816:
48:
4757:
43:
to create a chain of blocks such that each block depends on the proper encryption of the previous block. This interdependence ensures that a change to any of the plaintext bits will cause the final encrypted block to change in a way that cannot be predicted or counteracted without knowing the key to
2423:
However, when performing encryption and decryption, we are required to send the initialization vector in plain text - typically as the block immediately preceding the first block of cipher text - such that the first block of plain text can be decrypted and recovered successfully. If computing a MAC,
806:
One solution is to include the length of the message in the first block; in fact CBC-MAC has been proven secure as long as no two messages that are prefixes of each other are ever used and prepending the length is a special case of this. This can be problematic if the message length may not be known
789:
This problem cannot be solved by adding a message-size block to the end. There are three main ways of modifying CBC-MAC so that it is secure for variable length messages: 1) Input-length key separation; 2) Length-prepending; 3) Encrypt last block. In such a case, it may also be recommended to use a
2868:
Sometimes IV is used as a counter to prevent message replay attacks. However, if the attacker can predict what IV will be used for MAC verification, he or she can replay previously observed message by modifying the first data block to compensate for the change in the IV that will be used for the
875:
As with many cryptographic schemes, naïve use of ciphers and other protocols may lead to attacks being possible, reducing the effectiveness of the cryptographic protection (or even rendering it useless). We present attacks which are possible due to using the CBC-MAC incorrectly.
2856:
If the freedom to select an initialization vector is removed and all implementations of CBC-MAC fix themselves on a particular initialization vector (often the vector of zeroes, but in theory, it could be anything provided all implementations agree), this attack cannot proceed.
2378:) and that it is not repeated for any given secret key under which the block cipher operates. This provides semantic security, by means of ensuring the same plain text is not encrypted to the same cipher text, allowing an attacker to infer a relationship exists.
1962:
1656:
627:
we will perform an exclusive OR operation with the value derived for the MAC of the first message. The presence of that tag in the new message means it will cancel, leaving no contribution to the MAC from the blocks of plain text in the first message
246:), then CBC-MAC is secure for fixed-length messages. However, by itself, it is not secure for variable-length messages. Thus, any single key must only be used for messages of a fixed and known length. This is because an attacker who knows the correct
734:
3294:
1192:
to obtain corresponding plain text. Note that all plain text produced will be different from that which Alice originally sent, because Eve has modified all but the last cipher text block. In particular, the final plain text,
3129:
The simplest countermeasure is to encrypt the IV before using it (i.e., prepending IV to the data). Alternatively MAC in CFB mode can be used, because in CFB mode the IV is encrypted before it is XORed with the data.
3094:
2427:
If we allow the initialization vector to be selected arbitrarily, it follows that the first block of plain text can potentially be modified (transmitting a different message) while producing the same message tag.
867:. Compared to the other discussed methods of extending CBC-MAC to variable-length messages, encrypt-last-block has the advantage of not needing to know the length of the message until the end of the computation.
2826:. As bits in both the plain text and initialization vector have been flipped in the same places, the modification is cancelled in this first stage, meaning the input to the block cipher is identical to that for
1476:
1183:
1741:
625:
2824:
2353:
2039:, was produced, but the tag for this message matched the tag of the original, and Bob was unaware that the contents had been modified in transit. By definition, a Message Authentication Code is
2696:
2103:. It follows that the message authentication protocol, in this usage scenario, has been broken, and Bob has been deceived into believing Alice sent him a message which she did not produce.
1101:
954:
124:
2358:
This example also shows that a CBC-MAC cannot be used as a collision-resistant one-way function: given a key it is trivial to create a different message which "hashes" to the same tag.
1330:
2581:
2930:
2492:
1035:, remains the same. We assume, for the purposes of this example and without loss of generality, that the initialization vector used for the encryption process is a vector of zeroes.
2860:
To sum up, if the attacker is able to set the IV that will be used for MAC verification, he can perform arbitrary modification of the first data block without invalidating the MAC.
1006:
3577:
888:
for CBC encryption and CBC-MAC. Although a reuse of a key for different purposes is a bad practice in general, in this particular case the mistake leads to a spectacular attack:
533:
322:
2424:
we will also need to transmit the initialization vector to the other party in plain text so that they can verify the tag on the message matches the value they have computed.
2009:
1779:
2418:
2101:
3474:
2627:
759:
558:
347:
2759:
3351:
3161:
2726:
2275:
2218:
2188:
1360:
1221:
2066:
2037:
2014:
Therefore, Eve was able to modify the cipher text in transit (without necessarily knowing what plain text it corresponds to) such that an entirely different message,
1504:
784:
430:
397:
372:
3124:
2990:
2960:
2522:
3321:
2851:
2302:
2245:
2158:
2131:
1771:
1512:
1387:
1275:
1248:
1033:
280:
2247:, we cannot "undo" the decryption process in the forward step of the computation of the message authentication code so as to produce the same tag; each modified
4737:
4567:
1481:
It follows that Bob will now compute the authentication tag using CBC-MAC over all the values of plain text which he decoded. The tag for the new message,
635:
3166:
3133:
Another solution (in case protection against message replay attacks is not required) is to always use a zero vector IV. Note that the above formula for
1038:
When Bob receives the message, he will first decrypt the message by reversing the encryption process which Alice applied, using the cipher text blocks
2384:
In the operation of a ciphertext block chaining cipher, the first block of plain text is mixed with the initialization vector using an exclusive OR (
187:
159:
4420:
40:
4340:
2995:
3728:
3757:
3574:
3385:– Hash functions can be made from block ciphers. But note, there are significant differences in function and uses for security between
4790:
2381:
When computing a message authentication code, such as by CBC-MAC, the use of an initialization vector is a possible attack vector.
3478:
220:
2853:. If no further changes are made to the plain text, the same tag will be derived despite a different message being transmitted.
134:: CBC-MAC on its own is not secure for variable-length messages (see the discussion below) and is currently used to construct a
4785:
4356:
3645:
1392:
3553:
Information technology – Security techniques – Message
Authentication Codes (MACs) – Part 1: Mechanisms using a block cipher
3353:
are the same message, by definition they will have the same tag. This is not a forgery, rather the intended use of CBC-MAC.
3550:
1106:
571:
4117:
4284:
197:
CBC-MAC is also used as a "conditioning component" (a.k.a. randomness extractor, a method to generate bitstrings with
67:
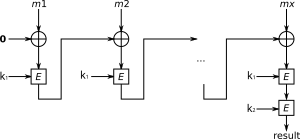
and keeps the last block. The following figure sketches the computation of the CBC-MAC of a message comprising blocks
4413:
3632:. Lecture Notes in Computer Science. Vol. 5536. Berlin, Heidelberg: Springer Berlin Heidelberg. pp. 53–70.
1667:
2307:
1041:
894:
70:
3721:
2764:
4616:
4325:
3810:
3762:
2635:
2527:
2872:
2434:
2374:
to the first stage of the encryption process. It is typically required that this vector be chosen randomly (a
4112:
4406:
4330:
3382:
1280:
135:
3592:
959:
4732:
4687:
4500:
4099:
3741:
3737:
3390:
3386:
32:
2494:. In particular, when computing the message tag for CBC-MAC, suppose we choose an initialization vector
1957:{\displaystyle t'=E_{K}(C_{n-1}'\oplus E_{K}^{-1}(C_{n})\oplus C_{n-1}')=E_{K}(E_{K}^{-1}(C_{n}))=C_{n}}
4611:
3714:
3365:– A block-cipher–based MAC algorithm which is secure for messages of different lengths (recommended by
4727:
3995:
1008:
cipher-text blocks and adjust any of the bits therein as she chooses, provided that the final block,
3800:
3575:
http://spark-university.s3.amazonaws.com/stanford-crypto/slides/05.3-integrity-cbc-mac-and-nmac.pptx
2387:
4717:
4707:
4562:
4335:
4171:
3870:
3865:
2586:
1362:
is produced when chaining the previous cipher text block into the exclusive-OR after decryption of
243:
224:
175:
4712:
4702:
4505:
4465:
4458:
4448:
4443:
4258:
4078:
3448:
Using
Advanced Encryption Standard (AES) CCM Mode with IPsec Encapsulating Security Payload (ESP)
1970:
4453:
4366:
3752:
2728:, flip the corresponding bit in the initialization vector to produce the initialization vector
2075:
1651:{\displaystyle t'=E_{K}(P_{n}'\oplus E_{K}(P_{n-1}'\oplus E_{K}(\dots \oplus E_{K}(P_{1}'))))}
4760:
4606:
4552:
4381:
4031:
3985:
3875:
3833:
3818:
2731:
2371:
2367:
435:
285:
64:
3326:
3136:
3099:
2965:
2935:
2701:
2497:
2250:
2193:
2163:
1335:
1196:
4722:
4646:
4051:
3955:
3905:
3880:
3299:
2829:
2280:
2223:
2136:
2109:
1749:
1365:
1253:
1226:
1011:
253:
179:
3565:
C. Rackoff and S. Gorbunov. On the
Security of Block Chaining Message Authentication Code.
