433:
3036:
183:
29:
428:{\displaystyle {\begin{aligned}\operatorname {HMAC} (K,m)&=\operatorname {H} {\Bigl (}{\bigl (}K'\oplus opad{\bigr )}\parallel \operatorname {H} {\bigl (}\left(K'\oplus ipad\right)\parallel m{\bigr )}{\Bigr )}\\K'&={\begin{cases}\operatorname {H} \left(K\right)&{\text{if}}\ K{\text{ is larger than block size}}\\K&{\text{otherwise}}\end{cases}}\end{aligned}}}
1046:), suffers from the problem that an attacker who can find a collision in the (unkeyed) hash function has a collision in the MAC (as two messages m1 and m2 yielding the same hash will provide the same start condition to the hash function before the appended key is hashed, hence the final hash will be the same). Using MAC =
1657:
under the sole assumption that the compression function is a PRF. This recovers a proof based guarantee since no known attacks compromise the pseudorandomness of the compression function, and it also helps explain the resistance-to-attack that HMAC has shown even when implemented with hash functions
1120:
The cryptographic strength of the HMAC depends upon the size of the secret key that is used and the security of the underlying hash function used. It has been proven that the security of an HMAC construction is directly related to security properties of the hash function used. The most common attack
114:
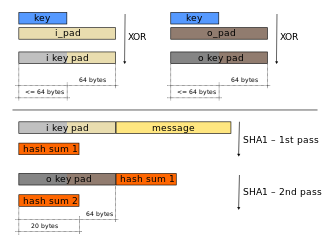
HMAC uses two passes of hash computation. Before either pass, the secret key is used to derive two keys – inner and outer. Next, the first pass of the hash algorithm produces an internal hash derived from the message and the inner key. The second pass produces the final HMAC code derived from the
1144:. This property is sometimes raised as a possible weakness of HMAC in password-hashing scenarios: it has been demonstrated that it's possible to find a long ASCII string and a random value whose hash will be also an ASCII string, and both values will produce the same HMAC output.
1231:
HMAC_MD5("key", "The quick brown fox jumps over the lazy dog") = 80070713463e7749b90c2dc24911e275 HMAC_SHA1("key", "The quick brown fox jumps over the lazy dog") = de7c9b85b8b78aa6bc8a7a36f70a90701c9db4d9 HMAC_SHA256("key", "The quick brown fox jumps over the lazy dog") =
1232:
f7bc83f430538424b13298e6aa6fb143ef4d59a14946175997479dbc2d1a3cd8 HMAC_SHA512("key", "The quick brown fox jumps over the lazy dog") = b42af09057bac1e2d41708e48a902e09b5ff7f12ab428a4fe86653c73dd248fb82f948a549f7b791a5b41915ee4d1ec3935357e4e2317250d0372afa2ebeeb3a
130:. For example, SHA-256 operates on 512-bit blocks. The size of the output of HMAC is the same as that of the underlying hash function (e.g., 256 and 512 bits in the case of SHA-256 and SHA3-512, respectively), although it can be truncated if desired.
133:
HMAC does not encrypt the message. Instead, the message (encrypted or not) must be sent alongside the HMAC hash. Parties with the secret key will hash the message again themselves, and if it is authentic, the received and computed hashes will match.
1017:
The design of the HMAC specification was motivated by the existence of attacks on more trivial mechanisms for combining a key with a hash function. For example, one might assume the same security that HMAC provides could be achieved with MAC =
1548:
Unlike SHA-1 and SHA-2, Keccak does not have the length-extension weakness, hence does not need the HMAC nested construction. Instead, MAC computation can be performed by simply prepending the message with the
1197:
presented a distinguishing attack on HMAC-MD5 without using related keys. It can distinguish an instantiation of HMAC with MD5 from an instantiation with a random function with 2 queries with probability 0.87.
1121:
against HMACs is brute force to uncover the secret key. HMACs are substantially less affected by collisions than their underlying hashing algorithms alone. In particular, Mihir
Bellare proved that HMAC is a
188:
1622:
The strongest attack known against HMAC is based on the frequency of collisions for the hash function H ("birthday attack") , and is totally impractical for minimally reasonable hash functions.
1112:
competition winner, doesn't need this nested approach and can be used to generate a MAC by simply prepending the key to the message, as it is not susceptible to length-extension attacks.
1179:
or HMAC with a random function. Differential distinguishers allow an attacker to devise a forgery attack on HMAC. Furthermore, differential and rectangle distinguishers can lead to
459:
1030:). However, this method suffers from a serious flaw: with most hash functions, it is easy to append data to the message without knowing the key and obtain another valid MAC ("
83:
by delegating the key exchange to the communicating parties, who are responsible for establishing and using a trusted channel to agree on the key prior to communication.
556:
536:; either by padding to the right with 0s up to the block size, or by hashing down to less than or equal to the block size first and then padding to the right with zeros.
1097:
from each other and so the inner and outer keys will have fewer bits in common. The security reduction of HMAC does require them to be different in at least one bit.
582:
530:
648:
617:
1125:(PRF) under the sole assumption that the compression function is a PRF. Therefore, HMAC-MD5 does not suffer from the same weaknesses that have been found in MD5.
503:
481:
3016:
2846:
1187:
with this knowledge. These attacks do not contradict the security proof of HMAC, but provide insight into HMAC based on existing cryptographic hash functions.
866:
demonstrates how HMAC may be implemented. The block size is 512 bits (64 bytes) when using one of the following hash functions: SHA-1, MD5, RIPEMD-128.
111:
of the HMAC depends upon the cryptographic strength of the underlying hash function, the size of its hash output, and the size and quality of the key.
64:
and authenticity of a message. An HMAC is a type of keyed hash function that can also be used in a key derivation scheme or a key stretching scheme.
