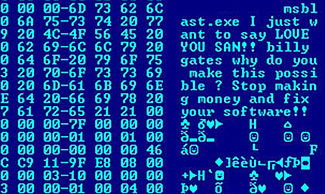
155:. In the novel, Nichlas Haflinger designs and sets off a data-gathering worm in an act of revenge against the powerful men who run a national electronic information web that induces mass conformity. "You have the biggest-ever worm loose in the net, and it automatically sabotages any attempt to monitor it. There's never been a worm with that tough a head or that long a tail!" "Then the answer dawned on him, and he almost laughed. Fluckner had resorted to one of the oldest tricks in the store and turned loose in the continental net a self-perpetuating tapeworm, probably headed by a denunciation group "borrowed" from a major corporation, which would shunt itself from one nexus to another every time his credit-code was punched into a keyboard. It could take days to kill a worm like that, and sometimes weeks."
2372:
1731:
74:
132:
189:, disrupting many computers then on the Internet, guessed at the time to be one tenth of all those connected. During the Morris appeal process, the U.S. Court of Appeals estimated the cost of removing the worm from each installation at between $ 200 and $ 53,000; this work prompted the formation of the
499:
family of worms tried to download and install patches from
Microsoft's website to fix vulnerabilities in the host system by exploiting those same vulnerabilities. In practice, although this may have made these systems more secure, it generated considerable network traffic, rebooted the machine in the
359:
systems to attack the embedded programmable logic controllers of industrial machines. Although these systems operate independently from the network, if the operator inserts a virus-infected drive into the system's USB interface, the virus will be able to gain control of the system without any other
221:
Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A worm does not need a host program, as it is an independent program or code chunk. Therefore, it
207:
operating systems, is a worm that employs 3 different spreading strategies: local probing, neighborhood probing, and global probing. This worm was considered a hybrid epidemic and affected millions of computers. The term "hybrid epidemic" is used because of the three separate methods it employed to
99:
to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts,
347:
was primarily transmitted through LANs and infected thumb-drives, as its targets were never connected to untrusted networks, like the internet. This virus can destroy the core production control computer software used by chemical, power generation and power transmission companies in various
348:
countries around the world - in
Stuxnet's case, Iran, Indonesia and India were hardest hit - it was used to "issue orders" to other equipment in the factory, and to hide those commands from being detected. Stuxnet used multiple vulnerabilities and four different zero-day exploits (e.g.:
49:
462:
Infections can sometimes be detected by their behavior - typically scanning the
Internet randomly, looking for vulnerable hosts to infect. In addition, machine learning techniques can be used to detect new worms, by analyzing the behavior of the suspected computer.
285:
Worms are more infectious than traditional viruses. They not only infect local computers, but also all servers and clients on the network based on the local computer. Worms can easily spread through
479:
is a worm designed to do something that its author feels is helpful, though not necessarily with the permission of the executing computer's owner. Beginning with the first research into worms at
265:
and other technologies. When a user accesses a webpage containing a virus, the virus automatically resides in memory and waits to be triggered. There are also some worms that are combined with
500:
course of patching it, and did its work without the consent of the computer's owner or user. Regardless of their payload or their writers' intentions, security experts regard all worms as
404:
Users can minimize the threat posed by worms by keeping their computers' operating system and other software up to date, avoiding opening unrecognized or unexpected emails and running
372:"), and if these are installed to a machine, then the majority of worms are unable to spread to it. If a vulnerability is disclosed before the security patch released by the vendor, a
508:
patching a bug allowing for Roku OS to be rooted via an update to their screensaver channels, which the screensaver would attempt to connect to the telnet and patch the device.
100:
and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of
550:
without the users' consent. Welchia automatically reboots the computers it infects after installing the updates. One of these updates was the patch that fixed the exploit.
379:
Users need to be wary of opening unexpected emails, and should not run attached files or programs, or visit web sites that are linked to such emails. However, as with the
234:
Because a worm is not limited by the host program, worms can take advantage of various operating system vulnerabilities to carry out active attacks. For example, the "
1316:
104:, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming
556:
Art worms support artists in the performance of massive scale ephemeral artworks. It turns the infected computers into nodes that contribute to the artwork.
519:(CAM) tables and Spanning Tree information stored in switches to propagate and probe for vulnerable nodes until the enterprise network is covered.
2266:
1641:
Moskovitch, Robert; Elovici, Yuval; Rokach, Lior (2008). "Detection of unknown computer worms based on behavioral classification of the host".
2106:
368:
Worms spread by exploiting vulnerabilities in operating systems. Vendors with security problems supply regular security updates (see "
2810:
1880:
1150:
Yu, Wei; Zhang, Nan; Fu, Xinwen; Zhao, Wei (October 2010). "Self-Disciplinary Worms and
Countermeasures: Modeling and Analysis".
661:
1958:
621:
123:
showed, even these "payload-free" worms can cause major disruption by increasing network traffic and other unintended effects.
2787:
1768:
1488:
1210:
1126:
923:
837:
1886:
1525:
2818:
1324:
2259:
1864:
2750:
2223:
1914:
618:– unsolicited phone calls from a fake "tech support" person, claiming that the computer has a virus or other problems
585:
570:
115:
Many worms are designed only to spread, and do not attempt to change the systems they pass through. However, as the
2546:
605:
2800:
2111:
1751:
Al-Salloum, Z. S.; Wolthusen, S. D. (2010). "A link-layer-based self-replicating vulnerability discovery agent".
