27:
91:
2822:
1028:
In 2009, Lu presented a related-key rectangle attack on 36 rounds of XTEA, breaking more rounds than any previously published cryptanalytic results for XTEA. The paper presents two attacks, one without and with a weak key assumption, which corresponds to 2 bytes of data and 2 operations, and 2 bytes
995:
The recommended value for the "num_rounds" parameter is 32, not 64, as each iteration of the loop does two
Feistel-cipher rounds. To additionally improve speed, the loop can be unrolled by pre-computing the values of sum+key.
1041:, which uses the XTEA round function, but Block TEA applies it cyclically across an entire message for several iterations. Because it operates on the entire message, Block TEA has the property that it does not need a
1167:
Hong, Seokhie; Hong, Deukjo; Ko, Youngdai; Chang, Donghoon; Lee, Wonil; Lee, Sangjin (2004). "Differential
Cryptanalysis of TEA and XTEA". In Lim, JI.; Lee, DH. (eds.).
1457:
2802:
2632:
2875:
2870:
1314:
Moon, Dukjae; Hwang, Kyungdeok; Lee, Wonil; Lee, Sangjin; Lim, Jongin (2002). "Impossible
Differential Cryptanalysis of Reduced Round XTEA and TEA".
2855:
2485:
2420:
1501:
246:
249:, and the algorithm was presented in an unpublished technical report in 1997 (Needham and Wheeler, 1997). It is not subject to any
2247:
1603:
1429:
2237:
1731:
1335:
1297:
1184:
1144:
2400:
2374:
2242:
2138:
1454:
2215:
238:
115:
2478:
1045:. An attack on the full Block TEA was described by Saarinen, which also details a weakness in Block TEA's successor,
70:
48:
41:
2384:
1494:
2263:
1171:. ICISC 2003. Lecture Notes in Computer Science. Vol. 2971. Berlin, Heidelberg: Springer. pp. 402–417.
1042:
987:
The reference source code omitted redundant parentheses, using C precedence to write the round function as e.g.
2681:
2441:
1385:
1129:. FSE 2004. Lecture Notes in Computer Science. Vol. 3017. Berlin, Heidelberg: Springer. pp. 299–316.
1403:
1420:
2471:
1531:
2797:
2752:
2565:
2327:
1487:
267:
and a suggested 64 rounds. Several differences from TEA are apparent, including a somewhat more complex
2676:
2344:
2254:
2232:
1545:
2792:
2349:
2205:
2158:
1633:
1074:
257:
230:
165:
133:
2860:
2782:
2772:
2627:
2415:
2297:
2172:
1541:
1444:
284:
264:
35:
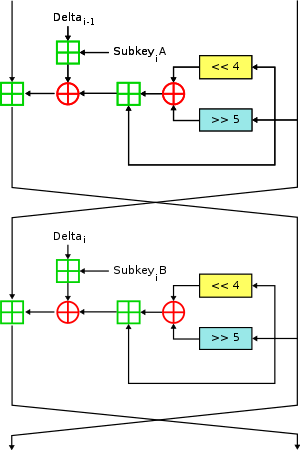
1277:
1200:
Lu, Jiqiang (July 2, 2008). "Related-key rectangle attack on 36 rounds of the XTEA block cipher".
2777:
2767:
2570:
2530:
2523:
2513:
2508:
2354:
2143:
1514:
1439:
2850:
2518:
2446:
2322:
2317:
2269:
1353:
52:
1395:
2865:
2825:
2671:
2617:
2436:
2259:
2118:
1696:
1119:
2787:
2711:
2339:
2222:
2148:
1831:
1811:
185:
8:
2550:
2302:
2279:
1598:
1412:
1014:
1315:
2656:
2640:
2587:
2287:
2195:
1907:
1836:
1806:
1751:
1225:
1011:
204:
2716:
2706:
2577:
2007:
1706:
1666:
1661:
1628:
1588:
1536:
1331:
1293:
1244:
1217:
1180:
1140:
1229:
2651:
2379:
2274:
2153:
2012:
1892:
1861:
1555:
1321:
1283:
1209:
1172:
1130:
1018:
1276:(2011). "Meet-in-the-Middle Attacks on Reduced-Round XTEA". In Kiayias, A. (ed.).
2226:
2210:
2199:
2133:
2092:
2057:
1987:
1967:
1841:
1721:
1716:
1671:
1461:
1424:
1407:
1288:
1176:
1135:
1022:
1445:
Linden
Scripting Language (LSL) implementation of XTEA for Second Life scripting
2726:
2646:
2607:
2555:
2540:
2364:
2312:
2123:
2108:
2047:
2042:
1927:
1676:
1390:
260:
178:
1213:
2844:
2807:
2762:
2721:
2701:
2597:
2560:
2535:
2359:
2307:
2186:
2168:
1957:
1932:
1922:
1746:
1736:
1583:
1386:
A web page advocating TEA and XTEA and providing a variety of implementations
1221:
1118:
Ko, Youngdai; Hong, Seokhie; Lee, Wonil; Lee, Sangjin; Kang, Ju-Sung (2004).
