37:
33:
19:
3029:file systems
2921:Time-sharing
2890:
2572:. Retrieved
2563:
2556:
2544:. Retrieved
2540:
2530:
2520:September 2,
2518:. Retrieved
2509:
2496:
2486:November 16,
2484:. Retrieved
2470:
2460:November 16,
2458:. Retrieved
2444:
2434:November 16,
2432:. Retrieved
2415:
2405:November 16,
2403:. Retrieved
2395:
2371:. Retrieved
2351:
2347:
2337:
2327:, retrieved
2305:
2295:
2289:. p. 4.
2278:
2272:
2255:
2249:
2232:
2211:. Retrieved
2198:
2192:
2180:. Retrieved
2175:
2166:
2154:. Retrieved
2149:
2140:
2128:. Retrieved
2096:
2075:. Retrieved
2053:
2046:. Retrieved
2042:
2020:
2011:
1992:
1986:
1975:. Retrieved
1966:
1957:
1934:
1927:
1914:
1907:
1896:. Retrieved
1887:
1875:. Retrieved
1872:"Interrupts"
1850:. Retrieved
1835:
1828:
1819:
1815:
1806:
1795:. Retrieved
1791:the original
1780:
1768:
1763:December 25,
1761:. Retrieved
1747:
1724:. Retrieved
1722:. 2003-10-27
1692:
1675:
1666:
1654:
1637:
1624:
1612:
1608:
1603:
1590:
1458:
1450:
1438:
1406:
1391:
1388:Typical uses
1377:
1364:
1362:
1358:IRQ affinity
1357:
1342:
1331:
1319:
1303:
1291:
1270:
1268:
1242:
1238:
1228:
1213:
1204:
1189:Please help
1177:
1147:
1143:
1136:
1132:
1128:computer bus
1123:
1121:
1106:
1102:
1085:
1077:
1068:
1064:oscilloscope
1060:
1049:
1045:
1032:
1017:
1008:
986:
959:
944:
933:
918:
912:January 2022
909:
887:
863:
845:
835:
833:
818:
816:
807:
804:
795:
793:
784:
773:
768:
764:
760:
756:
751:
747:system calls
742:
738:
733:
728:
696:
692:
688:
684:
680:
676:
672:
668:
666:
653:may result.
645:In a kernel
644:
598:
579:
575:
566:
547:
539:
529:
527:
515:
511:
491:
489:
484:
479:
477:
472:
468:
466:
450:
446:
438:
403:
393:
389:
379:
333:UNIVAC 1103A
330:
319:
306:system calls
299:
294:
288:
276:
268:
264:
258:
213:Input/output
182:
127:
118:
108:
101:
94:
87:
75:
63:Please help
58:verification
55:
36:Interruption
3047:Device file
3037:Boot loader
2951:Round-robin
2876:Cooperative
2812:Rump kernel
2802:Multikernel
2792:Microkernel
2689:Usage share
2570:. p. 4
2182:22 December
2130:22 December
2077:22 December
2048:22 December
1877:22 December
1347:(RSS) when
1316:Performance
1266:them, etc.
1237:, the term
1231:push button
1149:PCI Express
1081:PCI Express
968:Shared IRQs
940:southbridge
800:logic level
657:Terminology
582:instruction
422:peripherals
193:File system
80:"Interrupt"
3156:Interrupts
2977:protection
2933:algorithms
2931:Scheduling
2880:Preemptive
2826:Components
2797:Monolithic
2664:Comparison
2400:kernel.org
2373:2010-11-11
2329:2023-10-11
2156:21 January
2002:1482280825
1977:2023-11-17
1954:2016020120
1898:2014-02-09
1797:2010-11-11
1726:20 January
1704:References
1619:and later.
1442:keystrokes
988:neutrality
889:neutrality
828:polled I/O
761:interrupts
743:exceptions
739:interrupts
701:breakpoint
667:The terms
605:page fault
414:bare metal
287:called an
203:Networking
183:Interrupts
91:newspapers
18:Interrupts
3067:Partition
2984:Bus error
2911:Real-time
2891:Interrupt
2817:Unikernel
2782:Exokernel
2368:215749380
1446:typeahead
1414:processes
1410:scheduler
1376:(IPIs).
1334:livelocks
1283:registers
1269:The term
1178:does not
1040:pull cord
999:talk page
947:multiplex
900:talk page
757:exception
729:exception
677:exception
669:interrupt
613:Unix-like
558:crosstalk
550:anomalies
434:PS/2 port
356:debugging
277:interrupt
273:processor
265:interrupt
3150:Category
3113:Live USB
2975:resource
2865:Concepts
2703:Variants
2684:Timeline
1491:See also
1398:Ethernet
1275:misnomer
1247:software
1239:doorbell
1159:Doorbell
992:disputed
893:disputed
713:debugger
622:such as
596:system.