8:
4485:
4376:
4253:
4202:
4141:
4041:
3960:
3920:
3900:
3376:
2375:
2160:, respectively, this attack is foiled. The decryption of the modified cipher-text blocks
815:
739:
538:
327:
163:
3500:
2046:
2017:
1484:
764:
410:
377:
352:
4591:
4575:
4522:
4310:
4294:
4243:
3828:
3607:
Introduction to Modern
Cryptography, Second Edition by Jonathan Katz and Yehuda Lindell
247:
4651:
4641:
4512:
4187:
3687:
3651:
3641:
3623:"How to Extract and Expand Randomness: A Summary and Explanation of Existing Results"
2106:
If, instead, we use different keys for the encryption and authentication stages, say
729:{\displaystyle E_{K_{\text{MAC}}}(m_{1}'\oplus t\oplus t)=E_{K_{\text{MAC}}}(m_{1}')}
3289:{\displaystyle M_{1}'=(P_{1}\oplus 0\oplus 0)|P_{2}|\dots =P_{1}|P_{2}|\dots =M_{1}}
4586:
4274:
4228:
3990:
3679:
3633:
3596:
3457:
3441:
2761:. It follows that to compute the MAC for this message, we begin the computation by
230:
The CBC-MAC algorithm is also included into ANSI X9.9, ANSI X9.19, ISO 8731-1, and
183:
4289:
4238:
4233:
4021:
3736:
3581:
2420:). The result of this operation is the input to the block cipher for encryption.
202:
3637:
3461:
3445:
3414:
1103:. The tampered message, delivered to Bob in replacement of Alice's original, is
4661:
4581:
4542:
4490:
4475:
4279:
4007:
3379:– Other methods to turn block ciphers into message authentication codes (MACs).
231:
4779:
4742:
4697:
4656:
4636:
4532:
4495:
4470:
4371:
4248:
3691:
3655:
3950:
4692:
4537:
4527:
4517:
4480:
4429:
213:
198:
155:
36:
20:
4671:
4361:
4207:
4136:
4132:
3372:
47:
3678:(1). Institute of Electrical and Electronics Engineers (IEEE): 188–199.
4631:
4601:
4596:
4557:
3664:
3622:
879:
3683:
3425:
3423:
3415:
The security of the cipher block chaining message authentication code.
2361:
4621:
4036:
3915:
3089:{\displaystyle M_{1}'=(P_{1}\oplus IV_{1}\oplus IV_{2})|P_{2}|\dots }
3823:
1188:
Bob first decrypts the message received using the shared secret key
4666:
4626:
4315:
4212:
4197:
4192:
4182:
4146:
4066:
3980:
3860:
3420:
2043:
if we can find a different message (a sequence of plain-text pairs
237:
151:
139:
956:. During the transmission process, Eve can tamper with any of the
190:
Rev2). It is available for TLS 1.3, but not enabled by default in
4151:
3885:
3504:
568:, but when this value is chained forwards to the stage computing
191:
2869:
verification. For example, if the attacker has observed message
39:. The message is encrypted with some block cipher algorithm in
4547:
4320:
4061:
4056:
4026:
4016:
3975:
3970:
3965:
3945:
3940:
3910:
3895:
3855:
3518:
4046:
3935:
3890:
3838:
3795:
3790:
3784:
171:
4161:
4156:
4127:
4122:
4086:
3366:
3362:
795:
791:
167:
3665:"On the security of iterated message authentication codes"
2863:
3930:
3925:
3778:
3621:
Cliff, Yvonne; Boyd, Colin; Gonzalez Nieto, Juan (2009).
242:
If the block cipher used is secure (meaning that it is a
3464:
AES-CCM Cipher Suites for
Transport Layer Security (TLS)
3620:
3429:
2068:) which produces the same tag as the previous message,
1471:{\displaystyle P_{n}'=C_{n-1}'\oplus E_{K}^{-1}(C_{n})}
870:
4568:
Cryptographically secure pseudorandom number generator
798:
to protect the integrity of variable-length messages.
208:
3329:
3302:
3169:
3139:
3102:
2998:
2968:
2938:
2875:
2832:
2767:
2734:
2704:
2638:
2589:
2530:
2500:
2437:
2390:
2310:
2283:
2253:
2226:
2220:. However, due to the MAC's usage of a different key
2196:
2166:
2139:
2112:
2078:
2049:
2020:
1973:
1782:
1752:
1670:
1515:
1487:
1395:
1368:
1338:
1283:
1256:
1229:
1199:
1109:
1044:
1014:
962:
897:
891:
Suppose Alice has sent to Bob the cipher text blocks
767:
742:
638:
574:
541:
438:
413:
380:
355:
330:
288:
256:
73:
3698:
880:
Using the same key for encryption and authentication
823:
Encrypt-last-block CBC-MAC (ECBC-MAC) is defined as
3662:
3524:
2362:
Allowing the initialization vector to vary in value
374:. This is simply done by XORing the first block of
3345:
3315:
3288:
3155:
3118:
3088:
2984:
2954:
2924:
2845:
2818:
2753:
2720:
2690:
2621:
2575:
2516:
2486:
2412:
2347:
2296:
2269:
2239:
2212:
2182:
2152:
2125:
2095:
2060:
2031:
2003:
1956:
1765:
1735:
1650:
1498:
1470:
1381:
1354:
1324:
1269:
1242:
1215:
1178:{\displaystyle C'=C_{1}'\|\dots \|C_{n-1}'\|C_{n}}
1177:
1095:
1027:
1000:
948:
778:
753:
728:
620:{\displaystyle E_{K_{\text{MAC}}}(m_{1}'\oplus t)}
619:
552:
527:
424:
391:
366:
341:
316:
274:
118:
25:cipher block chaining message authentication code
4777:
2370:(or another) mode, it is common to introduce an
238:Security with fixed and variable-length messages
1736:{\displaystyle t'=E_{K}(P_{n}'\oplus C_{n-1}')}
2348:{\displaystyle \mathrm {MAC} _{i}\not =C_{i}'}
1096:{\displaystyle C=C_{1}\|C_{2}\|\cdots \|C_{n}}
4414:
3722:
2524:such that computation of the MAC begins with
2366:When encrypting data using a block cipher in
949:{\displaystyle C=C_{1}\|C_{2}\|\dots \|C_{n}}
150:The CBC-MAC construct is used as part of the
1162:
1140:
1134:
1080:
1074:
1061:
933:
927:
914:
884:One common mistake is to reuse the same key
506:
500:
484:
453:
119:{\displaystyle m_{1}\|m_{2}\|\cdots \|m_{x}}
103:
97:
84:
2819:{\displaystyle E_{K}(P_{1}'\oplus IV_{1}')}
223:that specified the CBC-MAC algorithm using
4421:
4407:
3729:
3715:
819:Computation of CBC-MAC Encrypt-last-block.