450:
1792:
1938:
397:
software are helpful, but must be kept up-to-date with new pattern files at least every few days. The use of a
889:
2613:
2252:
2177:
17:
194:
2805:
2726:
2526:
1469:
Wang, Guangwei; Pan, Hong; Fan, Mingyu (2014). "Dynamic
Analysis of a Suspected Stuxnet Malicious Code".
415:
239:
1867:(archived link) – Guide for understanding, removing and preventing worm infections on Vernalex.com.
2852:
2782:
2740:
2396:
2197:
516:
441:
2857:
2643:
2361:
2065:
641:
242:
2628:
2506:
2401:
1999:
1989:
626:
610:
523:
337:
274:
270:
190:
770:
Philosophical
Transactions of the Royal Society A: Mathematical, Physical and Engineering Sciences
349:
193:
and Phage mailing list. Morris himself became the first person tried and convicted under the 1986
2847:
2716:
2668:
2331:
2075:
146:
139:
56:
1589:
Sellke, S. H.; Shroff, N. B.; Bagchi, S. (2008). "Modeling and
Automated Containment of Worms".
2126:
1953:
615:
565:
2060:
1197:, Undergraduate Topics in Computer Science, Springer International Publishing, pp. 1–10,
2757:
2491:
1907:
1677:
428:
105:
35:
1226:
2777:
2689:
2638:
2583:
2451:
2424:
2406:
2304:
2275:
2233:
2228:
2187:
2116:
1974:
1347:
1039:
962:
777:
710:
405:
398:
321:
266:
178:
31:
2371:
1815:
293:, malicious web pages, and servers with a large number of vulnerabilities in the network.
8:
2561:
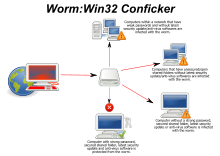
2336:
2294:
2182:
580:
446:
151:
1383:
Bronk, Christopher; Tikk-Ringas, Eneken (May 2013). "The Cyber Attack on Saudi Aramco".
1043:
966:
781:
714:
553:
Other examples of helpful worms are "Den_Zuko", "Cheeze", "CodeGreen", and "Millenium".
2745:
2673:
2578:
2167:
2004:
1984:
1774:
1699:
1658:
1451:
1408:
1297:
1254:
1175:
1070:
1029:
1017:
993:
952:
940:
741:
700:
688:
419:
390:
302:
182:
101:
1471:
Proceedings of the 3rd
International Conference on Computer Science and Service System
665:
2793:
2551:
2486:
2436:
2383:
2341:
2289:
2192:
2146:
2055:
1764:
1484:
1455:
1443:
1412:
1400:
1289:
1258:
1246:
1206:
1167:
1132:
1122:
1075:
1057:
998:
980:
919:
833:
826:
803:
795:
746:
728:
595:
547:
204:
171:
1365:
1301:
511:
One study proposed the first computer worm that operates on the second layer of the
2762:
2702:
2466:
2456:
2351:
2207:
2172:
1900:
1778:
1756:
1703:
1689:
1662:
1650:
1598:
1474:
1435:
1392:
1281:
1238:
1227:"Parameter estimation of a susceptible–infected–recovered–dead computer worm model"
1198:
1179:
1159:
1065:
1047:
1016:
Zhang, Changwang; Zhou, Shi; Chain, Benjamin M. (2015-05-15). Sun, Gui-Quan (ed.).
988:
970:
785:
736:
718:
631:
325:
301:
Any code designed to do more than spread the worm is typically referred to as the "
223:
159:
96:
92:
871:
538:
is an example of a helpful worm. Utilizing the same deficiencies exploited by the
2653:
2633:
2531:
2356:
2346:
2202:
2141:
2045:
1883:, Unclassified report from the U.S. National Security Agency (NSA), 18 June 2004.
1568:
1439:
1396:
1119:
Computer science and its applications : CSA 2012, Jeju, Korea, 22-25.11.2012
1052:
975:
723:
373:
1202:
387:
attacks, it remains possible to trick the end-user into running malicious code.
332:
and are very commonly used for a range of malicious purposes, including sending
2823:
2721:
2571:
2521:
2496:
2461:
2441:
2321:
2309:
2162:
2136:
1943:
1654:
1529:
853:
590:
437:
423:
109:
78:
42:
1760:
1550:
1242:
324:. This allows the computer to be remotely controlled by the worm author as a "
158:
The second ever computer worm was devised to be an anti-virus software. Named
95:
that replicates itself in order to spread to other computers. It often uses a
2841:
2733:
2694:
2663:
2511:
2501:
2471:
2121:
2040:
1447:
1404:
1293:
1250:
1171:
1136:
1061:
984:
799:
732:
369:
356:
305:". Typical malicious payloads might delete files on a host system (e.g., the
286:
163:
1871:"The 'Worm' Programs – Early Experience with a Distributed Computation"
1616:
1602:
1479:
2767:
2623:
2326:
1979:
1870:
1079:
1002:
807:
790:
765:
750:
539:
527:
1889:(archived link), paper by Jago Maniscalchi on Digital Threat, 31 May 2009.
1840:
1694:
1163:
2707:
2541:
2516:
2481:
2316:
2131:
2050:
1717:
433:
394:
333:
186:
135:
116:
30:
This article is about coding of a worm. For the data storage device, see
1426:
Lindsay, Jon R. (July 2013). "Stuxnet and the Limits of Cyber
Warfare".