556:levels,
535:wired-OR
453:CDC 3600
426:keyboard
386:software
382:hardware
337:UNIVAC I
285:function
208:Security
3108:Live CD
3062:Journal
3026:access,
3024:Storage
2901:Process
2807:vkernel
2674:History
2657:General
2574:Aug 13,
2546:Aug 13,
2481:LWN.net
2455:LWN.net
2213:May 17,
1852:Feb 18,
1771:wake_up
1596:process
1473:SIGSEGV
1461:signals
1322:latency
1312:(IPI).
1264:encrypt
1260:network
1199:removed
1184:sources
647:process
624:SIGSEGV
463:Masking
352:IBM 704
341:IBM 650
316:History
293:(or an
105:scholar
2916:Thread
2787:Hybrid
2765:Kernel
2366:
2320:
2103:
1999:
1952:
1942:
1843:
1516:(APIC)
1485:SIGFPE
1481:SIGILL
1477:SIGBUS
1469:kernel
1424:, and
1353:queues
1279:polled
1099:Hybrid
1087:line.
775:RISC-V
765:aborts
683:, and
636:SIGFPE
632:SIGILL
628:SIGBUS
620:signal
601:kernel
473:unmask
348:DYSEAC
326:DYSEAC
107:
100:
93:
86:
78:
3118:Shell
3057:Inode
2568:(PDF)
2514:(PDF)
2505:(PDF)
2428:Intel
2424:(PDF)
2364:S2CID
2283:(PDF)
2260:(PDF)
2237:(PDF)
2203:(PDF)
1959:occur
1919:(PDF)
1822:: 82.
1753:(PDF)
1582:Notes
1402:traps
1262:, or
1229:In a
938:or a
769:reset
707:to a
685:abort
681:fault
554:noise
502:SPARC
430:mouse
369:Types
281:state
263:, an
112:JSTOR
98:books
2679:List
2576:2017
2548:2017
2522:2024
2488:2014
2462:2014
2436:2014
2407:2014
2318:ISBN
2215:2023
2184:2021
2158:2022
2132:2021
2101:ISBN
2079:2021
2050:2021
1997:ISBN
1950:LCCN
1940:ISBN
1879:2021
1854:2019
1841:ISBN
1765:2014
1728:2022
1683:, a
1658:See
1483:and
1426:GPIO
1394:UART
1182:any
1180:cite
1050:The
985:The
886:The
697:trap
693:trap
689:trap
673:trap
469:mask
363:TX-2
331:The
304:and
269:trap
84:news
3135:PXE
3123:CLI
3103:HAL
3093:API
2896:IPC
2356:doi
2310:doi
2241:IBM
1685:PSW
1643:PSW
1613:TPI
1487:).
1304:In
1287:CPU
1241:or
1193:by
1089:ISA
960:In
817:An
753:Arm
735:x86
711:or
634:or
467:To
392:or
384:or
275:to
259:In
67:by
3152::
2878:,
2539:.
2507:.
2479:.
2453:.
2426:.
2398:.
2394:.
2382:^
2362:.
2352:15
2350:.
2346:.
2316:,
2304:,
2285:.
2262:.
2223:^
2174:.
2148:.
2115:^
2087:^
2062:^
2052:.
2041:.
2029:^
2019:.
1956:.
1948:.
1862:^
1818:.
1767:.
1755:.
1736:^
1711:^
1479:,
1475:,
1448:.
1432:,
1420:,
1404:.
1396:,
1329:.
1122:A
957:.
942:.
794:A
767:,
763:,
723:,
719:,
679:,
675:,
671:,
630:,
626:,
564:.
528:A
487:.
459:.
2972:,
2882:)
2874:(
2642:e
2635:t
2628:v
2578:.
2550:.
2524:.
2490:.
2464:.
2438:.
2409:.
2376:.
2358::
2312::
2217:.
2186:.
2160:.
2134:.
2109:.
2081:.
2005:.
1980:.
1901:.
1881:.
1856:.
1820:3
1800:.
1746:"
1730:.
1649:.
1611:(
1220:)
1214:(
1209:)
1205:(
1201:.
1187:.
1024:)
1018:(
1013:)
1009:(
1005:.
995:.
925:)
919:(
914:)
910:(
906:.
896:.
240:e
233:t
226:v
134:)
128:(
123:)
119:(
109:·
102:·
95:·
88:·
61:.
38:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.