1062:
1005:
288:
242:
196:
111:
1326:
1095:
2757:
2602:
2592:
2582:
2545:
2494:
2292:
2113:
2077:
1942:
1821:
1776:
1608:
1560:
1510:
1273:
1120:"Related Key Differential Attacks on 27 Rounds of XTEA and Full-Round GOST"
268:
226:
214:
2736:
1902:
1897:
1781:
1380:
2696:
2666:
2661:
2622:
2334:
2052:
1992:
1876:
1871:
1816:
1686:
1549:
1282:. Lecture Notes in Computer Science. Vol. 6558. pp. 250–267.
90:
1434:
291:
by David
Wheeler and Roger Needham, encrypts and decrypts using XTEA:
2686:
2067:
2062:
1952:
1866:
1761:
1741:
1320:. Lecture Notes in Computer Science. Vol. 2365. pp. 49–60.
1449:
2731:
2691:
2405:
2369:
2163:
1826:
1701:
1681:
1593:
1466:
1400:
1037:
Presented along with XTEA was a variable-width block cipher termed
155:
1417:
2072:
2022:
1982:
1972:
1917:
1912:
1756:
1565:
1065:
that, just like XTEA, is designed to be very simple to implement.
1093:
2612:
2410:
2032:
2027:
1962:
1947:
1937:
1882:
1856:
1851:
1846:
1726:
1711:
970:
302:/* take 64 bits of data in v and v and 128 bits of key - key */
287:
source code, adapted from the reference code released into the
250:
234:
2128:
2087:
2037:
2017:
2002:
1791:
1771:
1691:
1656:
1068:
1046:
143:
1977:
1886:
1801:
1796:
1786:
1766:
1623:
1271:
2082:
1997:
1618:
1613:
1058:
272:
1361:(Masters thesis). The University of Alabama, Tuscaloosa
2633:
Cryptographically secure pseudorandom number generator
961:
The changes from the reference source code are minor:
1509:
1471:
1272:Sekar, Gautham; Mouha, Nicky; Velichkov, Vesselin;
1094:Roger M. Needham; David J. Wheeler (October 1997).
190:
variable; recommended 64 Feistel rounds (32 cycles)
2842:
1396:A Cryptanalysis of the Tiny Encryption Algorithm
1355:A cryptanalysis of the Tiny Encryption Algorithm
989:v1 += (v0<<4 ^ v0>>5) + v0 ^ sum + k
207:rectangle attack on 36 rounds of XTEA (Lu, 2009)
1313:
1166:
2479:
1495:
1435:JavaScript implementation of XTEA (32 rounds)
1202:International Journal of Information Security
1243:Saarinen, Markku-Juhani (October 20, 1998).
1117:
1105:Computer Laboratory, University of Cambridge
1017:on 27 out of 64 rounds of XTEA, requiring 2
2876:University of Cambridge Computer Laboratory
2871:History of computing in the United Kingdom
2486:
2472:
1502:
1488:
1325:
1287:
1134:
71:Learn how and when to remove this message
1242:
34:This article includes a list of general
2856:Computer security in the United Kingdom
1430:Java implementation of XTEA (32 rounds)
1029:of data and 2 operations respectively.
2843:
1087:
980:The reference source code did not use
97:Two Feistel rounds (one cycle) of XTEA
2467:
1483:
1351:
1418:Pascal/Delphi implementation of XTEA
20:
1169:Information Security and Cryptology
965:The reference source code used the
271:and a rearrangement of the shifts,
13:
1279:Topics in Cryptology – CT-RSA 2011
1265:
1199:
278:
229:designed to correct weaknesses in
89:
40:it lacks sufficient corresponding
14:
2887:
1467:PostgreSQL implementation of XTEA
1374:
2821:
2820:
2493:
1455:Smalltalk implementation of XTEA
1125:. In Roy, B.; Meier, W. (eds.).
999:
25:
1010:In 2004, Ko et al. presented a
2682:Information-theoretic security
1450:Verilog implementation of XTEA
1236:
1193:
1160:
1111:
1:
1440:Python implementation of XTEA
1391:Test vectors for TEA and XTEA
1081:
247:Cambridge Computer Laboratory
1352:Andem, Vikram Reddy (2003).