1908:
1160:
1148:
2699:
2619:
1417:
2007:
2036:
1422:
1062:) is better, but various security papers have suggested vulnerabilities with this approach, even when two different keys are used.
150:
3064:
2635:
1136:" which leads to a confusing pseudo-collision: if the key is longer than the hash block size (e.g. 64 bytes for SHA-1), then
1085:)) because the outer application of the hash function masks the intermediate result of the internal hash. The values of
2396:
2563:
1967:
123:
2692:
1395:
1211:"attacks on HMAC-MD5 do not seem to indicate a practical vulnerability when used as a message authentication code"
2000:
1869:
2895:
2604:
2089:
2041:
149:, and they also wrote RFC 2104 in 1997. The 1996 paper also defined a nested variant called NMAC (Nested MAC).
2391:
2685:
2609:
1241:
1122:
127:
3011:
2966:
2779:
2378:
2020:
2016:
57:
53:
1949:
444:
2890:
1993:
1228:
Here are some HMAC values, assuming 8-bit ASCII for the input and hexadecimal encoding for the output:
1220:
In May 2011, RFC 6234 was published detailing the abstract theory and source code for SHA-based HMACs.
1065:
No known extension attacks have been found against the current HMAC specification which is defined as
3006:
2274:
80:
2079:
1848:
1521:
1472:
1282:
908:
block_sized_key = computeBlockSizedKey(key, hash, blockSize) o_key_pad ← block_sized_key xor
362:
2996:
2986:
2841:
2614:
2450:
2149:
2144:
1817:
1499:
1450:
162:
1093:
are not critical to the security of the algorithm, but were defined in such a way to have a large
60:
and a secret cryptographic key. As with any MAC, it may be used to simultaneously verify both the
2991:
2981:
2784:
2744:
2737:
2727:
2722:
2537:
2357:
1562:
1031:
116:
76:
541:
2732:
2645:
2031:
1654:
1494:
1445:
1277:
1184:
137:
The definition and analysis of the HMAC construction was first published in 1996 in a paper by
108:
3039:
2885:
2831:
2660:
2310:
2264:
2154:
2112:
2097:
1835:
1508:
1459:
1377:
567:
3001:
2925:
2330:
2234:
2184:
2159:
1891:
1694:
1605:
1352:
1163:
showed how to distinguish HMAC with reduced versions of MD5 and SHA-1 or full versions of
624:
593:
8:
2764:
2655:
2532:
2481:
2420:
2320:
2239:
2199:
2179:
115:
inner hash result and the outer key. Thus the algorithm provides better immunity against
1201:
In 2011 an informational RFC 6151 was published to summarize security considerations in
510:
99:, may be used in the calculation of an HMAC; the resulting MAC algorithm is termed HMAC-
2870:
2854:
2801:
2589:
2573:
2522:
2107:
488:
466:
1972:
1676:
Updated
Security Considerations for the MD5 Message-Digest and the HMAC-MD5 Algorithms
1575:
although it doesn't affect applications such as HMAC where collisions aren't important
2930:
2920:
2791:
2466:
1902:
1883:
1490:
1441:
72:
1303:
3069:
2865:
2553:
2507:
2269:
1925:
1917:
1873:
1684:
1595:
1342:
1094:
1205:
and HMAC-MD5. For HMAC-MD5 the RFC summarizes that – although the security of the
2568:
2517:
2512:
2300:
2015:
1270:
1180:
1176:
1929:
1921:
1894:
1863:
1793:
1710:
1706:
1697:
1674:
1617:
1608:
1589:
1364:
1355:
1336:
126:) breaks up a message into blocks of a fixed size and iterates over them with a
2940:
2860:
2821:
2769:
2754:
2558:
2286:
1748:
1215:"for a new protocol design, a ciphersuite with HMAC-MD5 should not be included"
166:
153:
PUB 198 generalizes and standardizes the use of HMACs. HMAC is used within the
61:
3058:
3021:
2976:
2935:
2915:
2811:
2774:
2749:
2650:
2527:
1887:
1723:
1266:
1152:
657:
559:
146:
138:
68:
2229:
1962:
1796:"On the Security of HMAC and NMAC Based on HAVAL, MD4, MD5, SHA-0 and SHA-1"
1769:
1536:
2971:
2816:
2806:
2796:
2759:
2708:
1486:
1437:
1191:
1156:
650:
is the block-sized inner padding, consisting of repeated bytes valued 0x36.
619:
is the block-sized outer padding, consisting of repeated bytes valued 0x5c.
585:
158:
37:
1944:
2950:
2640:
2486:
2415:
2411:
142:
1418:"SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions"
2910:
2880:
2875:
2836:
1634:
863:
22:
1816:
Wang, Xiaoyun; Yu, Hongbo; Wang, Wei; Zhang, Haina; Zhan, Tao (2009).
1795:
2900:
2315:
2194:
1878:
1689:
1635:"New Proofs for NMAC and HMAC: Security without Collision-Resistance"
1600:
1347:
2102:
1794:
Jongsung, Kim; Biryukov, Alex; Preneel, Bart; Hong, Seokhie (2006).