790:different mode of operation, for example,
3630:Applied Cryptography and Network Security
2691:{\displaystyle M_{2}=P_{1}'|P_{2}|\dots }
2576:{\displaystyle E_{K}(IV_{1}\oplus P_{1})}
560:, it follows that we compute the MAC for
535:. When computing the MAC for the message
3663:Preneel, B.; van Oorschot, P.C. (1999).
2925:{\displaystyle M_{1}=P_{1}|P_{2}|\dots }
2487:{\displaystyle M_{1}=P_{1}|P_{2}|\dots }
1661:Notice that this expression is equal to
814:
46:
3672:IEEE Transactions on Information Theory
3498:
2864:Using predictable initialization vector
4778:
3413:M. Bellare, J. Kilian and P. Rogaway.
2583:. This produces a (message, tag) pair
250:(i.e. CBC-MAC) pairs for two messages
4402:
3710:
3430:Cliff, Boyd & Gonzalez Nieto 2009
3409:
3407:
3096:that will pass MAC verification with
2304:in the CBC-MAC process to some value
1325:{\displaystyle C_{n-1}'\not =C_{n-1}}
810:
16:Message authentication code algorithm
3537:
3535:
3533:
1001:{\displaystyle C_{1},\dots ,C_{n-1}}
871:Attack methods against incorrect use
801:
55:To calculate the CBC-MAC of message
31:) is a technique for constructing a
209:Standards that define the algorithm
145:
13:
3559:
3404:
2319:
2316:
2313:
166:, the CCM encryption protocol for
14:
4802:
3530:
33:message authentication code (MAC)
4756:
4755:
4428:
3541:See Section 5 of Bellare, et al.
41:cipher block chaining (CBC) mode
4791:Block cipher modes of operation
3601:
3586:
3568:
3556:, clause 6.1.3 Padding Method 3
3525:Preneel & van Oorschot 1999
3475:"Bluetooth Low Energy Security"
2190:obtains some plain text string
4617:Information-theoretic security
4326:NIST hash function competition
3544:
3492:
3467:
3451:
3435:
3266:
3251:
3230:
3215:
3211:
3186:
3079:
3064:
3060:
3015:
2915:
2900:
2813:
2778:
2681:
2666:
2616:
2590:
2570:
2541:
2477:
2462:
2413:{\displaystyle P_{1}\oplus IV}
1938:
1935:
1922:
1901:
1885:
1860:
1847:
1804:
1730:
1692:
1645:
1642:
1639:
1636:
1620:
1601:
1566:
1537:
1465:
1452:
723:
707:
684:
656:
614:
592:
522:
481:
459:
456:
311:
289:
269:
257:
1:
3397:
2622:{\displaystyle (M_{1},T_{1})}
1250:, which Alice sent; although
1223:, differs from the original,
324:can generate a third message
4786:Message authentication codes
4331:Password Hashing Competition
3742:message authentication codes
3738:Cryptographic hash functions
3499:Caswell, Matt (2017-05-04).
3383:One-way compression function
1332:, so a different plain text
217:Computer Data Authentication
136:pseudorandom function family
7:
4733:Message authentication code
4688:Cryptographic hash function
4501:Cryptographic hash function
4285:Merkle–Damgård construction
3638:10.1007/978-3-642-01957-9_4
3501:"Using TLS1.3 With OpenSSL"
3356:
2698:. For each bit modified in
349:whose CBC-MAC will also be
10:
4807:
4612:Harvest now, decrypt later
3614:
2004:{\displaystyle t'=C_{n}=t}
138:and as a component of the
4751:
4728:Post-quantum cryptography
4680:
4436:
4398:
4349:
4303:
4267:
4221:
4170:
4098:
4075:
4004:
3848:
3809:
3771:
3748:
3706:
3702:
3417:JCSS 61(3):362–399, 2000.
2277:will now be encrypted by
2096:{\displaystyle P\not =P'}
4718:Quantum key distribution
4708:Authenticated encryption
4563:Random number generation
4079:key derivation functions
2632:Now produce the message
807:when processing begins.
244:pseudorandom permutation
221:U.S. government standard
4713:Public-key cryptography
4703:Symmetric-key algorithm
4506:Key derivation function
4466:Cryptographic primitive
4459:Authentication protocol
4449:Outline of cryptography
4444:History of cryptography
4357:Hash-based cryptography
4259:Length extension attack
2754:{\displaystyle IV_{1}'}
564:in the usual manner as
528:{\displaystyle m''=m\|}
403:and then concatenating
317:{\displaystyle (m',t')}
4454:Cryptographic protocol
4367:Message authentication
3389:(such as CBC-MAC) and
3347:
3346:{\displaystyle M_{1}'}
3317:
3290:
3157:
3156:{\displaystyle M_{1}'}
3120:
3119:{\displaystyle IV_{2}}
3090:
2986:
2985:{\displaystyle IV_{2}}
2956:
2955:{\displaystyle IV_{1}}
2926:
2847:
2820:
2755:
2722:
2721:{\displaystyle P_{1}'}
2692:
2623:
2577:
2518:
2517:{\displaystyle IV_{1}}
2488:
2414:
2349:
2298:
2271:
2270:{\displaystyle P_{i}'}
2241:
2214:
2213:{\displaystyle P_{i}'}
2184:
2183:{\displaystyle C_{i}'}
2154:
2127:
2097:
2062:
2033:
2005:
1958:
1767:
1737:
1652:
1500:
1472:
1383:
1356:
1355:{\displaystyle P_{n}'}
1326:
1271:
1244:
1217:
1216:{\displaystyle P_{n}'}
1179:
1097:
1029:
1002:
950:
820:
780:
755:
730:
621:
554:
529:
426:
393:
368:
343:
318:
276:
120:
63:in CBC mode with zero
52:
4607:End-to-end encryption
4553:Cryptojacking malware
3348:
3318:
3316:{\displaystyle M_{1}}
3291:
3158:
3121:
3091:
2987:
2957:
2927:
2848:
2846:{\displaystyle M_{1}}
2821:
2756:
2723:
2693:
2624:
2578:
2519:
2489:
2415:
2372:initialization vector
2368:cipher block chaining
2350:
2299:
2297:{\displaystyle K_{2}}
2272:
2242:
2240:{\displaystyle K_{2}}
2215:
2185:
2155:
2153:{\displaystyle K_{2}}
2128:
2126:{\displaystyle K_{1}}
2098:
2063:
2034:
2006:
1959:
1768:
1766:{\displaystyle C_{n}}
1738:
1653:
1501:
1473:
1384:
1382:{\displaystyle C_{n}}
1357:
1327:
1272:
1270:{\displaystyle C_{n}}
1245:
1243:{\displaystyle P_{n}}
1218:
1180:
1098:
1030:
1028:{\displaystyle C_{n}}
1003:
951:
818:
781:
756:
736:and thus the tag for
731:
622:
555:
530:
427:
394:
369:
344:
319:
277:
275:{\displaystyle (m,t)}
227:as the block cipher.
121:
65:initialization vector
50:
4723:Quantum cryptography
4647:Trusted timestamping
3551:ISO/IEC 9797-1:1999
3327:
3300:
3167:
3137:
3100:
2996:
2966:
2936:
2873:
2830:
2765:
2732:
2702:
2636:
2587:
2528:
2498:
2435:
2388:
2308:
2281:
2251:
2224:
2194:
2164:
2137:
2110:
2076:
2047:
2018:
1971:
1967:and it follows that
1780:
1750:
1668:
1513:
1485:
1393:
1366:
1336:
1281:
1254:
1227:
1197:
1107:
1042:
1012:
960:
895:
765:
740:
636:
572:
539:
436:
411:
378:
353:
328:
286:
254:
219:is a (now obsolete)
180:Bluetooth Low Energy
71:
51:CBC-MAC construction
4486:Cryptographic nonce
4254:Side-channel attack
3342:
3182:
3152:
3011:
2812:
2793:
2750:
2717:
2664:
2431:Consider a message
2344:
2266:
2209:
2179:
1921:
1884:
1846:
1825:
1729:
1707:
1635:
1587:
1552:
1451:
1430:
1408:
1351:
1302:
1212:
1161:
1133:
754:{\displaystyle m''}
722:
671:
607:
553:{\displaystyle m''}
521:
499:
474:
407:with this modified
342:{\displaystyle m''}
234:MAC (Algorithm 1).