1317:"Business & Technology: E-mail viruses blamed as spam rises sharply"
1285:
1093:
2772:
2588:
2536:
2419:
2299:
2244:
2090:
2070:
2035:
1678:"The "Worm" Programs - Early Experience with a Distributed Computation"
600:
496:
492:
484:
483:, there have been attempts to create useful worms. Those worms allowed
480:
314:
310:
306:
66:
185:
computer science graduate student, unleashed what became known as the
2648:
2603:
2598:
2446:
2414:
2080:
2030:
1796:
543:
512:
456:
200:
60:
2608:
2566:
2429:
893:
636:
488:
384:
380:
343:
Some special worms attack industrial systems in a targeted manner.
258:
52:
1272:
Lawton, George (June 2009). "On the Trail of the
Conficker Worm".
1034:
957:
705:
2618:
2593:
2556:
2085:
1994:
1923:
1892:
542:, Welchia infected computers and automatically began downloading
535:
505:
501:
352:
344:
329:
262:
253:
Some worms are combined with web page scripts, and are hidden in
167:
89:
48:
2476:
2391:
2025:
2020:
1736:
575:
120:
939:
Zhang, Changwang; Zhou, Shi; Chain, Benjamin M. (2015-05-15).
687:
Zhang, Changwang; Zhou, Shi; Chain, Benjamin M. (2015-05-15).
131:
112:
almost always corrupt or modify files on a targeted computer.
531:
290:
235:
203:, a computer worm discovered in 2008 that primarily targeted
1617:"A New Way to Protect Computer Networks from Internet Worms"
1551:"Email-Worm:VBS/LoveLetter Description | F-Secure Labs"
1504:
226:, but can run independently and actively carry out attacks.
73:
1094:"Worm vs. Virus: What's the Difference and Does It Matter?"
254:
1018:"Hybrid Epidemics—A Case Study on Computer Worm Conficker"
941:"Hybrid Epidemics—A Case Study on Computer Worm Conficker"
689:"Hybrid Epidemics—A Case Study on Computer Worm Conficker"
515:(Data link Layer), utilizing topology information such as
1098:
Worm vs. Virus: What's the Difference and Does It Matter?
63:
1640:
522:
Anti-worms have been used to combat the effects of the
383:
worm, and with the increased growth and efficiency of
328:". Networks of such machines are often referred to as
1225:
Deng, Yue; Pei, Yongzhen; Li, Changguo (2021-11-09).
1152:
IEEE Transactions on Parallel and Distributed Systems
1591:
IEEE Transactions on Dependable and Secure Computing
208:
spread, which was discovered through code analysis.
1881:"The Case for Using Layered Defenses to Stop Worms"
1877:, Volume 25 Issue 3 (March 1982), pp. 172–180.
1793:"vnunet.com 'Anti-worms' fight off Code Red threat"
1750:
1753:The IEEE symposium on Computers and Communications
1588:
825:
2839:
1473:. Vol. 109. Paris, France: Atlantis Press.
1382:
914:Dressler, J. (2007). "United States v. Morris".
1116:
1015:
938:
686:
2260:
1908:
1744:
1569:"Computer Worm Information and Removal Steps"
1193:Brooks, David R. (2017), "Introducing HTML",
1149:
317:such as confidential documents or passwords.
1643:Computational Statistics & Data Analysis
2267:
2253:
1915:
1901:
1468:
1345:
766:"From Turing machines to computer viruses"
2811:Security information and event management
1693:
1675:
1478:
1224:
1069:
1051:
1033:
992:
974:
956:
789:
740:
722:
704:
466:
174:program (the first computer worm, 1971).
2274:
1810:
1808:
1806:
913:
130:
72:
47:
1425:
823:
14:
2840:
1959:Timeline of computer viruses and worms
1838:
1271:
1192:
763:
622:Timeline of computer viruses and worms
504:. Another example of this approach is
2788:Host-based intrusion detection system
2248:
1896:
1803:
1346:McWilliams, Brian (October 9, 2003).
360:operational requirements or prompts.
892:. securitydigest.org. Archived from
819:
817:
2819:Runtime application self-protection
1676:Shoch, John; Hupp, Jon (Mar 1982).
1348:"Cloaking Device Made for Spammers"
1314:
916:Cases and Materials on Criminal Law
659:
138:source code floppy diskette at the
24:
2370:
1922:
1718:"Virus alert about the Nachi worm"
1366:"Hacker threats to bookies probed"
1315:Ray, Tiernan (February 18, 2004).
363:
145:The term "worm" was first used in
25:
2869:
2751:Security-focused operating system
2224:Computer and network surveillance
1858:
814:
586:Computer and network surveillance
2547:Insecure direct object reference
764:Marion, Jean-Yves (2012-07-28).
606:Father Christmas (computer worm)
27:Self-replicating malware program
2801:Information security management
1832:
1785:
1724:
1710:
1669:
1634:
1609:
1582:
1561:
1543:
1526:"Threat Description Email-Worm"
1518:
1497:
1462:
1419:
1376:
1358:
1339:
1308:
1265:
1218:
1186:
1143:
1110:
1086:
1009:
491:principles on their network of
411:Mitigation techniques include:
166:to replicate itself across the
1939:Comparison of computer viruses
1851:(2): 112–113 – via MUSE.
1820:. December 18, 2003. p. 1
1795:. Sep 14, 2001. Archived from
932:
918:. St. Paul, MN: Thomson/West.
907:
882:
864:
846:
832:. New York: Ballantine Books.