2945:
2905:
2594:
2491:
2476:
2471:
2461:
2425:
2345:
2259:
2139:
1815:
1304:"Message Authentication using Hash Functions—The HMAC Construction"
1209:
hash function itself is severely compromised – the currently known
1172:
107:
is the hash function used (e.g. HMAC-SHA256 or HMAC-SHA3-512). The
2430:
2386:
2164:
1957:
903:// The output size of the hash function (e.g. 20 bytes for SHA-1)
21:"NMAC" redirects here. For the Nissan Motor Acceptance Corp, see
948:// The block size of the hash function (e.g. 64 bytes for SHA-1)
899:// The block size of the hash function (e.g. 64 bytes for SHA-1)
2826:
2599:
2340:
2335:
2305:
2295:
2254:
2249:
2244:
2224:
2219:
2189:
2174:
2134:
1587:
1378:"FIPS 198-1: The Keyed-Hash Message Authentication Code (HMAC)"
1334:
1101:
1770:"RFC 2104 Errata Held for Document Update · Erdem Memisyazici"
1444:(1995). "MDx-MAC and Building Fast MACs from Hash Functions".
2325:
2214:
2169:
2117:
2074:
2069:
2063:
1164:
1109:
828:
815:
802:
789:
776:
763:
750:
737:
724:
711:
698:
154:
96:
92:
1302:
Bellare, Mihir; Canetti, Ran; Krawczyk, Hugo (Spring 1996).
2440:
2435:
2406:
2365:
1865:
US Secure Hash
Algorithms (SHA and SHA-based HMAC and HKDF)
1680:
1105:
678:
669:
417:
28:
2209:
2204:
2057:
1206:
1202:
1168:
685:
1724:"PBKDF2+HMAC hash collisions explained · Mathias Bynens"
2847:
Cryptographically secure pseudorandom number generator
1301:
1265:
1588:
H. Krawczyk; M. Bellare; R. Canetti (February 1997).
1335:
H. Krawczyk; M. Bellare; R. Canetti (February 1997).
627:
596:
570:
544:
513:
491:
469:
447:
186:
1977:
1485:
1436:
1034:"). The alternative, appending the key using MAC =
1861:
1271:"Keying Hash Functions for Message Authentication"
642:
611:
576:
550:
532:is a block-sized key derived from the secret key,
524:
497:
475:
453:
427:
1952:The Keyed-Hash Message Authentication Code (HMAC)
1658:whose (weak) collision resistance is compromised.
1493:(1995). "On the Security of Two MAC Algorithms".
333:
227:
3056:
1672:
16:Computer communications authentication algorithm
1591:HMAC: Keyed-Hashing for Message Authentication
1338:HMAC: Keyed-Hashing for Message Authentication
122:An iterative hash function (one that uses the
2693:
2001:
326:
280:
264:
234:
1818:"Cryptanalysis on HMAC/NMAC-MD5 and MD5-MAC"
921:hash(o_key_pad ∥ hash(i_key_pad ∥ message))
1907:: CS1 maint: numeric names: authors list (
1183:. HMAC with the full version of MD4 can be
2700:
2686:
2008:
1994:
1668:
1666:
1877:
1862:Eastlake 3rd, D.; Hansen, T. (May 2011).
1688:
1599:
1581:
1498:
1449:
1346:
1330:
1328:
1326:
1324:
1281:
1128:RFC 2104 requires that "keys longer than
91:Any cryptographic hash function, such as
1560:
1423:Federal Information Processing Standards
1382:Federal Information Processing Standards
944:// The hash function to use (e.g. SHA-1)
895:// The hash function to use (e.g. SHA-1)
177:This definition is taken from RFC 2104:
67:HMAC can provide authentication using a
27:
1855:
1663:
1534:
1415:
1269:; Canetti, Ran; Krawczyk, Hugo (1996).
1261:
1259:
1257:
79:. It trades off the need for a complex
3057:
1321:
50:hash-based message authentication code
46:keyed-hash message authentication code
2681:
1989:
1749:"Aaron Toponce : Breaking HMAC"
1297:
1295:
1293:
1254:
1104:hash function, that was selected by
1012:
1945:Online HMAC Generator / Tester Tool
1632:
1537:"Keccak Team – Design and security"
912:i_key_pad ← block_sized_key xor
483:is the message to be authenticated.
13:
978:by padding with zeros on the right
454:{\displaystyle \operatorname {H} }
448:
365:
272:
219:
14:
3081:
1938:
1673:S. Turner; L. Chen (March 2011).
1653:This paper proves that HMAC is a
1416:Dworkin, Morris (4 August 2015).
1396:"FIPS 180-2 with Change Notice 1"
1290:
998:// Pad key with zeros to make it
857:
461:is a cryptographic hash function.
3035:
3034:
2707:
1870:Internet Engineering Task Force
1809:
1787:
1762:
1741:
1716:
1626:
1561:Schneier, Bruce (August 2005).
1554:
397: is larger than block size
2896:Information-theoretic security
2605:NIST hash function competition
1528:
1479:
1430:
1426:– via NIST Publications.
1409:
1388:
1370:
906:// Compute the block sized key
891:// Array of bytes to be hashed
209:
197:
44:(sometimes expanded as either
1:
1247:
1132:bytes are first hashed using
985:(length(key) < blockSize)
962:(length(key) > blockSize)
955:are shortened by hashing them
850:b = H's internal block length
172:
3065:Message authentication codes
2610:Password Hashing Competition
2021:message authentication codes
2017:Cryptographic hash functions
1616:sec. 6. Updated by RFC
1242:HMAC-based one-time password
7:
3012:Message authentication code
2967:Cryptographic hash function
2780:Cryptographic hash function
2564:Merkle–Damgård construction
1235:
1223:
1115:
124:Merkle–Damgård construction
58:cryptographic hash function
54:message authentication code
10:
3086:
2891:Harvest now, decrypt later
1963:Python HMAC implementation
1713:.
1367:.
551:{\displaystyle \parallel }
86:
20:
3030:
3007:Post-quantum cryptography
2959:
2715:
2677:
2628:
2582:
2546:
2500:
2449:
2377:
2354:
2283:
2127:
2088:
2050:
2027:
1985:
1981:
1594:. Network Working Group.