1289:10.1007/978-3-642-19074-2_17
1245:"Cryptanalysis of Block Tea"
1177:10.1007/978-3-540-24691-6_30
1136:10.1007/978-3-540-25937-4_19
1032:
7:
2798:Message authentication code
2753:Cryptographic hash function
2566:Cryptographic hash function
1052:
10:
2892:
2677:Harvest now, decrypt later
1413:PHP implementation of XTEA
1406:February 24, 2023, at the
1401:A C implementation of XTEA
1003:
2816:
2793:Post-quantum cryptography
2745:
2501:
2463:
2429:
2393:
2385:Time/memory/data tradeoff
2182:
2101:
1647:
1574:
1522:
1479:
1475:
1423:October 22, 2008, at the
1214:10.1007/s10207-008-0059-9
202:
194:
184:
174:
164:
154:
149:
139:
129:
121:
107:
102:
88:
2783:Quantum key distribution
2773:Authenticated encryption
2628:Random number generation
2173:Whitening transformation
1317:Fast Software Encryption
1127:Fast Software Encryption
1077:— Block TEA's precursor.
1071:— Block TEA's successor.
293:
2778:Public-key cryptography
2768:Symmetric-key algorithm
2571:Key derivation function
2531:Cryptographic primitive
2524:Authentication protocol
2514:Outline of cryptography
2509:History of cryptography
2144:Confusion and diffusion
1327:10.1007/3-540-45661-9_4
55:more precise citations.
2519:Cryptographic protocol
1460:March 4, 2016, at the
94:
2672:End-to-end encryption
2618:Cryptojacking malware
2437:Initialization vector
969:type rather than the
93:
2788:Quantum cryptography
2712:Trusted timestamping
2216:3-subset MITM attack
1832:Intel Cascade Cipher
1812:Hasty Pudding cipher
256:Like TEA, XTEA is a
2551:Cryptographic nonce
2255:Differential-linear
1107:(Technical report).
1015:differential attack
144:Corrected Block TEA
85:
2657:Subliminal channel
2641:Pseudorandom noise
2588:Key (cryptography)
2328:Differential-fault
1546:internal mechanics
237:'s designers were
95:
83:
2838:
2837:
2834:
2833:
2717:Key-based routing
2707:Trapdoor function
2578:Digital signature
2459:
2458:
2455:
2454:
2442:Mode of operation
2119:Lai–Massey scheme
1337:978-3-540-44009-3
1299:978-3-642-19073-5
1186:978-3-540-21376-5
1146:978-3-540-22171-5
1043:mode of operation
1019:chosen plaintexts
275:, and additions.
211:
210:
81:
80:
73:
2883:
2824:
2823:
2652:Insecure channel
2488:
2481:
2474:
2465:
2464:
2313:Power-monitoring
2154:Avalanche effect
1862:Khufu and Khafre
1515:security summary
1504:
1497:
1490:
1481:
1480:
1477:
1476:
1473:
1472:
1381:DataFlow Diagram
1370:
1368:
1366:
1360:
1348:
1346:
1344:
1329:
1310:
1308:
1306:
1291:
1260:
1259:
1257:
1255:
1240:
1234:
1233:
1197:
1191:
1190:
1164:
1158:
1157:
1155:
1153:
1138:
1124:
1115:
1109:
1108:
1102:
1091:
990:
983:
976:
968:
957:
954:
951:
948:
945:
942:
939:
936:
933:
930:
927:
924:
921:
918:
915:
912:
909:
906:
903:
900:
897:
894:
891:
888:
885:
882:
879:
876:
873:
870:
867:
864:
861:
858:
855:
852:
849:
846:
843:
840:
837:
834:
831:
828:
825:
822:
819:
816:
813:
810:
807:
804:
801:
798:
795:
792:
789:
786:
783:
780:
777:
774:
771:
768:
765:
762:
759:
756:
753:
750:
747:
744:
741:
738:
735:
732:
729:
726:
723:
720:
717:
714:
711:
708:
705:
702:
699:
696:
693:
690:
687:
684:
681:
678:
675:
672:
669:
666:
663:
660:
657:
654:
651:
648:
645:
642:
639:
636:
633:
630:
627:
624:
621:
618:
615:
612:
609:
606:
603:
600:
597:
594:
591:
588:
585:
582:
579:
576:
573:
570:
567:
564:
561:
558:
555:
552:
549:
546:
543:
540:
537:
534:
531:
528:
525:
522:
519:
516:
513:
510:
507:
504:
501:
498:
495:
492:
489:
486:
483:
480:
477:
474:
471:
468:
465:
462:
459:
456:
453:
450:
447:
444:
441:
438:
435:
432:
429:
426:
423:
420:
417:
414:
411:
408:
405:
402:
399:
396:
393:
390:
387:
384:
381:
378:
375:
372:
369:
366:
363:
360:
357:
354:
351:
348:
345:
342:
339:
336:
333:
330:
327:
324:
321:
318:
315:
312:
309:
306:
303:
300:
299:<stdint.h>
297:
86:
82:
76:
69:
65:
62:
56:
51:this article by
42:inline citations
29:
28:
21:
2891:
2890:
2886:
2885:
2884:
2882:
2881:
2880:
2861:Feistel ciphers
2841:
2840:
2839:
2830:
2812:
2741:
2497:
2492:
2451:
2425:
2394:Standardization
2389:
2318:Electromagnetic
2270:Integral/Square
2227:Piling-up lemma
2211:Biclique attack
2200:EFF DES cracker
2184:
2178:
2109:Feistel network
2097:
1722:CIPHERUNICORN-E
1717:CIPHERUNICORN-A
1649:
1643:
1576:
1570:
1524:
1518:
1508:
1462:Wayback Machine
1425:Wayback Machine
1408:Wayback Machine
1377:
1364:
1362:
1358:
1342:
1340:
1338:
1304:
1302:
1300:
1268:
1266:Further reading
1263:
1253:
1251:
1241:
1237:
1198:
1194:
1187:
1165:
1161:
1151:
1149:
1147:
1122:
1116:
1112:
1100:
1092:
1088:
1084:
1055:
1035:
1023:time complexity
1008:
1002:
988:
981:
974:
966:
959:
958:
955:
952:
949:
946:
943:
940:
937:
934:
931:
928:
925:
922:
919:
916:
913:
910:
907:
904:
901:
898:
895:
892:
889:
886:
883:
880:
877:
874:
871:
868:
865:
862:
859:
856:
853:
850:
847:
844:
841:
838:
835:
832:
829:
826:
823:
820:
817:
814:
811:
808:
805:
802:
799:
796:
793:
790:
787:
784:
781:
778:
775:
772:
769:
766:
763:
760:
757:
754:
751:
748:
745:
742:
739:
736:
733:
730:
727:
724:
721:
718:
715:
712:
709:
706:
703:
700:
697:
694:
691:
688:
685:
682:
679:
676:
673:
670:
667:
664:
661:
658:
655:
652:
649:
646:
643:
640:
637:
634:
631:
628:
625:
622:
619:
616:
613:
610:
607:
604:
601:
598:
595:
592:
589:
586:
583:
580:
577:
574:
571:
568:
565:
562:
559:
556:
553:
550:
547:
544:
541:
538:
535:
532:
529:
526:
523:
520:
517:
514:
511:
508:
505:
502:
499:
496:
493:
490:
487:
484:
481:
478:
475:
472:
469:
466:
463:
460:
457:
454:
451:
448:
445:
442:
439:
436:
433:
430:
427:
424:
421:
418:
415:
412:
409:
406:
403:
400:
397:
394:
391:
388:
385:
382:
379:
376:
373:
370:
367:
364:
361:
358:
355:
352:
349:
346:
343:
340:
337:
334:
331:
328:
325:
322:
319:
316:
313:
310:
307:
304:
301:
298:
295:
281:
279:Implementations
122:First published
98:
77:
66:
60:
57:
47:Please help to
46:
30:
26:
17:
12:
11:
5:
2889:
2879:
2878:
2873:
2868:
2863:
2858:
2853:
2836:
2835:
2832:
2831:
2829:
2828:
2817:
2814:
2813:
2811:
2810:
2805:
2803:Random numbers
2800:
2795:
2790:
2785:
2780:
2775:
2770:
2765:
2760:
2755:
2749:
2747:
2743:
2742:
2740:
2739:
2734:
2729:
2727:Garlic routing
2724:
2719:
2714:
2709:
2704:
2699:
2694:
2689:
2684:
2679:
2674:
2669:
2664:
2659:
2654:
2649:
2647:Secure channel
2644:
2638:
2637:
2636:
2625:
2620:
2615:
2610:
2608:Key stretching
2605:
2600:
2595:
2590:
2585:
2580:
2575:
2574:
2573:
2568:
2558:
2556:Cryptovirology
2553:
2548:
2543:
2541:Cryptocurrency