130:and a block cipher
126:using a secret key
4592:Subliminal channel
4576:Pseudorandom noise
4523:Key (cryptography)
4311:CAESAR Competition
4295:HAIFA construction
4244:Brute-force attack
3593:Why I hate CBC-MAC
3580:2017-04-22 at the
3343:
3330:
3313:
3286:
3170:
3153:
3140:
3116:
3086:
2999:
2992:, he can produce
2982:
2952:
2922:
2843:
2816:
2800:
2781:
2751:
2738:
2718:
2705:
2688:
2652:
2619:
2573:
2514:
2484:
2410:
2345:
2332:
2294:
2267:
2254:
2237:
2210:
2197:
2180:
2167:
2150:
2123:
2093:
2061:{\displaystyle P'}
2058:
2032:{\displaystyle P'}
2029:
2001:
1954:
1904:
1866:
1829:
1807:
1763:
1733:
1711:
1695:
1648:
1623:
1569:
1540:
1499:{\displaystyle t'}
1496:
1468:
1434:
1412:
1396:
1379:
1352:
1339:
1322:
1284:
1267:
1240:
1213:
1200:
1175:
1143:
1121:
1093:
1025:
998:
946:
821:
811:Encrypt-last-block
779:{\displaystyle t'}
776:
751:
726:
710:
659:
617:
595:
550:
525:
509:
487:
462:
432:; i.e., by making
425:{\displaystyle m'}
422:
392:{\displaystyle m'}
389:
367:{\displaystyle t'}
364:
339:
314:
272:
248:authentication tag
116:
53:
44:the block cipher.
4773:
4772:
4769:
4768:
4652:Key-based routing
4642:Trapdoor function
4513:Digital signature
4394:
4393:
4390:
4389:
4188:ChaCha20-Poly1305
4005:Password hashing/
3684:10.1109/18.746787
3647:978-3-642-01956-2
1746:which is exactly
802:Length prepending
702:
651:
587:
4798:
4759:
4758:
4587:Insecure channel
4423:
4416:
4409:
4400:
4399:
4275:Avalanche effect
4229:Collision attack
3772:Common functions
3731:
3724:
3717:
3708:
3707:
3704:
3703:
3700:
3699:
3695:
3669:
3659:
3627:
3608:
3605:
3599:
3597:Matthew D. Green
3590:
3584:
3572:
3566:
3563:
3557:
3548:
3542:
3539:
3528:
3522:
3516:
3515:
3513:
3512:
3496:
3490:
3489:
3487:
3486:
3477:. Archived from
3471:
3465:
3455:
3449:
3439:
3433:
3427:
3418:
3411:
3352:
3350:
3349:
3344:
3338:
3322:
3320:
3319:
3314:
3312:
3311:
3295:
3293:
3292:
3287:
3285:
3284:
3269:
3264:
3263:
3254:
3249:
3248:
3233:
3228:
3227:
3218:
3198:
3197:
3178:
3162:
3160:
3159:
3154:
3148:
3125:
3123:
3122:
3117:
3115:
3114:
3095:
3093:
3092:
3087:
3082:
3077:
3076:
3067:
3059:
3058:
3043:
3042:
3027:
3026:
3007:
2991:
2989:
2988:
2983:
2981:
2980:
2961:
2959:
2958:
2953:
2951:
2950:
2931:
2929:
2928:
2923:
2918:
2913:
2912:
2903:
2898:
2897:
2885:
2884:
2852:
2850:
2849:
2844:
2842:
2841:
2825:
2823:
2822:
2817:
2808:
2789:
2777:
2776:
2760:
2758:
2757:
2752:
2746:
2727:
2725:
2724:
2719:
2713:
2697:
2695:
2694:
2689:
2684:
2679:
2678:
2669:
2660:
2648:
2647:
2628:
2626:
2625:
2620:
2615:
2614:
2602:
2601:
2582:
2580:
2579:
2574:
2569:
2568:
2556:
2555:
2540:
2539:
2523:
2521:
2520:
2515:
2513:
2512:
2493:
2491:
2490:
2485:
2480:
2475:
2474:
2465:
2460:
2459:
2447:
2446:
2419:
2417:
2416:
2411:
2400:
2399:
2354:
2352:
2351:
2346:
2340:
2328:
2327:
2322:
2303:
2301:
2300:
2295:
2293:
2292:
2276:
2274:
2273:
2268:
2262:
2246:
2244:
2243:
2238:
2236:
2235:
2219:
2217:
2216:
2211:
2205:
2189:
2187:
2186:
2181:
2175:
2159:
2157:
2156:
2151:
2149:
2148:
2132:
2130:
2129:
2124:
2122:
2121:
2102:
2100:
2099:
2094:
2092:
2071:
2067:
2065:
2064:
2059:
2057:
2038:
2036:
2035:
2030:
2028:
2010:
2008:
2007:
2002:
1994:
1993:
1981:
1963:
1961:
1960:
1955:
1953:
1952:
1934:
1933:
1920:
1912:
1900:
1899:
1880:
1859:
1858:
1845:
1837:
1821:
1803:
1802:
1790:
1772:
1770:
1769:
1764:
1762:
1761:
1742:
1740:
1739:
1734:
1725:
1703:
1691:
1690:
1678:
1657:
1655:
1654:
1649:
1631:
1619:
1618:
1600:
1599:
1583:
1565:
1564:
1548:
1536:
1535:
1523:
1505:
1503:
1502:
1497:
1495:
1477:
1475:
1474:
1469:
1464:
1463:
1450:
1442:
1426:
1404:
1388:
1386:
1385:
1380:
1378:
1377:
1361:
1359:
1358:
1353:
1347:
1331:
1329:
1328:
1323:
1321:
1320:
1298:
1276:
1274:
1273:
1268:
1266:
1265:
1249:
1247:
1246:
1241:
1239:
1238:
1222:
1220:
1219:
1214:
1208:
1191:
1184:
1182:
1181:
1176:
1174:
1173:
1157:
1129:
1117:
1102:
1100:
1099:
1094:
1092:
1091:
1073:
1072:
1060:
1059:
1034:
1032:
1031:
1026:
1024:
1023:
1007:
1005:
1004:
999:
997:
996:
972:
971:
955:
953:
952:
947:
945:
944:
926:
925:
913:
912:
887:
866:
785:
783:
782:
777:
775:
760:
758:
757:
752:
750:
735:
733:
732:
727:
718:
706:
705:
704:
703:
700:
667:
655:
654:
653:
652:
649:
631:
626:
624:
623:
618:
603:
591:
590:
589:
588:
585:
567:
563:
559:
557:
556:
551:
549:
534:
532:
531:
526:
517:
495:
470:
446:
431:
429:
428:
423:
421:
406:
402:
398:
396:
395:
390:
388:
373:
371:
370:
365:
363:
348:
346:
345:
340:
338:
323:
321:
320:
315:
310:
299:
281:
279:
278:
273:
178:1.2, as well as
146:Use in standards
133:
129:
125:
123:
122:
117:
115:
114:
96:
95:
83:
82:
62:
58:
4806:
4805:
4801:
4800:
4799:
4797:
4796:
4795:
4776:
4775:
4774:
4765:
4747:
4676:
4432:
4427:
4386:
4345:
4304:Standardization
4299:
4290:Sponge function
4263:
4239:Birthday attack
4234:Preimage attack
4217:
4173:
4166:
4094:
4077:
4076:General purpose
4071:
4006:
4000:
3849:Other functions
3844:
3811:SHA-3 finalists
3805:
3767:
3744:
3735:
3667:
3648:
3625:
3617:
3612:
3611:
3606:
3602:
3591:
3587:
3582:Wayback Machine
3573:
3569:
3564:
3560:
3549:
3545:
3540:
3531:
3523:
3519:
3510:
3508:
3497:
3493:
3484:
3482:
3473:
3472:
3468:
3456:
3452:
3440:
3436:
3428:
3421:
3412:
3405:
3400:
3359:
3334:
3328:
3325:
3324:
3307:
3303:
3301:
3298:
3297:
3280:
3276:
3265:
3259:
3255:
3250:
3244:
3240:
3229:
3223:
3219:
3214:
3193:
3189:
3174:
3168:
3165:
3164:
3144:
3138:
3135:
3134:
3110:
3106:
3101:
3098:
3097:
3078:
3072:
3068:
3063:
3054:
3050:
3038:
3034:
3022:
3018:
3003:
2997:
2994:
2993:
2976:
2972:
2967:
2964:
2963:
2946:
2942:
2937:
2934:
2933:
2914:
2908:
2904:
2899:
2893:
2889:
2880:
2876:
2874:
2871:
2870:
2866:
2837:
2833:
2831:
2828:
2827:
2804:
2785:
2772:
2768:
2766:
2763:
2762:
2742:
2733:
2730:
2729:
2709:
2703:
2700:
2699:
2680:
2674:
2670:
2665:
2656:
2643:
2639:
2637:
2634:
2633:
2610:
2606:
2597:
2593:
2588:
2585:
2584:
2564:
2560:
2551:
2547:
2535:
2531:
2529:
2526:
2525:
2508:
2504:
2499:
2496:
2495:
2476:
2470:
2466:
2461:
2455:
2451:
2442:
2438:
2436:
2433:
2432:
2395:
2391:
2389:
2386:
2385:
2364:
2336:
2323:
2312:
2311:
2309:
2306:
2305:
2288:
2284:
2282:
2279:
2278:
2258:
2252:
2249:
2248:
2231:
2227:
2225:
2222:
2221:
2201:
2195:
2192:
2191:
2171:
2165:
2162:
2161:
2144:
2140:
2138:
2135:
2134:
2117:
2113:
2111:
2108:
2107:
2085:
2077:
2074:
2073:
2069:
2050:
2048:
2045:
2044:
2021:
2019:
2016:
2015:
1989:
1985:
1974:
1972:
1969:
1968:
1948:
1944:
1929:
1925:
1913:
1908:
1895:
1891:
1870:
1854:
1850:
1838:
1833:
1811:
1798:
1794:
1783:
1781:
1778:
1777:
1757:
1753:
1751:
1748:
1747:
1715:
1699:
1686:
1682:
1671:
1669:
1666:
1665:
1627:
1614:
1610:
1595:
1591:
1573:
1560:
1556:
1544:
1531:
1527:
1516:
1514:
1511:
1510:
1506:, is given by:
1488:
1486:
1483:
1482:
1459:
1455:
1443:
1438:
1416:
1400:
1394:
1391:
1390:
1373:
1369:
1367:
1364:
1363:
1343:
1337:
1334:
1333:
1310:
1306:
1288:
1282:
1279:
1278:
1261:
1257:
1255:
1252:
1251:
1234:
1230:
1228:
1225:
1224:
1204:
1198:
1195:
1194:
1189:
1169:
1165:
1147:
1125:
1110:
1108:
1105:
1104:
1087:
1083:
1068:
1064:
1055:
1051:
1043:
1040:
1039:
1019:
1015:
1013:
1010:
1009:
986:
982:
967:
963:
961:
958:
957:
940:
936:
921:
917:
908:
904:
896:
893:
892:
885:
882:
873:
864:
860:
857:
853:
850:
846:
842:
839:
835:
832:
828:
824:
813:
804:
768:
766:
763:
762:
743:
741:
738:
737:
714:
699:
695:
694:
690:
663:
648:
644:
643:
639:
637:
634:
633:
629:
599:
584:
580:
579:
575:
573:
570:
569:
565:
561:
542:
540:
537:
536:
513:
491:
466:
439:
437:
434:
433:
414:
412:
409:
408:
404:
400:
381:
379:
376:
375:
356:
354:
351:
350:
331:
329:
326:
325:
303:
292:
287:
284:
283:
255:
252:
251:
240:
211:
203:NIST SP 800-90B
188:NIST SP 800-121
148:
131:
127:
110:
106:
91:
87:
78:
74:
72:
69:
68:
60:
59:, one encrypts
56:
17:
12:
11:
5:
4804:
4794:
4793:
4788:
4771:
4770:
4767:
4766:
4764:
4763:
4752:
4749:
4748:
4746:
4745:
4740:
4738:Random numbers
4735:
4730:
4725:
4720:
4715:
4710:
4705:
4700:
4695:
4690:
4684:
4682:
4678:
4677:
4675:
4674:
4669:
4664:
4662:Garlic routing
4659:
4654:
4649:
4644:
4639:
4634:
4629:
4624:
4619:
4614:
4609:
4604:
4599:
4594:
4589:
4584:
4582:Secure channel
4579:
4573:
4572:
4571:
4560:
4555:
4550:
4545:
4543:Key stretching
4540:
4535:
4530:
4525:
4520:
4515:
4510:
4509:
4508:
4503:
4493:
4491:Cryptovirology
4488:
4483:
4478:
4476:Cryptocurrency
4473:
4468:
4463:
4462:
4461:
4451:
4446:
4440:
4438:
4434:
4433:
4426:
4425:
4418:
4411:
4403:
4396:
4395:
4392:
4391:
4388:
4387:
4385:
4384:
4379:
4374:
4369:
4364:
4359:
4353:
4351:
4347:
4346:
4344:
4343:
4338:
4333:
4328:
4323:
4318:
4313:
4307:
4305:
4301:
4300:
4298:
4297:
4292:
4287:
4282:
4280:Hash collision
4277:
4271:
4269:
4265:
4264:
4262:
4261:
4256:
4251:
4246:
4241:
4236:
4231:
4225:
4223:
4219:
4218:
4216:
4215:
4210:
4205:
4200:
4195:
4190:
4185:
4179:
4177:
4168:
4167:
4165:
4164:
4159:
4154:
4149:
4144:
4139:
4130:
4125:
4120:
4115:
4110:
4104:
4102:
4096:
4095:
4093:
4092:
4089:
4083:
4081:
4073:
4072:
4070:
4069:
4064:
4059:
4054:
4049:
4044:
4039:
4034:
4029:
4024:
4019:
4013:
4011:
4008:key stretching
4002:
4001:
3999:
3998:
3993:
3988:
3983:
3978:
3973:
3968:
3963:
3958:
3953:
3948:
3943:
3938:
3933:
3928:
3923:
3918:
3913:
3908:
3903:
3898:
3893:
3888:
3883:
3878:
3873:
3868:
3863:
3858:
3852:
3850:
3846:
3845:
3843:
3842:
3836:
3831:
3826:
3821:
3815:
3813:
3807:
3806:
3804:
3803:
3798:
3793:
3788:
3782:
3775:
3773:
3769:
3768:
3766:
3765:
3760:
3755:
3749:
3746:
3745:
3734:
3733:
3726:
3719:
3711:
3697:
3696:
3660:
3646:
3616:
3613:
3610:
3609:
3600:
3585:
3567:
3558:
3543:
3529:
3517:
3491:
3466:
3450:
3434:
3419:
3402:
3401:
3399:
3396:
3395:
3394:
3380:
3370:
3358:
3355:
3341:
3337:
3333:
3310:
3306:
3283:
3279:
3275:
3272:
3268:
3262:
3258:
3253:
3247:
3243:
3239:
3236:
3232:
3226:
3222:
3217:
3213:
3210:
3207:
3204:
3201:
3196:
3192:
3188:
3185:
3181:
3177:
3173:
3151:
3147:
3143:
3113:
3109:
3105:
3085:
3081:
3075:
3071:
3066:
3062:
3057:
3053:
3049:
3046:
3041:
3037:
3033:
3030:
3025:
3021:
3017:
3014:
3010:
3006:
3002:
2979:
2975:
2971:
2949:
2945:
2941:
2921:
2917:
2911:
2907:
2902:
2896:
2892:
2888:
2883:
2879:
2865:
2862:
2840:
2836:
2815:
2811:
2807:
2803:
2799:
2796:
2792:
2788:
2784:
2780:
2775:
2771:
2749:
2745:
2741:
2737:
2716:
2712:
2708:
2687:
2683:
2677:
2673:
2668:
2663:
2659:
2655:
2651:
2646:
2642:
2618:
2613:
2609:
2605:
2600:
2596:
2592:
2572:
2567:
2563:
2559:
2554:
2550:
2546:
2543:
2538:
2534:
2511:
2507:
2503:
2483:
2479:
2473:
2469:
2464:
2458:
2454:
2450:
2445:
2441:
2409:
2406:
2403:
2398:
2394:
2363:
2360:
2343:
2339:
2335:
2331:
2326:
2321:
2318:
2315:
2291:
2287:
2265:
2261:
2257:
2234:
2230:
2208:
2204:
2200:
2178:
2174:
2170:
2147:
2143:
2120:
2116:
2091:
2088:
2084:
2081:
2056:
2053:
2027:
2024:
2000:
1997:
1992:
1988:
1984:
1980:
1977:
1965:
1964:
1951:
1947:
1943:
1940:
1937:
1932:
1928:
1924:
1919:
1916:
1911:
1907:
1903:
1898:
1894:
1890:
1887:
1883:
1879:
1876:
1873:
1869:
1865:
1862:
1857:
1853:
1849:
1844:
1841:
1836:
1832:
1828:
1824:
1820:
1817:
1814:
1810:
1806:
1801:
1797:
1793:
1789:
1786:
1760:
1756:
1744:
1743:
1732:
1728:
1724:
1721:
1718:
1714:
1710:
1706:
1702:
1698:
1694:
1689:
1685:
1681:
1677:
1674:
1659:
1658:
1647:
1644:
1641:
1638:
1634:
1630:
1626:
1622:
1617:
1613:
1609:
1606:
1603:
1598:
1594:
1590:
1586:
1582:
1579:
1576:
1572:
1568:
1563:
1559:
1555:
1551:
1547:
1543:
1539:
1534:
1530:
1526:
1522:
1519:
1494:
1491:
1467:
1462:
1458:
1454:
1449:
1446:
1441:
1437:
1433:
1429:
1425:
1422:
1419:
1415:
1411:
1407:
1403:
1399:
1376:
1372:
1350:
1346:
1342:
1319:
1316:
1313:
1309:
1305:
1301:
1297:
1294:
1291:
1287:
1264:
1260:
1237:
1233:
1211:
1207:
1203:
1172:
1168:
1164:
1160:
1156:
1153:
1150:
1146:
1142:
1139:
1136:
1132:
1128:
1124:
1120:
1116:
1113:
1090:
1086:
1082:
1079:
1076:
1071:
1067:
1063:
1058:
1054:
1050:
1047:
1022:
1018:
995:
992:
989:
985:
981:
978:
975:
970:
966:
943:
939:
935:
932:
929:
924:
920:
916:
911:
907:
903:
900:
881:
878:
872:
869:
862:
858:
855:
851:
848:
844:
840:
837:
833:
830:
826:
812:
809:
803:
800:
774:
771:
749:
746:
725:
721:
717:
713:
709:
698:
693:
689:
686:
683:
680:
677:
674:
670:
666:
662:
658:
647:
642:
616:
613:
610:
606:
602:
598:
594:
583:
578:
548:
545:
524:
520:
516:
512:
508:
505:
502:
498:
494:
490:
486:
483:
480:
477:
473:
469:
465:
461:
458:
455:
452:
449:
445:
442:
420:
417:
387:
384:
362:
359:
337:
334:
313:
309:
306:
302:
298:
295:
291:
271:
268:
265:
262:
259:
239:
236:
232:ISO/IEC 9797-1
210:
207:
160:NIST SP 800-97
147:
144:
113:
109:
105:
102:
99:
94:
90:
86:
81:
77:
15:
9:
6:
4:
3:
2:
4803:
4792:
4789:
4787:
4784:
4783:
4781:
4762:
4754:
4753:
4750:
4744:
4743:Steganography
4741:
4739:
4736:
4734:
4731:
4729:
4726:
4724:
4721:
4719:
4716:
4714:
4711:
4709:
4706:
4704:
4701:
4699:
4698:Stream cipher
4696:
4694:
4691:
4689:
4686:
4685:
4683:
4679:
4673:
4670:
4668:
4665:
4663:
4660:
4658:
4657:Onion routing
4655:
4653:
4650:
4648:
4645:
4643:
4640:
4638:
4637:Shared secret
4635:
4633:
4630:
4628:
4625:
4623:
4620:
4618:
4615:
4613:
4610:
4608:
4605:
4603:
4600:
4598:
4595:
4593:
4590:
4588:
4585:
4583:
4580:
4577:
4574:
4569:
4566:
4565:
4564:
4561:
4559:
4556:
4554:
4551:
4549:
4546:
4544:
4541:
4539:
4536:
4534:
4533:Key generator
4531:
4529:
4526:
4524:
4521:
4519:
4516:
4514:
4511:
4507:
4504:
4502:
4499:
4498:
4497:
4496:Hash function
4494:
4492:
4489:
4487:
4484:
4482:
4479:
4477:
4474:
4472:
4471:Cryptanalysis
4469:
4467:
4464:
4460:
4457:
4456:
4455:
4452:
4450:
4447:
4445:
4442:
4441:
4439:
4435:
4431:
4424:
4419:
4417:
4412:
4410:
4405:
4404:
4401:
4397:
4383:
4380:
4378:
4375:
4373:
4372:Proof of work
4370:
4368:
4365:
4363:
4360:
4358:
4355:
4354:
4352:
4348:
4342:
4339:
4337:
4334:
4332:
4329:
4327:
4324:
4322:
4319:
4317:
4314:
4312:
4309:
4308:
4306:
4302:
4296:
4293:
4291:
4288:
4286:
4283:
4281:
4278:
4276:
4273:
4272:
4270:
4266:
4260:
4257:
4255:
4252:
4250:
4249:Rainbow table
4247:
4245:
4242:
4240:
4237:
4235:
4232:
4230:
4227:
4226:
4224:
4220:
4214:
4211:
4209:
4206:
4204:
4201:
4199:
4196:
4194:
4191:
4189:
4186:
4184:
4181:
4180:
4178:
4175:
4172:Authenticated
4169:
4163:
4160:
4158:
4155:
4153:
4150:
4148:
4145:
4143:
4140:
4138:
4134:
4131:
4129:
4126:
4124:
4121:
4119:
4116:
4114:
4111:
4109:
4106:
4105:
4103:
4101:
4100:MAC functions
4097:
4090:
4088:
4085:
4084:
4082:
4080:
4074:
4068:
4065:
4063:
4060:
4058:
4055:
4053:
4050:
4048:
4045:
4043:
4040:
4038:
4035:
4033:
4030:
4028:
4025:
4023:
4020:
4018:
4015:
4014:
4012:
4009:
4003:
3997:
3994:
3992:
3989:
3987:
3984:
3982:
3979:
3977:
3974:
3972:
3969:
3967:
3964:
3962:
3959:
3957:
3954:
3952:
3949:
3947:
3944:
3942:
3939:
3937:
3934:
3932:
3929:
3927:
3924:
3922:
3919:
3917:
3914:
3912:
3909:
3907:
3904:
3902:
3899:
3897:
3894:
3892:
3889:
3887:
3884:
3882:
3879:
3877:
3874:
3872:
3869:
3867:
3864:
3862:
3859:
3857:
3854:
3853:
3851:
3847:
3840:
3837:
3835:
3832:
3830:
3827:
3825:
3822:
3820:
3817:
3816:
3814:
3812:
3808:
3802:
3799:
3797:
3794:
3792:
3789:
3787:(compromised)
3786:
3783:
3781:(compromised)
3780:
3777:
3776:
3774:
3770:
3764:
3763:Known attacks
3761:
3759:
3756:
3754:
3751:
3750:
3747:
3743:
3739:
3732:
3727:
3725:
3720:
3718:
3713:
3712:
3709:
3705:
3701:
3693:
3689:
3685:
3681:
3677:
3673:
3666:
3661:
3657:
3653:
3649:
3643:
3639:
3635:
3631:
3624:
3619:
3618:
3604:
3598:
3594:
3589:
3583:
3579:
3576:
3571:
3562:
3555:
3554:
3547:
3538:
3536:
3534:
3526:
3521:
3506:
3502:
3495:
3481:on 2016-04-02
3480:
3476:
3470:
3463:
3459:
3454:
3447:
3443:
3438:
3431:
3426:
3424:
3416:
3410:
3408:
3403:
3392:
3388:
3384:
3381:
3378:
3374:
3371:
3368:
3364:
3361:
3360:
3354:
3339:
3335:
3331:
3308:
3304:
3281:
3277:
3273:
3270:
3260:
3256:
3245:
3241:
3237:
3234:
3224:
3220:
3208:
3205:
3202:
3199:
3194:
3190:
3183:
3179:
3175:
3171:
3149:
3145:
3141:
3131:
3127:
3111:
3107:
3103:
3083:
3073:
3069:
3055:
3051:
3047:
3044:
3039:
3035:
3031:
3028:
3023:
3019:
3012:
3008:
3004:
3000:
2977:
2973:
2969:
2947:
2943:
2939:
2919:
2909:
2905:
2894:
2890:
2886:
2881:
2877:
2861:
2858:
2854:
2838:
2834:
2809:
2805:
2801:
2797:
2794:
2790:
2786:
2782:
2773:
2769:
2747:
2743:
2739:
2735:
2714:
2710:
2706:
2685:
2675:
2671:
2661:
2657:
2653:
2649:
2644:
2640:
2630:
2611:
2607:
2603:
2598:
2594:
2565:
2561:
2557:
2552:
2548:
2544:
2536:
2532:
2509:
2505:
2501:
2481:
2471:
2467:
2456:
2452:
2448:
2443:
2439:
2429:
2425:
2421:
2407:
2404:
2401:
2396:
2392:
2382:
2379:
2377:
2373:
2369:
2359:
2356:
2341:
2337:
2333:
2329:
2324:
2289:
2285:
2263:
2259:
2255:
2232:
2228:
2206:
2202:
2198:
2176:
2172:
2168:
2145:
2141:
2118:
2114:
2104:
2089:
2086:
2082:
2079:
2054:
2051:
2042:
2025:
2022:
2012:
1998:
1995:
1990:
1986:
1982:
1978:
1975:
1949:
1945:
1941:
1930:
1926:
1917:
1914:
1909:
1905:
1896:
1892:
1888:
1881:
1877:
1874:
1871:
1867:
1863:
1855:
1851:
1842:
1839:
1834:
1830:
1826:
1822:
1818:
1815:
1812:
1808:
1799:
1795:
1791:
1787:
1784:
1776:
1775:
1774:
1758:
1754:
1726:
1722:
1719:
1716:
1712:
1708:
1704:
1700:
1696:
1687:
1683:
1679:
1675:
1672:
1664:
1663:
1662:
1632:
1628:
1624:
1615:
1611:
1607:
1604:
1596:
1592:
1588:
1584:
1580:
1577:
1574:
1570:
1561:
1557:
1553:
1549:
1545:
1541:
1532:
1528:
1524:
1520:
1517:
1509:
1508:
1507:
1492:
1489:
1479:
1460:
1456:
1447:
1444:
1439:
1435:
1431:
1427:
1423:
1420:
1417:
1413:
1409:
1405:
1401:
1397:
1374:
1370:
1348:
1344:
1340:
1317:
1314:
1311:
1307:
1303:
1299:
1295:
1292:
1289:
1285:
1277:is the same,
1262:
1258:
1235:
1231:
1209:
1205:
1201:
1186:
1170:
1166:
1158:
1154:
1151:
1148:
1144:
1137:
1130:
1126:
1122:
1118:
1114:
1111:
1088:
1084:
1077:
1069:
1065:
1056:
1052:
1048:
1045:
1036:
1020:
1016:
993:
990:
987:
983:
979:
976:
973:
968:
964:
941:
937:
930:
922:
918:
909:
905:
901:
898:
889:
877:
868:
817:
808:
799:
797:
793:
787:
772:
769:
747:
744:
719:
715:
711:
696:
691:
687:
681:
678:
675:
672:
668:
664:
660:
645:
640:
611:
608:
604:
600:
596:
581:
576:
546:
543:
518:
514:
510:
503:
496:
492:
488:
478:
475:
471:
467:
463:
450:
447:
443:
440:
418:
415:
385:
382:
360:
357:
335:
332:
307:
304:
300:
296:
293:
266:
263:
260:
249:
245:
235:
233:
228:
226:
222:
218:
215:
206:
204:
200:
195:
193:
189:
185:
184:Bluetooth 4.0
181:
177:
173:
169:
165:
161:
157:
153:
143:
141:
137:
111:
107:
100:
92:
88:
79:
75:
66:
49:
45:
42:
38:
34:
30:
26:
22:
4693:Block cipher
4538:Key schedule
4528:Key exchange
4518:Kleptography
4481:Cryptosystem
4430:Cryptography
4107:
3675:
3671:
3629:
3603:
3588:
3570:
3561:
3552:
3546:
3527:, p. 7.
3520:
3509:. Retrieved
3494:
3483:. Retrieved
3479:the original
3469:
3453:
3437:
3432:, p. 5.