1341:. Network Working Group.
840:
81:public key infrastructure
2997:Quantum key distribution
2987:Authenticated encryption
2842:Random number generation
2358:key derivation functions
1973:Rust HMAC implementation
1213:, but it also adds that
117:length extension attacks
52:) is a specific type of
2992:Public-key cryptography
2982:Symmetric-key algorithm
2785:Key derivation function
2745:Cryptographic primitive
2738:Authentication protocol
2728:Outline of cryptography
2723:History of cryptography
2636:Hash-based cryptography
2538:Length extension attack
1181:second-preimage attacks
1032:length-extension attack
577:{\displaystyle \oplus }
77:asymmetric cryptography
2733:Cryptographic protocol
2646:Message authentication
1843:Cite journal requires
1516:Cite journal requires
1467:Cite journal requires
1123:pseudo-random function
644:
613:
578:
552:
526:
499:
477:
455:
429:
109:cryptographic strength
33:
2886:End-to-end encryption
2832:Cryptojacking malware
1958:C HMAC implementation
1642:Journal of Cryptology
1491:van Oorschot, Paul C.
1442:van Oorschot, Paul C.
970:// Keys shorter than
946:blockSize: Integer
942:hash: Function
938:key: Bytes
927:computeBlockSizedKey
901:outputSize: Integer
897:blockSize: Integer
893:hash: Function
889:message: Bytes
885:key: Bytes
645:
614:
579:
553:
527:
500:
478:
456:
430:
31:
3002:Quantum cryptography
2926:Trusted timestamping
1363:Updated by RFC
996:Pad(key, blockSize)
968:key = hash(key)
951:// Keys longer than
643:{\displaystyle ipad}
625:
612:{\displaystyle opad}
594:
568:
542:
511:
489:
467:
445:
184:
128:compression function
32:HMAC-SHA1 generation
2765:Cryptographic nonce
2533:Side-channel attack
1968:Java implementation
914:// Inner padded key
910:// Outer padded key
2871:Subliminal channel
2855:Pseudorandom noise
2802:Key (cryptography)
2590:CAESAR Competition
2574:HAIFA construction
2523:Brute-force attack
1805:. Springer-Verlag.
1774:www.rfc-editor.org
640:
609:
574:
548:
525:{\displaystyle K'}
522:
505:is the secret key.
495:
473:
451:
425:
423:
416:
165:protocols and for
73:digital signatures
56:(MAC) involving a
34:
3052:
3051:
3048:
3047:
2931:Key-based routing
2921:Trapdoor function
2792:Digital signature
2673:
2672:
2669:
2668:
2467:ChaCha20-Poly1305
2284:Password hashing/
1705:Updates RFC
1276:. pp. 1–15.
1013:Design principles
940:// Array of bytes
887:// Array of bytes
855:
854:
498:{\displaystyle K}
476:{\displaystyle m}
412:
398:
391:
387:
71:instead of using
3077:
3038:
3037:
2866:Insecure channel
2702:
2695:
2688:
2679:
2678:
2554:Avalanche effect
2508:Collision attack
2051:Common functions
2010:
2003:
1996:
1987:
1986:
1983:
1982:
1979:
1978:
1950:FIPS PUB 198-1,
1932:
1912:
1906:
1898:
1881:
1879:10.17487/RFC6234
1859:
1853:
1852:
1846:
1841:
1839:
1831:
1829:
1827:
1822:
1813:
1807:
1806:
1800:
1791:
1785:
1784:
1782:
1780:
1766:
1760:
1759:
1757:
1755:
1745:
1739:
1738:
1736:
1734:
1728:mathiasbynens.be
1720:
1714:
1701:
1692:
1690:10.17487/RFC6151
1670:
1661:
1660:
1650:
1648:
1639:
1633:Bellare, Mihir.
1630:
1624:
1612:
1603:
1601:10.17487/RFC2104
1585:
1579:
1578:
1571:
1569:
1558:
1552:
1551:
1545:
1543:
1532:
1526:
1525:
1519:
1514:
1512:
1504:
1502:
1483:
1477:
1476:
1470:
1465:
1463:
1455:
1453:
1434:
1428:
1427:
1413:
1407:
1406:
1400:
1392:
1386:
1385:
1374:
1368:
1359:
1350:
1348:10.17487/RFC2104
1332:
1319:
1318:
1308:
1299:
1288:
1287:
1285:
1275:
1263:
1143:
1139:
1095:Hamming distance
1007:
1003:
994:
989:
983:
979:
966:
960:
956:
949:
945:
941:
936:
931:
925:
919:
915:
911:
907:
904:
900:
896:
892:
888:
883:
878:
872:
851:
847:
843:
676:
667:
662:
654:
653:
649:
647:
646:
641:
618:
616:
615:
610:
584:denotes bitwise
583:
581:
580:
575:
557:
555:
554:
549:
531:
529:
528:
523:
521:
504:
502:
501:
496:
482:
480:
479:
474:
460:
458:
457:
452:
434:
432:
431:
426:
424:
420:
419:
413:
410:
399:
396:
389:
388:
385:
381:
349:
337:
336:
330:
329:
317:
313:
297:
284:
283:
268:
267:
246:
238:
237:
231:
230:
3085:
3084:
3080:
3079:
3078:
3076:
3075:
3074:
3055:
3054:
3053:
3044:
3026:
2955:
2711:
2706:
2665:
2624:
2583:Standardization
2578:
2569:Sponge function
2542:
2518:Birthday attack
2513:Preimage attack
2496:
2452:
2445:
2373:
2356:
2355:General purpose
2350:
2285:
2279:
2128:Other functions
2123:
2090:SHA-3 finalists
2084:
2046:
2023:
2014:
1941:
1936:
1935:
1900:
1899:
1860:
1856:
1844:
1842:
1833:
1832:
1825:
1823:
1820:
1814:
1810:
1798:
1792:
1788:
1778:
1776:
1768:
1767:
1763:
1753:
1751:
1747:
1746:
1742:
1732:
1730:
1722:
1721:
1717:
1671:
1664:
1646:
1644:
1637:
1631:
1627:
1586:
1582:
1567:
1565:
1559:
1555:
1541:
1539:
1533:
1529:
1517:
1515:
1506:
1505:
1484:
1480:
1468:
1466:
1457:
1456:
1435:
1431:
1414:
1410:
1398:
1394:
1393:
1389:
1384:. 16 July 2008.