2538:
2533:
2528:
2527:
2526:
2516:
2511:
2505:
2503:
2499:
2498:
2491:
2490:
2483:
2476:
2468:
2461:
2460:
2457:
2456:
2453:
2452:
2450:
2449:
2444:
2439:
2433:
2431:
2427:
2426:
2424:
2423:
2418:
2413:
2408:
2403:
2397:
2395:
2391:
2390:
2388:
2387:
2382:
2377:
2372:
2367:
2362:
2357:
2352:
2347:
2342:
2337:
2332:
2331:
2330:
2325:
2320:
2315:
2310:
2300:
2295:
2290:
2285:
2277:
2272:
2267:
2260:Distinguishing
2257:
2252:
2251:
2250:
2245:
2240:
2230:
2220:
2219:
2218:
2213:
2203:
2192:
2190:
2180:
2179:
2177:
2176:
2166:
2161:
2156:
2151:
2146:
2141:
2136:
2131:
2126:
2124:Product cipher
2121:
2116:
2111:
2105:
2103:
2099:
2098:
2096:
2095:
2090:
2085:
2080:
2075:
2070:
2065:
2060:
2055:
2050:
2045:
2040:
2035:
2030:
2025:
2020:
2015:
2010:
2005:
2000:
1995:
1990:
1985:
1980:
1975:
1970:
1965:
1960:
1955:
1950:
1945:
1940:
1935:
1930:
1925:
1920:
1915:
1910:
1905:
1900:
1895:
1890:
1879:
1874:
1869:
1864:
1859:
1854:
1849:
1844:
1839:
1834:
1829:
1824:
1819:
1814:
1809:
1804:
1799:
1794:
1789:
1784:
1779:
1774:
1769:
1764:
1759:
1754:
1752:Cryptomeria/C2
1749:
1744:
1739:
1734:
1729:
1724:
1719:
1714:
1709:
1704:
1699:
1694:
1689:
1684:
1679:
1674:
1669:
1664:
1659:
1653:
1651:
1645:
1644:
1642:
1641:
1636:
1631:
1626:
1621:
1616:
1611:
1606:
1601:
1596:
1591:
1586:
1580:
1578:
1572:
1571:
1569:
1568:
1563:
1558:
1553:
1539:
1534:
1528:
1526:
1520:
1519:
1507:
1506:
1499:
1492:
1484:
1470:
1469:
1464:
1452:
1447:
1442:
1437:
1432:
1427:
1415:
1410:
1398:
1393:
1388:
1383:
1376:
1375:External links
1373:
1372:
1371:
1349:
1336:
1311:
1298:
1267:
1264:
1262:
1261:
1235:
1192:
1185:
1159:
1145:
1110:
1097:Tea extensions
1085:
1083:
1080:
1079:
1078:
1072:
1066:
1054:
1051:
1034:
1031:
1001:
998:
993:
992:
985:
978:
294:
283:This standard
280:
277:
261:Feistel cipher
209:
208:
200:
199:
192:
191:
188:
182:
181:
179:Feistel cipher
176:
172:
171:
168:
162:
161:
158:
152:
151:
147:
146:
141:
137:
136:
131:
127:
126:
123:
119:
118:
109:
105:
104:
100:
99:
96:
79:
78:
61:September 2015
33:
31:
24:
15:
9:
6:
4:
3:
2:
2888:
2877:
2874:
2872:
2869:
2867:
2864:
2862:
2859:
2857:
2854:
2852:
2851:Block ciphers
2849:
2848:
2846:
2827:
2819:
2818:
2815:
2809:
2808:Steganography
2806:
2804:
2801:
2799:
2796:
2794:
2791:
2789:
2786:
2784:
2781:
2779:
2776:
2774:
2771:
2769:
2766:
2764:
2763:Stream cipher
2761:
2759:
2756:
2754:
2751:
2750:
2748:
2744:
2738:
2735:
2733:
2730:
2728:
2725:
2723:
2722:Onion routing
2720:
2718:
2715:
2713:
2710:
2708:
2705:
2703:
2702:Shared secret
2700:
2698:
2695:
2693:
2690:
2688:
2685:
2683:
2680:
2678:
2675:
2673:
2670:
2668:
2665:
2663:
2660:
2658:
2655:
2653:
2650:
2648:
2645:
2642:
2639:
2634:
2631:
2630:
2629:
2626:
2624:
2621:
2619:
2616:
2614:
2611:
2609:
2606:
2604:
2601:
2599:
2598:Key generator
2596:
2594:
2591:
2589:
2586:
2584:
2581:
2579:
2576:
2572:
2569:
2567:
2564:
2563:
2562:
2561:Hash function
2559:
2557:
2554:
2552:
2549:
2547:
2544:
2542:
2539:
2537:
2536:Cryptanalysis
2534:
2532:
2529:
2525:
2522:
2521:
2520:
2517:
2515:
2512:
2510:
2507:
2506:
2504:
2500:
2496:
2489:
2484:
2482:
2477:
2475:
2470:
2469:
2466:
2462:
2448:
2445:
2443:
2440:
2438:
2435:
2434:
2432:
2428:
2422:
2419:
2417:
2414:
2412:
2409:
2407:
2404:
2402:
2399:
2398:
2396:
2392:
2386:
2383:
2381:
2378:
2376:
2373:
2371:
2368:
2366:
2363:
2361:
2358:
2356:
2353:
2351:
2348:
2346:
2343:
2341:
2340:Interpolation
2338:
2336:
2333:
2329:
2326:
2324:
2321:
2319:
2316:
2314:
2311:
2309:
2306:
2305:
2304:
2301:
2299:
2296:
2294:
2291:
2289:
2286:
2284:
2283:
2278:
2276:
2273:
2271:
2268:
2265:
2261:
2258:
2256:
2253:
2249:
2246:
2244:
2241:
2239:
2236:
2235:
2234:
2231:
2228:
2224:
2221:
2217:
2214:
2212:
2209:
2208:
2207:
2204:
2201:
2197:
2194:
2193:
2191:
2188:
2187:cryptanalysis
2181:
2174:
2170:
2169:Key whitening
2167:
2165:
2162:
2160:
2157:
2155:
2152:
2150:
2147:
2145:
2142:
2140:
2137:
2135:
2132:
2130:
2127:
2125:
2122:
2120:
2117:
2115:
2112:
2110:
2107:
2106:
2104:
2100:
2094:
2091:
2089:
2086:
2084:
2081:
2079:
2076:
2074:
2071:
2069:
2066:
2064:
2061:
2059:
2056:
2054:
2051:
2049:
2046:
2044:
2041:
2039:
2036:
2034:
2031:
2029:
2026:
2024:
2021:
2019:
2016:
2014:
2011:
2009:
2006:
2004:
2001:
1999:
1996:
1994:
1991:
1989:
1986:
1984:
1981:
1979:
1976:
1974:
1971:
1969:
1966:
1964:
1961:
1959:
1958:New Data Seal
1956:
1954:
1951:
1949:
1946:
1944:
1941:
1939:
1936:
1934:
1931:
1929:
1926:
1924:
1921:
1919:
1916:
1914:
1911:
1909:
1906:
1904:
1901:
1899:
1896:
1894:
1891:
1888:
1884:
1880:
1878:
1875:
1873:
1870:
1868:
1865:
1863:
1860:
1858:
1855:
1853:
1850:
1848:
1845:
1843:
1840:
1838:
1835:
1833:
1830:
1828:
1825:
1823:
1820:
1818:
1815:
1813:
1810:
1808:
1805:
1803:
1800:
1798:
1795:
1793:
1790:
1788:
1785:
1783:
1780:
1778:
1775:
1773:
1770:
1768:
1765:
1763:
1760:
1758:
1755:
1753:
1750:
1748:
1745:
1743:
1740:
1738:
1735:
1733:
1730:
1728:
1725:
1723:
1720:
1718:
1715:
1713:
1710:
1708:
1705:
1703:
1700:
1698:
1697:BEAR and LION
1695:
1693:
1690:
1688:
1685:
1683:
1680:
1678:
1675:
1673:
1670:
1668:
1665:
1663:
1660:
1658:
1655:
1654:
1652:
1646:
1640:
1637:
1635:
1632:
1630:
1627:
1625:
1622:
1620:
1617:
1615:
1612:
1610:
1607:
1605:
1602:
1600:
1597:
1595:
1592:
1590:
1587:
1585:
1582:
1581:
1579:
1573:
1567:
1564:
1562:
1559:
1557:
1554:
1551:
1547:
1543:
1540:
1538:
1535:
1533:
1530:
1529:
1527:
1521:
1516:
1512:
1511:Block ciphers
1505:
1500:
1498:
1493:
1491:
1486:
1485:
1482:
1478:
1474:
1468:
1465:
1463:
1459:
1456:
1453:
1451:
1448:
1446:
1443:
1441:
1438:
1436:
1433:
1431:
1428:
1426:
1422:
1419:
1416:
1414:
1411:
1409:
1405:
1402:
1399:
1397:
1394:
1392:
1389:
1387:
1384:
1382:
1379:
1378:
1357:
1356:
1350:
1339:
1333:
1328:
1323:
1319:
1318:
1312:
1301:
1295:
1290:
1285:
1281:
1280:
1275:
1274:Preneel, Bart
1270:
1269:
1250:
1246:
1239:
1231:
1227:
1223:
1219:
1215:
1211:
1207:
1203:
1196:
1188:
1182:
1178:
1174:
1170:
1163:
1148:
1142:
1137:
1132:
1128:
1121:
1114:
1106:
1099:
1098:
1090:
1086:
1076:
1073:
1070:
1067:
1064:
1063:stream cipher
1060:
1057:
1056:
1050:
1048:
1044:
1040:
1030:
1026:
1024:
1020:
1016:
1013:
1007:
1006:cryptanalysis
1000:Cryptanalysis
997:
986:
979:
972:
967:unsigned long
964:
963:
962:
292:
290:
289:public domain
286:
276:
274:
270:
266:
262:
259:
254:
252:
248:
244:
243:Roger Needham
240:
239:David Wheeler
236:
232:
228:
224:
220:
216:
206:
201:
198:
197:cryptanalysis
193:
189:
187:
183:
180:
177:
173:
169:
167:
163:
159:
157:
153:
150:Cipher detail
148:
145:
142:
138:
135:
132:
128:
124:
120:
117:
116:David Wheeler
113:
112:Roger Needham
110:
106:
101:
92:
87:
75:
72:
64:
54:
50:
44:
43:
37:
32:
23:
22:
19:
2866:Free ciphers
2758:Block cipher
2603:Key schedule
2593:Key exchange
2583:Kleptography
2546:Cryptosystem
2495:Cryptography
2345:Partitioning
2303:Side-channel
2281:
2248:Higher-order
2233:Differential
2114:Key schedule
1638:
1363:. Retrieved
1354:
1341:. Retrieved
1316:
1303:. Retrieved
1278:
1252:. Retrieved
1249:ResearchGate
1248:
1238:
1205:
1201:
1195:
1168:
1162:
1150:. Retrieved
1126:
1113:
1104:
1096:
1089:
1038:
1036:
1027:
1009:
994:
960:
282:
269:key-schedule
258:64-bit block
255:
227:block cipher
223:eXtended TEA
222:
218:
215:cryptography
212:
195:Best public
130:Derived from
67:
58:
39:
18:
16:Block cipher
2746:Mathematics
2737:Mix network
2430:Utilization
2416:NSA Suite B
2401:AES process
2350:Rubber-hose
2288:Related-key
2196:Brute-force
1575:Less common
1365:October 10,
1343:October 10,
1305:October 10,
1254:October 10,
1208:(1): 1–11.
1152:October 10,
1012:related-key
265:128-bit key
205:related-key
166:Block sizes
53:introducing
2845:Categories
2697:Ciphertext
2667:Decryption
2662:Encryption
2623:Ransomware
2380:Chi-square
2298:Rotational
2238:Impossible
2159:Block size
2053:Spectr-H64
1877:Ladder-DES
1872:Kuznyechik
1817:Hierocrypt
1687:BassOmatic
1650:algorithms
1577:algorithms
1550:Triple DES
1525:algorithms
1082:References
1004:See also:
767:num_rounds
737:num_rounds
719:0x9E3779B9
644:num_rounds
437:num_rounds
407:0x9E3779B9
320:num_rounds
140:Successors
36:references
2687:Plaintext
2355:Black-bag
2275:Boomerang
2264:Known-key
2243:Truncated
2068:Threefish
2063:SXAL/MBAL
1953:MultiSwap
1908:MacGuffin
1867:KN-Cipher
1807:Grand Cru
1762:CS-Cipher
1742:COCONUT98
1222:1615-5262
1039:Block TEA
1033:Block TEA
175:Structure
156:Key sizes
108:Designers
2826:Category
2732:Kademlia
2692:Codetext
2635:(CSPRNG)
2406:CRYPTREC
2370:Weak key
2323:Acoustic
2164:Key size
2008:Red Pike
1827:IDEA NXT
1707:Chiasmus
1702:CAST-256
1682:BaseKing
1667:Akelarre
1662:Adiantum
1629:Skipjack
1594:CAST-128
1589:Camellia
1537:Blowfish
1458:Archived
1421:Archived
1404:Archived
1230:26794956
1053:See also
975:uint32_t
893:>>
875:<<
815:>>
797:<<
686:uint32_t
674:unsigned
659:uint32_t
650:uint32_t
638:unsigned
632:decipher
563:>>
545:<<
485:>>
467:<<
362:uint32_t
350:unsigned
335:uint32_t
326:uint32_t
314:unsigned
308:encipher
296:#include
160:128 bits
2502:General
2447:Padding
2365:Rebound
2073:Treyfer
2023:SAVILLE
1983:PRESENT
1973:NOEKEON
1918:MAGENTA
1913:Madryga
1893:Lucifer
1757:CRYPTON
1566:Twofish
1556:Serpent
263:with a
251:patents
245:of the
225:) is a
170:64 bits
103:General
49:improve
2613:Keygen
2411:NESSIE
2360:Davies
2308:Timing
2223:Linear
2183:Attack
2102:Design
2093:Zodiac
2058:Square
2033:SHACAL
2028:SC2000
1988:Prince
1968:Nimbus
1963:NewDES
1948:MULTI2
1938:MISTY1
1881:LOKI (
1857:KHAZAD
1852:KeeLoq
1847:KASUMI
1842:Kalyna
1727:CLEFIA
1712:CIKS-1
1672:Anubis
1523:Common
1334:
1296:
1228:
1220:
1183:
1143:
1025:of 2.