3132:
3128:
2867:
2859:
2855:
2631:
2430:
2426:
2422:
2383:
2380:
2365:
2357:
2105:
2040:
2013:
1966:
1745:
1660:
1480:
1187:
1037:
890:
883:
874:
825:CBC-MAC-ELB(
822:
805:
788:
241:
229:
216:
214:FIPS PUB 113
212:
199:full entropy
196:
156:IEEE 802.11i
154:utilized in
149:
54:
37:block cipher
28:
24:
21:cryptography
18:
4681:Mathematics
4672:Mix network
4362:Merkle tree
4350:Utilization
4336:NSA Suite B
3296:. So since
4780:Categories
4632:Ciphertext
4602:Decryption
4597:Encryption
4558:Ransomware
4174:encryption
3951:RadioGatún
3758:Comparison
3511:2018-12-29
3485:2017-04-20
3398:References
2962:and knows
854:, CBC-MAC(
4622:Plaintext
4091:KDF1/KDF2
4010:functions
3996:Whirlpool
3692:0018-9448
3656:0302-9743
3271:⋯
3235:⋯
3206:⊕
3200:⊕
3084:…
3045:⊕
3029:⊕
2920:…
2795:⊕
2686:…
2558:⊕
2482:…
2402:⊕
1915:−
1875:−
1864:⊕
1840:−
1827:⊕
1816:−
1720:−
1709:⊕
1608:⊕
1605:⋯
1589:⊕
1578:−
1554:⊕
1445:−
1432:⊕
1421:−
1315:−
1293:−
1163:‖
1152:−
1141:‖
1138:…
1135:‖
1081:‖
1078:⋯
1075:‖
1062:‖
991:−
977:…
934:‖
931:…
928:‖
915:‖
679:⊕
673:⊕
609:⊕
507:‖
504:…
501:‖
485:‖
476:⊕
454:‖
104:‖
101:⋯
98:‖
85:‖
4761:Category
4667:Kademlia
4627:Codetext
4570:(CSPRNG)
4316:CRYPTREC
4147:Poly1305
4067:yescrypt
3981:Streebog
3861:CubeHash
3841:(winner)
3578:Archived
3357:See also
3340:′
3180:′
3163:becomes
3150:′
3009:′
2810:′
2791:′
2748:′
2715:′
2662:′
2342:′
2330:≠
2264:′
2207:′
2177:′
2090:′
2083:≠
2055:′
2026:′
1979:′
1882:′
1823:′
1788:′
1727:′
1705:′
1676:′
1633:′
1585:′
1550:′
1521:′
1493:′
1428:′
1406:′
1349:′
1304:≠
1300:′
1210:′
1159:′
1131:′
1115:′
773:′
748:″
720:′
669:′
605:′
547:″
519:′
497:′
472:′
444:″
419:′
386:′
361:′
336:″
308:′
297:′
152:CCM mode
140:CCM mode
4437:General
4222:Attacks
4152:SipHash
4108:CBC-MAC
4042:LM hash
4022:Balloon
3886:HAS-160
3615:Sources
3505:OpenSSL
2072:, with
192:OpenSSL
182:(as of
35:from a
29:CBC-MAC
4548:Keygen
4382:Pepper
4321:NESSIE
4268:Design
4062:scrypt
4057:PBKDF2
4032:Catena
4027:bcrypt
4017:Argon2
3976:Snefru
3971:Shabal
3966:SWIFFT
3946:RIPEMD
3941:N-hash
3916:MASH-2
3911:MASH-1
3896:Kupyna
3856:BLAKE3
3839:Keccak
3824:Grøstl
3801:BLAKE2
3690:
3654:
3644:
3460:
3444:
3391:hashes
2041:broken
186:, see
174:, and
4578:(PRN)
4176:modes
4052:Makwa
4047:Lyra2
4037:crypt
3986:Tiger
3936:MDC-2
3891:HAVAL
3876:Fugue
3834:Skein
3819:BLAKE
3796:SHA-3
3791:SHA-2
3785:SHA-1
3668:(PDF)
3626:(PDF)
2932:with
2376:nonce
843:)) =
399:with
201:) in
172:IPsec
4377:Salt
4341:CNSA
4208:IAPM
4162:VMAC
4157:UMAC
4142:PMAC
4137:CMAC
4133:OMAC
4128:NMAC
4123:HMAC
4118:GMAC
4087:HKDF
3956:SIMD
3906:Lane
3881:GOST
3866:ECOH
3753:List
3740:and
3688:ISSN
3652:ISSN
3642:ISBN
3507:blog
3462:6655
3446:4309
3387:MACs
3377:PMAC
3375:and
3373:OMAC
3367:NIST
3363:CMAC
3323:and
2133:and
796:HMAC
792:CMAC
282:and
168:WPA2
164:CCMP
162:(as
158:and
23:, a
4213:OCB
4203:GCM
4198:EAX
4193:CWC
4183:CCM
4113:DAA
3991:VSH
3961:SM3
3931:MD6
3926:MD4
3921:MD2
3901:LSH
3871:FSB
3779:MD5
3680:doi
3634:doi
3595:by
3458:RFC
3442:RFC
829:, (
794:or
761:is
701:MAC
650:MAC
586:MAC
225:DES
194:.
176:TLS
170:),
19:In
4782::
3829:JH
3686:.
3676:45
3674:.
3670:.
3650:.
3640:.
3628:.
3532:^
3503:.
3422:^
3406:^
3369:).
3126:.
2629:.
2355:.
2011:.
1773::
1478:.
1389::
1185:.
865:))
861:,
836:,
786:.
632::
205:.
142:.
4422:e
4415:t
4408:v
4135:/
3730:e
3723:t
3716:v
3694:.
3682::
3658:.
3636::
3514:.
3488:.
3393:.
3336:1
3332:M
3309:1
3305:M
3282:1
3278:M
3274:=
3267:|
3261:2
3257:P
3252:|
3246:1
3242:P
3238:=
3231:|
3225:2
3221:P
3216:|
3212:)
3209:0
3203:0
3195:1
3191:P
3187:(
3184:=
3176:1
3172:M
3146:1
3142:M
3112:2
3108:V
3104:I
3080:|
3074:2
3070:P
3065:|
3061:)
3056:2
3052:V
3048:I
3040:1
3036:V
3032:I
3024:1
3020:P
3016:(
3013:=
3005:1
3001:M
2978:2
2974:V
2970:I
2948:1
2944:V
2940:I
2916:|
2910:2
2906:P
2901:|
2895:1
2891:P
2887:=
2882:1
2878:M
2839:1
2835:M
2814:)
2806:1
2802:V
2798:I
2787:1
2783:P
2779:(
2774:K
2770:E
2744:1
2740:V
2736:I
2711:1
2707:P
2682:|
2676:2
2672:P
2667:|
2658:1
2654:P
2650:=
2645:2
2641:M
2617:)
2612:1
2608:T
2604:,
2599:1
2595:M
2591:(
2571:)
2566:1
2562:P
2553:1
2549:V
2545:I
2542:(
2537:K
2533:E
2510:1
2506:V
2502:I
2478:|
2472:2
2468:P
2463:|
2457:1
2453:P
2449:=
2444:1
2440:M
2408:V
2405:I
2397:1
2393:P
2338:i
2334:C
2325:i
2320:C
2317:A
2314:M
2290:2
2286:K
2260:i
2256:P
2233:2
2229:K
2203:i
2199:P
2173:i
2169:C
2146:2
2142:K
2119:1
2115:K
2087:P
2080:P
2070:P
2052:P
2023:P
1999:t
1996:=
1991:n
1987:C
1983:=
1976:t
1950:n
1946:C
1942:=
1939:)
1936:)
1931:n
1927:C
1923:(
1918:1
1910:K
1906:E
1902:(
1897:K
1893:E
1889:=
1886:)
1878:1
1872:n
1868:C
1861:)
1856:n
1852:C
1848:(
1843:1
1835:K
1831:E
1819:1
1813:n
1809:C
1805:(
1800:K
1796:E
1792:=
1785:t
1759:n
1755:C
1731:)
1723:1
1717:n
1713:C
1701:n
1697:P
1693:(
1688:K
1684:E
1680:=
1673:t
1646:)
1643:)
1640:)
1637:)
1629:1
1625:P
1621:(
1616:K
1612:E
1602:(
1597:K
1593:E
1581:1
1575:n
1571:P
1567:(
1562:K
1558:E
1546:n
1542:P
1538:(
1533:K
1529:E
1525:=
1518:t
1490:t
1466:)
1461:n
1457:C
1453:(
1448:1
1440:K
1436:E
1424:1
1418:n
1414:C
1410:=
1402:n
1398:P
1375:n
1371:C
1345:n
1341:P
1318:1
1312:n
1308:C
1296:1
1290:n
1286:C
1263:n
1259:C
1236:n
1232:P
1206:n
1202:P
1190:K
1171:n
1167:C
1155:1
1149:n
1145:C
1127:1
1123:C
1119:=
1112:C
1089:n
1085:C
1070:2
1066:C
1057:1
1053:C
1049:=
1046:C
1021:n
1017:C
994:1
988:n
984:C
980:,
974:,
969:1
965:C
942:n
938:C
923:2
919:C
910:1
906:C
902:=
899:C
886:k
863:m
859:1
856:k
852:2
849:k
847:(
845:E
841:2
838:k
834:1
831:k
827:m
770:t
745:m
724:)
716:1
712:m
708:(
697:K
692:E
688:=
685:)
682:t
676:t
665:1
661:m
657:(
646:K
641:E
630:m
615:)
612:t
601:1
597:m
593:(
582:K
577:E
566:t
562:m
544:m
523:]
515:x
511:m
493:2
489:m
482:)
479:t
468:1
464:m
460:(
457:[
451:m
448:=
441:m
416:m
405:m
401:t
383:m
358:t
333:m
312:)
305:t
301:,
294:m
290:(
270:)
267:t
264:,
261:m
258:(
132:E
128:k
112:x
108:m
93:2
89:m
80:1
76:m
61:m
57:m
27:(
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.