1376:
1375:
1371:
1333:
1322:
1306:
1300:
1291:
1283:10.1.1.134.8430
1273:
1264:
1255:
1250:
1238:
1233:
1226:
1177:random function
1141:
1140:is computed as
1137:
1118:
1015:
1010:
1005:
997:
992:
987:
981:
969:
964:
958:
950:
947:
943:
939:
934:
929:
923:
917:
913:
909:
905:
902:
898:
894:
890:
886:
881:
876:
870:
860:
849:
848:
846:L = length(out)
845:
844:
841:
674:
665:
660:
626:
623:
622:
595:
592:
591:
569:
566:
565:
543:
540:
539:
514:
512:
509:
508:
490:
487:
486:
468:
465:
464:
446:
443:
442:
422:
421:
415:
414:
409:
407:
401:
400:
395:
384:
382:
371:
358:
357:
350:
342:
339:
338:
332:
331:
325:
324:
290:
289:
285:
279:
278:
263:
262:
239:
233:
232:
226:
225:
212:
187:
185:
182:
181:
175:
167:JSON Web Tokens
89:
26:
17:
12:
11:
5:
3083:
3073:
3072:
3067:
3050:
3049:
3046:
3045:
3043:
3042:
3031:
3028:
3027:
3025:
3024:
3019:
3017:Random numbers
3014:
3009:
3004:
2999:
2994:
2989:
2984:
2979:
2974:
2969:
2963:
2961:
2957:
2956:
2954:
2953:
2948:
2943:
2941:Garlic routing
2938:
2933:
2928:
2923:
2918:
2913:
2908:
2903:
2898:
2893:
2888:
2883:
2878:
2873:
2868:
2863:
2861:Secure channel
2858:
2852:
2851:
2850:
2839:
2834:
2829:
2824:
2822:Key stretching
2819:
2814:
2809:
2804:
2799:
2794:
2789:
2788:
2787:
2782:
2772:
2770:Cryptovirology
2767:
2762:
2757:
2755:Cryptocurrency
2752:
2747:
2742:
2741:
2740:
2730:
2725:
2719:
2717:
2713:
2712:
2705:
2704:
2697:
2690:
2682:
2675:
2674:
2671:
2670:
2667:
2666:
2664:
2663:
2658:
2653:
2648:
2643:
2638:
2632:
2630:
2626:
2625:
2623:
2622:
2617:
2612:
2607:
2602:
2597:
2592:
2586:
2584:
2580:
2579:
2577:
2576:
2571:
2566:
2561:
2559:Hash collision
2556:
2550:
2548:
2544:
2543:
2541:
2540:
2535:
2530:
2525:
2520:
2515:
2510:
2504:
2502:
2498:
2497:
2495:
2494:
2489:
2484:
2479:
2474:
2469:
2464:
2458:
2456:
2447:
2446:
2444:
2443:
2438:
2433:
2428:
2423:
2418:
2409:
2404:
2399:
2394:
2389:
2383:
2381:
2375:
2374:
2372:
2371:
2368:
2362:
2360:
2352:
2351:
2349:
2348:
2343:
2338:
2333:
2328:
2323:
2318:
2313:
2308:
2303:
2298:
2292:
2290:
2287:key stretching
2281:
2280:
2278:
2277:
2272:
2267:
2262:
2257:
2252:
2247:
2242:
2237:
2232:
2227:
2222:
2217:
2212:
2207:
2202:
2197:
2192:
2187:
2182:
2177:
2172:
2167:
2162:
2157:
2152:
2147:
2142:
2137:
2131:
2129:
2125:
2124:
2122:
2121:
2115:
2110:
2105:
2100:
2094:
2092:
2086:
2085:
2083:
2082:
2077:
2072:
2067:
2061:
2054:
2052:
2048:
2047:
2045:
2044:
2039:
2034:
2028:
2025:
2024:
2013:
2012:
2005:
1998:
1990:
1976:
1975:
1970:
1965:
1960:
1955:
1947:
1940:
1939:External links
1937:
1934:
1933:
1914:Informational.
1854:
1845:|journal=
1808:
1786:
1761:
1740:
1715:
1703:Informational.
1662:
1625:
1614:Informational.
1580:
1563:"SHA-1 Broken"
1553:
1527:
1518:|journal=
1500:10.1.1.42.8908
1478:
1469:|journal=
1451:10.1.1.34.3855
1429:
1408:
1387:
1369:
1361:Informational.