1021:and a
984:types.
973:clean
971:64-bit
235:cipher
233:. The
186:Rounds
38:, but
2643:(PRN)
2293:Slide
2149:Round
2134:P-box
2129:S-box
2088:XXTEA
2048:Speck
2043:Simon
2038:SHARK
2018:SAFER
2003:REDOC
1928:Mercy
1887:89/91
1837:Iraqi
1802:G-DES
1792:FEA-M
1772:DES-X
1737:Cobra
1692:BATON
1677:Ascon
1657:3-Way
1648:Other
1359:(PDF)
1226:S2CID
1123:(PDF)
1101:(PDF)
1069:XXTEA
1047:XXTEA
982:const
857:delta
731:delta
713:delta
662:const
527:delta
401:delta
338:const
2421:CNSA
2280:Mod
2206:MITM
1978:NUSH
1933:MESH
1923:MARS
1797:FROG
1787:FEAL
1767:DEAL
1747:Crab
1732:CMEA
1639:XTEA
1624:SEED
1604:IDEA
1599:GOST
1584:ARIA
1367:2018
1345:2018
1332:ISBN
1307:2018
1294:ISBN
1256:2018
1218:ISSN
1181:ISBN
1154:2018
1141:ISBN
1061:— A
764:<
629:void
434:<
305:void
273:XORs
241:and
219:XTEA
125:1997
84:XTEA
2375:Tau
2335:XSL
2139:SPN
2083:xmx
2078:UES
2013:S-1
1998:RC2
1943:MMB
1822:ICE
1777:DFC
1634:TEA
1619:RC6
1614:RC5
1609:LEA
1561:SM4
1542:DES
1532:AES
1322:doi
1284:doi
1210:doi
1173:doi
1131:doi
1075:TEA
1059:RC4
923:key
917:sum
869:(((
851:sum
845:key
839:sum
791:(((
743:for
725:sum
677:int
665:key
641:int
593:key
587:sum
539:(((
521:sum
515:key
509:sum
461:(((
413:for
389:sum
353:int
341:key
317:int
231:TEA
213:In
134:TEA
2847::
1903:M8
1898:M6
1885:,
1883:97
1782:E2
1548:,
1330:.
1292:.
1247:.
1224:.
1216:.
1204:.
1179:.
1139:.
1103:.
1049:.
950:v1
938:v0
926:);
905:v1
899:))
890:v1
872:v1
866:-=
863:v0
854:-=
848:);
827:v0
821:))
812:v0
794:v0
788:-=
785:v1
776:++
701:v1
689:v0
620:v1
608:v0
596:);
575:v0
569:))
560:v0
542:v0
536:+=
533:v1
524:+=
518:);
497:v1
491:))
482:v1
464:v1
458:+=
455:v0
446:++
377:v1
365:v0
253:.
217:,
203:A
114:,
2487:e
2480:t
2473:v
2282:n
2266:)
2262:(
2229:)
2225:(
2202:)
2198:(
2189:)
2185:(
2175:)
2171:(
1993:Q
1889:)
1552:)
1544:(
1517:)
1513:(
1503:e
1496:t
1489:v
1369:.
1347:.
1324::
1309:.
1286::
1258:.
1232:.
1212::
1206:8
1189:.
1175::
1156:.
1133::
991:;
977:.
956:}
953:;
947:=
944:v
941:;
935:=
932:v
929:}
920:+
914:(
911:^
908:)
902:+
896:5
887:(
884:^
881:)
878:4
860:;
842:+
836:(
833:^
830:)
824:+
818:5
809:(
806:^
803:)
800:4
782:{
779:)
773:i
770:;
761:i
758:;
755:0
752:=
749:i
746:(
740:;
734:*
728:=
722:,
716:=
710:,
707:v
704:=
698:,
695:v
692:=
683:;
680:i
671:{
668:)
656:,
653:v
647:,
635:(
626:}
623:;
617:=
614:v
611:;
605:=
602:v
599:}
590:+
584:(
581:^
578:)
572:+
566:5
557:(
554:^
551:)
548:4
530:;
512:+
506:(
503:^
500:)
494:+
488:5
479:(
476:^
473:)
470:4
452:{
449:)
443:i
440:;
431:i
428:;
425:0
422:=
419:i
416:(
410:;
404:=
398:,
395:0
392:=
386:,
383:v
380:=
374:,
371:v
368:=
359:;
356:i
347:{
344:)
332:,
329:v
323:,
311:(
285:C
221:(
74:)
68:(
63:)
59:(
45:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.