757:
680:
653:
13:
1:
2178:Data loss prevention software
647:
59:, showing a message left for
1440:10.1080/09636412.2013.816122
1397:10.1080/00396338.2013.784468
1053:10.1371/journal.pone.0127478
976:10.1371/journal.pone.0127478
724:10.1371/journal.pone.0127478
195:Computer Fraud and Abuse Act
170:and delete the experimental
7:
2806:Information risk management
2727:Multi-factor authentication
2283:Related security categories
1873:, John Shoch and Jon Hupp,
1839:Aycock, John (2022-09-15).
1203:10.1007/978-3-319-56973-4_1
1195:Programming in HTML and PHP
662:"What is an internet worm?"
559:
211:
10:
2874:
2783:Intrusion detection system
2741:Computer security software
2397:Advanced persistent threat
2198:Intrusion detection system
1655:10.1016/j.csda.2008.01.028
872:"Security of the Internet"
517:Content-addressable memory
495:computers. Similarly, the
309:worm), encrypt files in a
126:
40:
29:
2682:
2382:
2368:
2362:Digital rights management
2282:
2216:
2155:
2099:
2066:Privacy-invasive software
2013:
1967:
1931:
1875:Communications of the ACM
1761:10.1109/ISCC.2010.5546723
1682:Communications of the ACM
1243:10.1177/00375497211009576
1121:. Springer. p. 515.
642:Zombie (computer science)
487:and Jon Hupp to test the
320:Some worms may install a
222:is not restricted by the
2507:Denial-of-service attack
2402:Arbitrary code execution
627:Trojan horse (computing)
611:Self-replicating machine
440:enabled network service
408:and antivirus software.
191:CERT Coordination Center
41:Not to be confused with
2717:Computer access control
2669:Rogue security software
2332:Electromagnetic warfare
2076:Rogue security software
1841:"Painting the Internet"
1603:10.1109/tdsc.2007.70230
1480:10.2991/csss-14.2014.86
1117:Yeo, Sang-Soo. (2012).
296:
140:Computer History Museum
2763:Obfuscation (software)
2492:Browser Helper Objects
2376:
2112:Classic Mac OS viruses
1954:List of computer worms
1571:. Veracode. 2014-02-02
824:Brunner, John (1975).
791:10.1098/rsta.2011.0332
616:Technical support scam
566:List of computer worms
467:Worms with good intent
142:
81:
70:
34:. For other uses, see
2758:Data-centric security
2639:Remote access trojans
2374:
1695:10.1145/358453.358455
1164:10.1109/tpds.2009.161
664:. BBC. Archived from
546:security updates for
401:is also recommended.
177:On November 2, 1988,
134:
76:
69:by the worm's creator
51:
36:Worm (disambiguation)
2690:Application security
2584:Privilege escalation
2452:Cross-site scripting
2305:Cybersex trafficking
2276:Information security
2234:Operation: Bot Roast
1372:. February 23, 2004.
890:"Phage mailing list"
179:Robert Tappan Morris
162:, it was created by
32:write once read many
2337:Information warfare
2295:Automotive security
2183:Defensive computing
2100:By operating system
1286:10.1109/mc.2009.198
1044:2015PLoSO..1027478Z
967:2015PLoSO..1027478Z
828:The Shockwave Rider
782:2012RSPTA.370.3319M
776:(1971): 3319–3339.
715:2015PLoSO..1027478Z
581:Code Shikara (Worm)
152:The Shockwave Rider
2746:Antivirus software
2614:Social engineering
2579:Polymorphic engine
2532:Fraudulent dialers
2437:Hardware backdoors
2377:
2168:Antivirus software
2014:Malware for profit
1985:Man-in-the-browser
1932:Infectious malware
1327:on August 26, 2012
858:www.paulgraham.com
183:Cornell University
143:
102:exponential growth
82:
71:
2853:Security breaches
2832:
2831:
2794:Anomaly detection
2699:Secure by default
2552:Keystroke loggers
2487:Drive-by download
2375:vectorial version
2342:Internet security
2290:Computer security
2242:
2241:
2193:Internet security
2147:HyperCard viruses
2056:Keystroke logging
2046:Fraudulent dialer
1990:Man-in-the-middle
1770:978-1-4244-7754-8
1490:978-94-6252-012-7
1321:The Seattle Times
1212:978-3-319-56972-7
1158:(10): 1501–1514.
1128:978-94-007-5699-1
925:978-0-314-17719-3
839:978-0-06-010559-4
596:Computer security
205:Microsoft Windows
16:(Redirected from
2865:
2858:Types of malware
2703:Secure by design
2634:Hardware Trojans
2467:History sniffing
2457:Cross-site leaks
2352:Network security
2269:
2262:
2255:
2246:
2245:
2208:Network security
2173:Browser security
1917:
1910:
1903:
1894:
1893:
1853:
1852:
1836:
1830:
1829:
1827:
1825:
1817:The Welchia Worm
1812:
1801:
1800:
1789:
1783:
1782:
1748:
1742:
1741:
1728:
1722:
1721:
1714:
1708:
1707:
1697:
1673:
1667:
1666:
1649:(9): 4544–4566.