1320:
1289:
1267:Bellare, Mihir
1252:
1251:
1249:
1246:
1245:
1244:
1237:
1234:
1230:
1225:
1222:
1117:
1114:
1014:
1011:
974:are padded to
868:
862:The following
859:
858:Implementation
856:
853:
852:
838:
837:
834:
831:
825:
824:
821:
818:
812:
811:
808:
805:
799:
798:
795:
792:
786:
785:
782:
779:
773:
772:
769:
766:
760:
759:
756:
753:
747:
746:
743:
740:
734:
733:
730:
727:
721:
720:
717:
714:
708:
707:
704:
701:
695:
694:
691:
688:
682:
681:
672:
663:
652:
651:
639:
636:
633:
630:
620:
608:
605:
602:
599:
589:
573:
563:
547:
537:
520:
517:
506:
494:
484:
472:
462:
450:
436:
435:
418:
408:
406:
403:
402:
394:
383:
380:
377:
374:
370:
367:
364:
363:
361:
356:
353:
351:
348:
345:
341:
340:
335:
328:
323:
320:
316:
312:
309:
306:
303:
300:
296:
293:
288:
282:
277:
274:
271:
266:
261:
258:
255:
252:
249:
245:
242:
236:
229:
224:
221:
218:
215:
213:
211:
208:
205:
202:
199:
196:
193:
190:
189:
174:
171:
88:
85:
62:data integrity
15:
9:
6:
4:
3:
2:
3082:
3071:
3068:
3066:
3063:
3062:
3060:
3041:
3033:
3032:
3029:
3023:
3022:Steganography
3020:
3018:
3015:
3013:
3010:
3008:
3005:
3003:
3000:
2998:
2995:
2993:
2990:
2988:
2985:
2983:
2980:
2978:
2977:Stream cipher
2975:
2973:
2970:
2968:
2965:
2964:
2962:
2958:
2952:
2949:
2947:
2944:
2942:
2939:
2937:
2936:Onion routing
2934:
2932:
2929:
2927:
2924:
2922:
2919:
2917:
2916:Shared secret
2914:
2912:
2909:
2907:
2904:
2902:
2899:
2897:
2894:
2892:
2889:
2887:
2884:
2882:
2879:
2877:
2874:
2872:
2869:
2867:
2864:
2862:
2859:
2856:
2853:
2848:
2845:
2844:
2843:
2840:
2838:
2835:
2833:
2830:
2828:
2825:
2823:
2820:
2818:
2815:
2813:
2812:Key generator
2810:
2808:
2805:
2803:
2800:
2798:
2795:
2793:
2790:
2786:
2783:
2781:
2778:
2777:
2776:
2775:Hash function
2773:
2771:
2768:
2766:
2763:
2761:
2758:
2756:
2753:
2751:
2750:Cryptanalysis
2748:
2746:
2743:
2739:
2736:
2735:
2734:
2731:
2729:
2726:
2724:
2721:
2720:
2718:
2714:
2710:
2703:
2698:
2696:
2691:
2689:
2684:
2683:
2680:
2676:
2662:
2659:
2657:
2654:
2652:
2651:Proof of work
2649:
2647:
2644:
2642:
2639:
2637:
2634:
2633:
2631:
2627:
2621:
2618:
2616:
2613:
2611:
2608:
2606:
2603:
2601:
2598:
2596:
2593:
2591:
2588:
2587:
2585:
2581:
2575:
2572:
2570:
2567:
2565:
2562:
2560:
2557:
2555:
2552:
2551:
2549:
2545:
2539:
2536:
2534:
2531:
2529:
2528:Rainbow table
2526:
2524:
2521:
2519:
2516:
2514:
2511:
2509:
2506:
2505:
2503:
2499:
2493:
2490:
2488:
2485:
2483:
2480:
2478:
2475:
2473:
2470:
2468:
2465:
2463:
2460:
2459:
2457:
2454:
2451:Authenticated
2448:
2442:
2439:
2437:
2434:
2432:
2429:
2427:
2424:
2422:
2419:
2417:
2413:
2410:
2408:
2405:
2403:
2400:
2398:
2395:
2393:
2390:
2388:
2385:
2384:
2382:
2380:
2379:MAC functions
2376:
2369:
2367:
2364:
2363:
2361:
2359:
2353:
2347:
2344:
2342:
2339:
2337:
2334:
2332:
2329:
2327:
2324:
2322:
2319:
2317:
2314:
2312:
2309:
2307:
2304:
2302:
2299:
2297:
2294:
2293:
2291:
2288:
2282:
2276:
2273:
2271:
2268:
2266:
2263:
2261:
2258:
2256:
2253:
2251:
2248:
2246:
2243:
2241:
2238:
2236:
2233:
2231:
2228:
2226:
2223:
2221:
2218:
2216:
2213:
2211:
2208:
2206:
2203:
2201:
2198:
2196:
2193:
2191:
2188:
2186:
2183:
2181:
2178:
2176:
2173:
2171:
2168:
2166:
2163:
2161:
2158:
2156:
2153:
2151:
2148:
2146:
2143:
2141:
2138:
2136:
2133:
2132:
2130:
2126:
2119:
2116:
2114:
2111:
2109:
2106:
2104:
2101:
2099:
2096:
2095:
2093:
2091:
2087:
2081:
2078:
2076:
2073:
2071:
2068:
2066:(compromised)
2065:
2062:
2060:(compromised)
2059:
2056:
2055:
2053:
2049:
2043:
2042:Known attacks
2040:
2038:
2035:
2033:
2030:
2029:
2026:
2022:
2018:
2011:
2006:
2004:
1999:
1997:
1992:
1991:
1988:
1984:
1980:
1974:
1971:
1969:
1966:
1964:
1961:
1959:
1956:
1954:
1953:
1948:
1946:
1943:
1942:
1931:
1927:
1923:
1919:
1915:
1910:
1904:
1896:
1893:
1889:
1885:
1880:
1875:
1871:
1867:
1866:
1858:
1850:
1837:
1819:
1812:
1804:
1797:
1790:
1775:
1771:
1765:
1750:
1744:
1729:
1725:
1719:
1712:
1708:
1704:
1699:
1696:
1691:
1686:
1682:
1678:
1677:
1669:
1667:
1659:
1656:
1643:
1636:
1629:
1623:
1619:
1615:
1610:
1607:
1602:
1597:
1593:
1592:
1584:
1577:
1576:
1564:
1557:
1550:
1538:
1535:Keccak team.
1531:
1523:
1510:
1501:
1496:
1492:
1488:
1487:Preneel, Bart
1482:
1474:
1461:
1452:
1447:
1443:
1439:
1438:Preneel, Bart
1433:
1425:
1424:
1419:
1412:
1404:
1403:csrc.nist.gov
1397:
1391:
1383:
1379:
1373:
1366:
1362:
1357:
1354:
1349:
1344:
1340:
1339:
1331:
1329:
1327:
1325:
1316:
1312:
1305:
1298:
1296:
1294:
1284:
1279:
1272:
1268:
1262:
1260:
1258:
1253:
1243:
1240:
1239:
1229:
1221:
1218:
1216:
1212:
1208:
1204:
1199:
1196:
1193:
1188:
1186:
1182:
1178:
1174:
1170:
1166:
1162:
1158:
1154:
1153:Alex Biryukov
1150:
1145:
1142:HMAC(H(k), m)
1135:
1131:
1126:
1124:
1113:
1111:
1107:
1103:
1098:
1096:
1092:
1088:
1084:
1080:
1076:
1072:
1068:
1063:
1061:
1057:
1053:
1049:
1045:
1041:
1037:
1033:
1029:
1025:
1021:
1008:
1001:
995:
990:
984:
977:
973:
967:
961:
954:
937:
932:
926:
920:
884:
879:
873:
867:
865:
839:
835:
832:
830:
827:
826:
822:
819:
817:
814:
813:
809:
806:
804:
801:
800:
796:
793:
791:
788:
787:
783:
780:
778:
775:
774:
770:
767:
765:
762:
761:
757:
754:
752:
749:
748:
744:
741:
739:
736:
735:
731:
728:
726:
723:
722:
718:
715:
713:
710:
709:
705:
702:
700:
697:
696:
692:
689:
687:
684:
683:
680:
673:
671:
664:
659:
658:Hash function
656:
655:
637:
634:
631:
628:
621:
606:
603:
600:
597:
590:
587:
571:
564:
561:
560:concatenation
545:
538:
535:
518:
515:
507:
492:
485:
470:
463:
441:
440:
439:
404:
392:
378:
375:
372:
368:
359:
354:
352:
346:
343:
321:
318:
314:
310:
307:
304:
301:
298:
294:
291:
286:
275:
269:
259:
256:
253:
250:
247:
243:
240:
222:
216:
214:
206:
203:
200:
194:
191:
180:
179:
178:
170:
168:
164:
160:
156:
152:
148:
147:Hugo Krawczyk
144:
140:
139:Mihir Bellare
135:
131:
129:
125:
120:
118:
112:
110:
106:
102:
98:
94:
84:
82:
78:
74:
70:
69:shared secret
65:
63:
59:
55:
51:
47:
43:
39:
30:
24:
19:
2972:Block cipher
2817:Key schedule
2807:Key exchange
2797:Kleptography
2760:Cryptosystem
2709:Cryptography
2401:
1951:
1913:
1864:
1857:
1836:cite journal
1824:. Retrieved
1811:
1802:
1789:
1779:23 September
1777:. Retrieved
1773:
1764:
1752:. Retrieved
1743:
1731:. Retrieved
1727:
1718:
1702:
1675:
1652:
1645:. Retrieved
1641:
1628:
1621:
1613:
1590:
1583:
1574:
1573:
1566:. Retrieved
1556:
1547:
1540:. Retrieved
1530:
1509:cite journal
1481:
1460:cite journal
1432:
1421:
1411:
1402:
1390:
1381:
1372:
1360:
1337:
1314:
1310:
1227:
1219:
1214:
1210:
1200:
1194:
1192:Xiaoyun Wang
1189:
1161:Seokhie Hong
1157:Bart Preneel
1149:Jongsung Kim
1146:
1133:
1129:
1127:
1119:
1099:
1090:
1086:
1082:
1078:
1074:
1070:
1066:
1064:
1059:
1055:
1051:
1047:
1043:
1039:
1035:
1027:
1023:
1019:
1016:
1004:
999:
991:
986:
980:
975:
971:
963:
957:
952:
933:
928:
922:
916:
880:
875:
869:
861:
586:exclusive or
533:
437:
176:
136:
132:
121:
113:
104:
100:
90:
66:
49:
45:
41:
38:cryptography
35:
18:
2960:Mathematics
2951:Mix network
2641:Merkle tree
2629:Utilization
2615:NSA Suite B
1647:15 December
1311:CryptoBytes
842:out = H(in)
751:SHA-512/256
738:SHA-512/224
143:Ran Canetti
3059:Categories
2911:Ciphertext
2881:Decryption
2876:Encryption
2837:Ransomware
2453:encryption
2230:RadioGatún
2037:Comparison
1924:. Updates
1916:Obsoletes
1542:31 October
1248:References
1138:HMAC(k, m)
1002:bytes long
864:pseudocode
173:Definition
23:Nissan USA
2901:Plaintext
2370:KDF1/KDF2
2289:functions
2275:Whirlpool
1888:2070-1721
1568:9 January
1495:CiteSeerX
1446:CiteSeerX
1278:CiteSeerX
1190:In 2009,
1147:In 2006,
1000:blockSize
976:blockSize
972:blockSize
953:blockSize
572:⊕
546:∥
411:otherwise
369:
319:∥
299:⊕
276:
270:∥
248:⊕
223:
195:
3040:Category
2946:Kademlia
2906:Codetext
2849:(CSPRNG)
2595:CRYPTREC
2426:Poly1305
2346:yescrypt
2260:Streebog
2140:CubeHash
2120:(winner)
1903:citation
1803:SCN 2006
1754:7 August
1733:7 August
1236:See also
1224:Examples
1116:Security
924:function
871:function
829:SHA3-512
816:SHA3-384
803:SHA3-256
790:SHA3-224
558:denotes
519:′
347:′
295:′
244:′
103:, where
3070:Hashing
2716:General
2501:Attacks
2431:SipHash
2387:CBC-MAC
2321:LM hash
2301:Balloon
2165:HAS-160
1826:15 June
1175:from a
1108:as the
1083:message
1056:message
1040:message
1028:message
777:SHA-512
764:SHA-384
725:SHA-256
712:SHA-224
87:Details
2827:Keygen
2661:Pepper
2600:NESSIE
2547:Design
2341:scrypt
2336:PBKDF2
2311:Catena
2306:bcrypt
2296:Argon2
2255:Snefru
2250:Shabal
2245:SWIFFT
2225:RIPEMD
2220:N-hash
2195:MASH-2
2190:MASH-1
2175:Kupyna
2135:BLAKE3
2118:Keccak
2103:Grøstl
2080:BLAKE2
1928:
1920:
1886:
1497:
1448:
1280:
1195:et al.