1638:
1632:
1631:
1629:
1627:
1613:
1607:
1606:
1586:
1580:
1579:
1577:
1576:
1565:
1559:
1558:
1555:www.f-secure.com
1547:
1541:
1540:
1538:
1537:
1528:. Archived from
1522:
1516:
1515:
1513:
1512:
1501:
1495:
1494:
1482:
1466:
1460:
1459:
1428:Security Studies
1423:
1417:
1416:
1380:
1374:
1373:
1362:
1356:
1355:
1343:
1337:
1336:
1334:
1332:
1323:. Archived from
1312:
1306:
1305:
1269:
1263:
1262:
1222:
1216:
1215:
1190:
1184:
1183:
1147:
1141:
1140:
1114:
1108:
1107:
1105:
1104:
1090:
1084:
1083:
1073:
1055:
1037:
1013:
1007:
1006:
996:
978:
960:
936:
930:
929:
911:
905:
904:
902:
901:
886:
880:
879:
868:
862:
861:
850:
844:
843:
831:
821:
812:
811:
793:
761:
755:
754:
744:
726:
708:
684:
678:
677:
675:
673:
657:
632:Worm memory test
97:computer network
93:computer program
88:is a standalone
21:
2873:
2872:
2868:
2867:
2866:
2864:
2863:
2862:
2838:
2837:
2835:
2833:
2828:
2678:
2378:
2366:
2357:Copy protection
2347:Mobile security
2278:
2273:
2243:
2238:
2217:Countermeasures
2212:
2203:Mobile security
2151:
2142:Palm OS viruses
2107:Android malware
2095:
2009:
2005:Zombie computer
1963:
1927:
1921:
1861:
1856:
1837:
1833:
1823:
1821:
1814:
1813:
1804:
1791:
1790:
1786:
1771:
1755:. p. 704.
1749:
1745:
1730:
1729:
1725:
1716:
1715:
1711:
1674:
1670:
1639:
1635:
1625:
1623:
1615:
1614:
1610:
1587:
1583:
1574:
1572:
1567:
1566:
1562:
1549:
1548:
1544:
1535:
1533:
1524:
1523:
1519:
1510:
1508:
1503:
1502:
1498:
1491:
1467:
1463:
1424:
1420:
1381:
1377:
1364:
1363:
1359:
1344:
1340:
1330:
1328:
1313:
1309:
1270:
1266:
1223:
1219:
1213:
1191:
1187:
1148:
1144:
1129:
1115:
1111:
1102:
1100:
1092:
1091:
1087:
1028:(5): e0127478.
1014:
1010:
951:(5): e0127478.
937:
933:
926:
912:
908:
899:
897:
888:
887:
883:
870:
869:
865:
854:"The Submarine"
852:
851:
847:
840:
822:
815:
762:
758:
699:(5): e0127478.
685:
681:
671:
669:
660:Barwise, Mike.
658:
654:
650:
562:
469:
374:zero-day attack
366:
364:Countermeasures
353:Windows systems
315:exfiltrate data
299:
243:vulnerabilities
230:Exploit attacks
214:
149:'s 1975 novel,
129:
46:
39:
28:
23:
22:
15:
12:
11:
5:
2871:
2861:
2860:
2855:
2850:
2848:Computer worms
2830:
2829:
2827:
2826:
2824:Site isolation
2821:
2816:
2815:
2814:
2808:
2798:
2797:
2796:
2791:
2780:
2775:
2770:
2765:
2760:
2755:
2754:
2753:
2748:
2738:
2737:
2736:
2731:
2730:
2729:
2722:Authentication
2714:
2713:
2712:
2711:
2710:
2700:
2697:
2686:
2684:
2680:
2679:
2677:
2676:
2671:
2666:
2661:
2656:
2651:
2646:
2641:
2636:
2631:
2626:
2621:
2616:
2611:
2606:
2601:
2596:
2591:
2586:
2581:
2576:
2575:
2574:
2564:
2559:
2554:
2549:
2544:
2539:
2534:
2529:
2524:
2522:Email spoofing
2519:
2514:
2509:
2504:
2499:
2494:
2489:
2484:
2479:
2474:
2469:
2464:
2462:DOM clobbering
2459:
2454:
2449:
2444:
2442:Code injection
2439:
2434:
2433:
2432:
2427:
2422:
2417:
2409:
2404:
2399:
2394:
2388:
2386:
2380:
2379:
2369:
2367:
2365:
2364:
2359:
2354:
2349:
2344:
2339:
2334:
2329:
2324:
2322:Cyberterrorism
2319:
2314:
2313:
2312:
2310:Computer fraud
2307:
2297:
2292:
2286:
2284:
2280:
2279:
2272:
2271:
2264:
2257:
2249:
2240:
2239:
2237:
2236:
2231:
2226:
2220:
2218:
2214:
2213:
2211:
2210:
2205:
2200:
2195:
2190:
2185:
2180:
2175:
2170:
2165:
2163:Anti-keylogger
2159:
2157:
2153:
2152:
2150:
2149:
2144:
2139:
2137:Mobile malware
2134:
2129:
2124:
2119:
2114:
2109:
2103:
2101:
2097:
2096:
2094:
2093:
2088:
2083:
2078:
2073:
2068:
2063:
2058:
2053:
2048:
2043:
2038:
2033:
2028:
2023:
2017:
2015:
2011:
2010:
2008:
2007:
2002:
1997:
1992:
1987:
1982:
1977:
1971:
1969:
1965:
1964:
1962:
1961:
1956:
1951:
1946:
1944:Computer virus
1941:
1935:
1933:
1929:
1928:
1920:
1919:
1912:
1905:
1897:
1891:
1890:
1887:Worm Evolution
1884:
1878:
1868:
1860:
1859:External links
1857:
1855:
1854:
1831:
1802:
1799:on 2001-09-14.
1784:
1769:
1743:
1732:"Root My Roku"
1723:
1709:
1688:(3): 172–180.
1668:
1633:
1608:
1581:
1560:
1542:
1517:
1496:
1489:
1461:
1434:(3): 365–404.
1418:
1375:
1357:
1338:
1307:
1264:
1237:(3): 209–220.