1185:forged
1171:, and
1159:, and
1102:Keccak
1006:return
993:return
935:input:
918:return
882:input:
588:(XOR).
438:where
390:
145:, and
2857:(PRN)
2455:modes
2331:Makwa
2326:Lyra2
2316:crypt
2265:Tiger
2215:MDC-2
2170:HAVAL
2155:Fugue
2113:Skein
2098:BLAKE
2075:SHA-3
2070:SHA-2
2064:SHA-1
1821:(PDF)
1799:(PDF)
1638:(PDF)
1399:(PDF)
1307:(PDF)
1274:(PDF)
1173:SHA-0
1165:HAVAL
1110:SHA-3
874:hmac
699:SHA-1
679:bytes
670:bytes
155:IPsec
97:SHA-3
93:SHA-2
75:with
40:, an
2656:Salt
2620:CNSA
2487:IAPM
2441:VMAC
2436:UMAC
2421:PMAC
2416:CMAC
2412:OMAC
2407:NMAC
2402:HMAC
2397:GMAC
2366:HKDF
2235:SIMD
2185:Lane
2160:GOST
2145:ECOH
2032:List
2019:and
1930:3174
1922:4634
1909:link
1895:6234
1884:ISSN
1849:help
1828:2015
1781:2016
1756:2019
1735:2019
1711:1321
1709:and
1707:2104
1698:6151
1681:IETF
1649:2021
1618:6151
1609:2104
1570:2009
1549:key.
1544:2019
1522:help
1473:help
1365:6151
1356:2104
1317:(1).
1106:NIST
1100:The
1091:opad
1089:and
1087:ipad
1009:key
988:then
965:then
192:HMAC
161:and
151:FIPS
42:HMAC
2492:OCB
2482:GCM
2477:EAX
2472:CWC
2462:CCM
2392:DAA
2270:VSH
2240:SM3
2210:MD6
2205:MD4
2200:MD2
2180:LSH
2150:FSB
2058:MD5
1926:RFC
1918:RFC
1892:RFC
1874:doi
1695:RFC
1685:doi
1655:PRF
1606:RFC
1596:doi
1353:RFC
1343:doi
1207:MD5
1203:MD5
1169:MD4
1079:key
1071:key
1060:key
1052:key
1044:key
1024:key
836:64
823:48
820:104
810:32
807:136
797:28
794:144
784:64
781:128
771:48
768:128
758:32
755:128
745:28
742:128
732:32
719:28
706:20
693:16
686:MD5
163:TLS
159:SSH
95:or
48:or
36:In
3061::
2108:JH
1905:}}
1901:{{
1890:.
1882:.
1872:.
1868:.
1840::
1838:}}
1834:{{
1801:.
1772:.
1726:.
1693:.
1683:.
1679:.
1665:^
1651:.
1640:.
1620:.
1604:.
1572:.
1546:.
1513::
1511:}}
1507:{{
1489:;
1464::
1462:}}
1458:{{
1440:;
1420:.
1401:.
1380:.
1351:.
1323:^
1313:.
1309:.
1292:^
1256:^
1217:.
1167:,
1155:,
1151:,
1081:∥
1073:∥
1058:∥
1054:∥
1042:∥
1026:∥
982:if
959:if
930:is
877:is
833:72
729:64
716:64
703:64
690:64
677:,
668:,
386:if
169:.
157:,
141:,
119:.
2701:e
2694:t
2687:v
2414:/
2009:e
2002:t
1995:v
1911:)
1897:.
1876::
1851:)
1847:(
1830:.
1783:.
1758:.
1737:.
1700:.
1687::
1611:.
1598::
1524:)
1520:(
1503:.
1475:)
1471:(
1454:.
1405:.
1358:.
1345::
1315:2
1286:.
1134:H
1130:B
1077:(
1075:H
1069:(
1067:H
1050:(
1048:H
1038:(
1036:H
1022:(
1020:H
675:L
666:b
661:H
638:d
635:a
632:p
629:i
607:d
604:a
601:p
598:o
562:.
534:K
516:K
493:K
471:m
449:H
405:K
393:K
379:)
376:K
373:(
366:H
360:{
355:=
344:K
334:)
327:)
322:m
315:)
311:d
308:a
305:p
302:i
292:K
287:(
281:(
273:H
265:)
260:d
257:a
254:p
251:o
241:K
235:(
228:(
220:H
217:=
210:)
207:m
204:,
201:K
198:(
105:x
101:x
25:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.