1217:
1211:
1185:
1142:
1127:
1109:
1085:
1008:
931:
924:
906:
881:
863:
845:
838:
813:
756:
679:
651:
649:
646:
645:
644:
639:
634:
629:
624:
619:
613:
608:
603:
598:
593:
591:Computer virus
588:
583:
578:
573:
568:
561:
558:
468:
465:
460:
459:
454:
444:
431:
429:Packet-filters
426:
365:
362:
336:or performing
298:
295:
287:shared folders
281:Contagiousness
213:
210:
128:
125:
79:Conficker worm
43:Computer virus
26:
9:
6:
4:
3:
2:
2870:
2859:
2856:
2854:
2851:
2849:
2846:
2845:
2843:
2836:
2825:
2822:
2820:
2817:
2812:
2809:
2807:
2804:
2803:
2802:
2799:
2795:
2792:
2789:
2786:
2785:
2784:
2781:
2779:
2776:
2774:
2771:
2769:
2766:
2764:
2761:
2759:
2756:
2752:
2749:
2747:
2744:
2743:
2742:
2739:
2735:
2734:Authorization
2732:
2728:
2725:
2724:
2723:
2720:
2719:
2718:
2715:
2709:
2706:
2705:
2704:
2701:
2698:
2696:
2695:Secure coding
2693:
2692:
2691:
2688:
2687:
2685:
2681:
2675:
2672:
2670:
2667:
2665:
2664:SQL injection
2662:
2660:
2657:
2655:
2652:
2650:
2647:
2645:
2644:Vulnerability
2642:
2640:
2637:
2635:
2632:
2630:
2629:Trojan horses
2627:
2625:
2624:Software bugs
2622:
2620:
2617:
2615:
2612:
2610:
2607:
2605:
2602:
2600:
2597:
2595:
2592:
2590:
2587:
2585:
2582:
2580:
2577:
2573:
2570:
2569:
2568:
2565:
2563:
2560:
2558:
2555:
2553:
2550:
2548:
2545:
2543:
2540:
2538:
2535:
2533:
2530:
2528:
2525:
2523:
2520:
2518:
2515:
2513:
2512:Eavesdropping
2510:
2508:
2505:
2503:
2502:Data scraping
2500:
2498:
2495:
2493:
2490:
2488:
2485:
2483:
2480:
2478:
2475:
2473:
2472:Cryptojacking
2470:
2468:
2465:
2463:
2460:
2458:
2455:
2453:
2450:
2448:
2445:
2443:
2440:
2438:
2435:
2431:
2428:
2426:
2423:
2421:
2418:
2416:
2413:
2412:
2410:
2408:
2405:
2403:
2400:
2398:
2395:
2393:
2390:
2389:
2387:
2385:
2381:
2373:
2363:
2360:
2358:
2355:
2353:
2350:
2348:
2345:
2343:
2340:
2338:
2335:
2333:
2330:
2328:
2325:
2323:
2320:
2318:
2315:
2311:
2308:
2306:
2303:
2302:
2301:
2298:
2296:
2293:
2291:
2288:
2287:
2285:
2281:
2277:
2270:
2265:
2263:
2258:
2256:
2251:
2250:
2247:
2235:
2232:
2230:
2227:
2225:
2222:
2221:
2219:
2215:
2209:
2206:
2204:
2201:
2199:
2196:
2194:
2191:
2189:
2186:
2184:
2181:
2179:
2176:
2174:
2171:
2169:
2166:
2164:
2161:
2160:
2158:
2154:
2148:
2145:
2143:
2140:
2138:
2135:
2133:
2130:
2128:
2127:MacOS malware
2125:
2123:
2122:Linux malware
2120:
2118:
2115:
2113:
2110:
2108:
2105:
2104:
2102:
2098:
2092:
2089:
2087:
2084:
2082:
2079:
2077:
2074:
2072:
2069:
2067:
2064:
2062:
2059:
2057:
2054:
2052:
2049:
2047:
2044:
2042:
2041:Form grabbing
2039:
2037:
2034:
2032:
2029:
2027:
2024:
2022:
2019:
2018:
2016:
2012:
2006:
2003:
2001:
1998:
1996:
1993:
1991:
1988:
1986:
1983:
1981:
1978:
1976:
1973:
1972:
1970:
1966:
1960:
1957:
1955:
1952:
1950:
1949:Computer worm
1947:
1945:
1942:
1940:
1937:
1936:
1934:
1930:
1925:
1918:
1913:
1911:
1906:
1904:
1899:
1898:
1895:
1888:
1885:
1882:
1879:
1876:
1872:
1869:
1866:
1865:Malware Guide
1863:
1862:
1850:
1846:
1842:
1835:
1819:
1818:
1811:
1809:
1807:
1798:
1794:
1788:
1780:
1776:
1772:
1766:
1762:
1758:
1754:
1747:
1739:
1738:
1733:
1727:
1719:
1713:
1705:
1701:
1696:
1691:
1687:
1683:
1679:
1672:
1664:
1660:
1656:
1652:
1648:
1644:
1637:
1622:
1618:
1612:
1604:
1600:
1596:
1592:
1585:
1570:
1564:
1556:
1552:
1546:
1532:on 2018-01-16
1531:
1527:
1521:
1506:
1500:
1492:
1486:
1481:
1476:
1472:
1465:
1457:
1453:
1449:
1445:
1441:
1437:
1433:
1429:
1422:
1414:
1410:
1406:
1402:
1398:
1394:
1390:
1386:
1379:
1371:
1367:
1361:
1353:
1349:
1342:
1326:
1322:
1318:
1311:
1303:
1299:
1295:
1291:
1287:
1283:
1279:
1275:
1268:
1260:
1256:
1252:
1248:
1244:
1240:
1236:
1232:
1228:
1221:
1214:
1208:
1204:
1200:
1196:
1189:
1181:
1177:
1173:
1169:
1165:
1161:
1157:
1153:
1146:
1138:
1134:
1130:
1124:
1120:
1113:
1099:
1095:
1089:
1081:
1077:
1072:
1067:
1063:
1059:
1054:
1049:
1045:
1041:
1036:
1031:
1027:
1023:
1019:
1012:
1004:
1000:
995:
990:
986:
982:
977:
972:
968:
964:
959:
954:
950:
946:
942:
935:
927:
921:
917:
910:
896:on 2011-07-26
895:
891:
885:
877:
873:
867:
859:
855:
849:
841:
835:
830:
829:
820:
818:
809:
805:
801:
797:
792:
787:
783:
779:
775:
771:
767:
760:
752:
748:
743:
738:
734:
730:
725:
720:
716:
712:
707:
702:
698:
694:
690:
683:
668:on 2015-03-24
667:
663:
656:
652:
643:
640:
638:
635:
633:
630:
628:
625:
623:
620:
617:
614:
612:
609:
607:
604:
602:
599:
597:
594:
592:
589:
587:
584:
582:
579:
577:
574:
572:
569:
567:
564:
563:
557:
554:
551:
549:
545:
541:
537:
533:
529:
525:
520:
518:
514:
509:
507:
503:
498:
494:
490:
486:
482:
478:
474:
464:
458:
455:
452:
448:
445:
443:
439:
435:
432:
430:
427:
425:
421:
417:
414:
413:
412:
409:
407:
402:
400:
396:
392:
388:
386:
382:
377:
376:is possible.
375:
371:
370:Patch Tuesday
361:
358:
354:
350:
346:
341:
339:
335:
331:
327:
323:
318:
316:
312:
308:
304:
294:
292:
288:
283:
282:
278:
276:
272:
271:Trojan horses
268:
264:
260:
256:
251:
250:
246:
244:
241:
237:
232:
231:
227:
225:
219:
218:
209:
206:
202:
198:
196:
192:
188:
184:
180:
175:
173:
169:
165:
164:Ray Tomlinson
161:
156:
154:
153:
148:
141:
137:
133:
124:
122:
118:
113:
111:
107:
103:
98:
94:
91:
87:
86:computer worm
80:
75:
68:
65:
62:
58:
54:
50:
44:
37:
33:
19:
18:Computer Worm
2834:
2768:Data masking
2658:
2327:Cyberwarfare
2000:Trojan horse
1980:Clickjacking
1948:
1874:
1848:
1844:
1834:
1822:. Retrieved
1816:
1797:the original
1787:
1752:
1746:
1735:
1726:
1720:. Microsoft.
1712:
1685:
1681:
1671:
1646:
1642:
1636:
1624:. Retrieved
1620:
1611:
1597:(2): 71–86.
1594:
1590:
1584:
1573:. Retrieved
1563:
1554:
1545:
1534:. Retrieved
1530:the original
1520:
1509:. Retrieved
1499:
1470:
1464:
1431:
1427:
1421:
1391:(2): 81–96.
1388:
1384:
1378:
1369:
1360:
1351:
1341:
1329:. Retrieved
1325:the original
1320:
1310:
1280:(6): 19–22.
1277:
1273:
1267:
1234:
1230:
1220:
1194:
1188:
1155:
1151:
1145:
1118:
1112:
1101:. Retrieved
1097:
1088:
1025:
1021:
1011:
948:
944:
934:
915:
909:
898:. Retrieved
894:the original
884:
875:
866:
857:
848:
827:
773:
769:
759:
696:
692:
682:
670:. Retrieved
666:the original
655:
555:
552:
540:Blaster worm
521:
510:
476:
473:helpful worm
472:
470:
461:
410:
403:
395:anti-spyware
389:
378:
367:
357:SIMATICWinCC
355:and Siemens
342:
319:
300:
284:
280:
279:
269:programs or
257:pages using
252:
248:
247:
233:
229:
228:
224:host program
220:
217:Independence
216:
215:
199:
176:
157:
150:
147:John Brunner
144:
114:
85:
83:
57:Blaster worm
2708:Misuse case
2542:Infostealer
2517:Email fraud
2482:Data breach
2317:Cybergeddon
2132:Macro virus
2117:iOS malware
2091:Web threats
2051:Infostealer
1968:Concealment
672:9 September
434:TCP Wrapper
313:attack, or
273:, such as "
245:to attack.
187:Morris worm
136:Morris worm
117:Morris worm
2842:Categories
2773:Encryption
2649:Web shells
2589:Ransomware
2537:Hacktivism
2300:Cybercrime
2156:Protection
2071:Ransomware
2036:Fleeceware
1575:2015-04-04
1536:2018-12-25
1511:2012-06-10
1505:"USN list"
1231:Simulation
1103:2021-10-08
900:2014-09-17
648:References
601:Email spam
493:Xerox Alto
485:John Shoch
481:Xerox PARC
391:Anti-virus
311:ransomware
307:ExploreZip
249:Complexity
108:, whereas
77:Spread of
67:Bill Gates
2604:Shellcode
2599:Scareware
2447:Crimeware
2407:Backdoors
2081:Scareware
2031:Crimeware
1456:154019562
1448:0963-6412
1413:154754335
1405:0039-6338
1294:0018-9162
1259:243976629
1251:0037-5497
1172:1045-9219
1137:897634290
1062:1932-6203
1035:1406.6046
985:1932-6203
958:1406.6046
800:1364-503X
733:1932-6203
706:1406.6046
544:Microsoft
513:OSI model
477:anti-worm
457:Nullroute
340:attacks.
201:Conficker
106:bandwidth
61:Microsoft
2778:Firewall
2683:Defenses
2609:Spamming
2594:Rootkits
2567:Phishing
2527:Exploits
2229:Honeypot
2188:Firewall
1975:Backdoor
1845:Leonardo
1621:Newswise
1507:. Ubuntu
1385:Survival
1370:BBC News
1302:15572850
1274:Computer
1080:25978309
1022:PLOS ONE
1003:25978309
945:PLOS ONE
808:22711861
751:25978309
693:PLOS ONE
637:XSS worm
571:BlueKeep
560:See also
524:Code Red
489:Ethernet
453:software
424:switches
406:firewall
399:firewall
385:phishing
381:ILOVEYOU
322:backdoor
275:Code Red
267:backdoor
259:VBScript
240:exploits
238:" virus
212:Features
53:Hex dump
2619:Spyware
2562:Payload
2557:Malware
2497:Viruses
2477:Botnets
2384:Threats
2086:Spyware
1995:Rootkit
1924:Malware
1779:3260588
1704:1639205
1663:1097834
1626:July 5,
1331:May 18,
1180:2242419
1071:4433115
1040:Bibcode
994:4433115
963:Bibcode
876:CERT/CC
778:Bibcode
742:4433115
711:Bibcode
548:Windows
536:Welchia
534:worms.
528:Blaster
506:Roku OS
502:malware
442:daemons
420:routers
345:Stuxnet
330:botnets
303:payload
291:e-mails
263:ActiveX
172:Creeper
168:ARPANET
127:History
110:viruses
90:malware
55:of the
2813:(SIEM)
2790:(HIDS)
2674:Zombie
2411:Bombs
2392:Adware
2061:Malbot
2026:Botnet
2021:Adware
1926:topics
1824:9 June
1777:
1767:
1737:GitHub
1702:
1661:
1487:
1454:
1446:
1411:
1403:
1300:
1292:
1257:
1249:
1209:
1178:
1170:
1135:
1125:
1078:
1068:
1060:
1001:
991:
983:
922:
836:
806:
798:
749:
739:
731:
576:Botnet
530:, and
326:zombie
160:Reaper
121:Mydoom
2659:Worms
2654:Wiper
2572:Voice
2420:Logic
1775:S2CID
1700:S2CID
1659:S2CID
1452:S2CID
1409:S2CID
1352:Wired
1298:S2CID
1255:S2CID
1176:S2CID
1030:arXiv
953:arXiv
701:arXiv
532:Santy
497:Nachi
351:) in
236:Nimda
2425:Time
2415:Fork
1826:2014
1765:ISBN
1628:2011
1485:ISBN
1444:ISSN
1401:ISSN
1333:2007
1290:ISSN
1247:ISSN
1207:ISBN
1168:ISSN
1133:OCLC
1123:ISBN
1076:PMID
1058:ISSN
999:PMID
981:ISSN
920:ISBN
834:ISBN
804:PMID
796:ISSN
747:PMID
729:ISSN
674:2010
422:and
416:ACLs
393:and
334:spam
297:Harm
255:HTML
181:, a
119:and
2430:Zip
1757:doi
1690:doi
1651:doi
1599:doi
1475:doi
1436:doi
1393:doi
1282:doi
1239:doi
1199:doi
1160:doi
1066:PMC
1048:doi
989:PMC
971:doi
786:doi
774:370
737:PMC
719:doi
475:or
451:EDR
447:EPP
438:ACL
418:in
338:DoS
277:".
64:CEO
2844::
1849:42
1847:.
1843:.
1805:^
1773:.
1763:.
1734:.
1698:.
1686:25
1684:.
1680:.
1657:.
1647:52
1645:.
1619:.
1593:.
1553:.
1483:.
1450:.
1442:.
1432:22
1430:.
1407:.
1399:.
1389:55
1387:.
1368:.
1350:.
1319:.
1296:.
1288:.
1278:42
1276:.
1253:.
1245:.
1235:98
1233:.
1229:.
1205:,
1174:.
1166:.
1156:21
1154:.
1131:.
1096:.
1074:.
1064:.
1056:.
1046:.
1038:.
1026:10
1024:.
1020:.
997:.
987:.
979:.
969:.
961:.
949:10
947:.
943:.
874:.
856:.
816:^
802:.
794:.
784:.
772:.
768:.
745:.
735:.
727:.
717:.
709:.
697:10
695:.
691:.
526:,
471:A
289:,
261:,
197:.
84:A
2268:e
2261:t
2254:v
1916:e
1909:t
1902:v
1828:.
1781:.
1759::
1740:.
1706:.
1692::
1665:.
1653::
1630:.
1605:.
1601::
1595:5
1578:.
1557:.
1539:.
1514:.
1493:.
1477::
1458:.
1438::
1415:.
1395::
1354:.
1335:.
1304:.
1284::
1261:.
1241::
1201::
1182:.
1162::
1139:.
1106:.
1082:.
1050::
1042::
1032::
1005:.
973::
965::
955::
928:.
903:.
878:.
860:.
842:.
810:.
788::
780::
753:.
721::
713::
703::
676:.
449:/
436:/
45:.
38:.
20:)
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.