36:
199:
239:
27:
219:
337:
326:
269:
736:
Sniffer customers could write their own protocol interpreters to decode new or rare protocols not supported by
Network General. Interpreters were written in C and linked with the rest of the Sniffer modules to create a new executable program. The procedure for creating new PIs was documented in April
126:
of
Mountain View, CA. By 1994 the Sniffer had become the market leader in high-end protocol analyzers. According to SEC 10-K filings and corporate annual reports, between 1986 and March 1997 about $ 933M worth of Sniffers and related products and services had been sold as tools for network managers
162:
promiscuous packet receiver and analyzer called TART (“Transmit and
Receive Totaliser”) for use as an internal engineering test tool. It used custom hardware, and software for an IBM PC written in a combination of BASIC and 8086 assembly code. When Nestar was acquired by Digital Switch Corporation
732:
Decoding higher protocol levels often required the interpreter to maintain state information about connections so that subsequent packets could be property interpreted. That was implemented with a combination of locally cached data within the protocol interpreter, and the ability to look back at
214:
There was no promiscuous mode in the SMC chip that would allow all packets to be received regardless of the destination address. So to create the
Sniffer, a daughterboard was developed that intercepted the receive data line to the chip and manipulated the data so that every packet looked like a
321:
for their file browser. As the
Sniffer manual described, “The screen shows you three panels, arranged from left to right. Immediately to the left of your current (highlighted) position is the node you just came from. Above and below you in the center panel are alternative nodes that are also
185:, and customers were given the ability to write their own interpreters. The product line gradually expanded to include the Distributed Sniffer System for multiple remote network segments, the Expert Sniffer for advanced problem diagnosis, and the Watchdog for simple network monitoring.
344:
When capture ended, packets were analyzed and displayed in one or more of the now-standard three synchronized vertical windows: multiple packet summary, single packet decoded detail, and raw numerical packet data. Highlighting linked the selected items in each window.
352:
The translation of data at a particular level of the network protocol stack into user-friendly text was the job of a “protocol interpreter”, or PI. Network
General provided over 100 PI’s for commonly-used protocols of the day:
206:
The ARCNET Sniffer developed as an internal test tool by Zynar used the IBM PC ARCNET Network
Interface Card developed by Nestar for the PLAN networking systems. That board used the COM9026 integrated ARCNET controller from
265:“luggable” computer that had an Intel 80286 processor, 640 KB of RAM, a 20 MB internal hard disk, a 5 ¼” floppy disk drive, and a 9” monochrome CRT screen. The retail price of the Sniffer in unit quantities was $ 19,995.
158:, a personal computer networking company founded in October 1978 by Saal and Shustek along with Jim Hinds and Nick Fortis. In 1982 engineers John Rowlands and Chris Reed at Nestar’s UK subsidiary Zynar Ltd developed an
226:
Since the ability to receive all packets was viewed as a violation of network privacy, the circuitry implementing it was kept secret, and the daughterboard was potted in black epoxy to discourage reverse-engineering.
348:
In the multiple-packet summary, the default display was of information at the highest level of the protocol stack present in that packet. Other displays could be requested using the “display options” menu.
250:
packet receiver, which means it received a copy of all network packets without regard to what computer they were addressed to. The packets were filtered, analyzed using what is now sometimes called
170:
network hardware, created a different user interface with software written in C, and began selling it as The
Sniffer™ in December 1986. The company had four employees at the end of that year.
740:
In addition to supporting many network protocols, there were versions of the
Sniffer that collected data from the major local area networks in use in the 1980s and early 1990s:
813:
Even in the early years, the
Sniffer had competition, at least for some aspects of the product. Several were, like the Sniffer, ready-to-use packaged instruments:
261:
operating system, and used a 40 line 80-character text-only display. The first version, the PA-400 protocol analyzer for Token-Ring networks, was released on a
1481:
166:
At Network General, Saal and Shustek initially sold TART as the “R-4903 ARCNET Line Analyzer (‘The Sniffer’)”. They then reengineered TART for IBM’s
836:
There were also several software-only packet monitors and decoders, often running on Unix, and often with only a command-line user interface:
154:
to develop and market network protocol analyzers. The inspiration was an internal test tool that had been developed within
35:
130:
The Sniffer was the antecedent of several generations of network protocol analyzers, of which the current most popular is
1419:
1366:
1130:
774:
1575:
208:
1165:
26:
769:
104:
1342:"1991 04 The Network Is Your Business : Network General Corp. : Free Download, Borrow, and Streaming"
1149:
863:
289:
triggers control when capture should stop, perhaps because a sought-after network error condition had occurred
1317:
784:
173:
In April 1987 the company released an Ethernet version of the Sniffer, and in October, versions for ARCNET,
996:
978:
960:
1258:
1619:
1181:
790:
181:
Broadband. Protocol interpreters were written for about 100 network protocols at various levels of the
889:
322:
reachable from the node to your left… To your right are nodes reachable from the node you're now on.”
1292:
1464:
1602:
1341:
1206:
1037:
946:
1402:
309:
Navigation of the extensive menu system on the character-mode display was through a variation of
230:
The source code of the original TART/Sniffer BASIC and assembler program is available on GitHub.
1014:
163:(now DSC Communications) of Plano, Texas in 1986, Saal and Shustek received the rights to TART.
844:
251:
198:
1594:
1516:
1383:
1240:
1221:
1112:
1029:
938:
914:"May 13: Network General Corporation Founded | This Day in History | Computer History Museum"
1318:"1987 03 16 Network General Price List End User : Free Download, Borrow, and Streaming"
1198:
238:
8:
1537:"The Ancient History of Computers and Network Sniffers" (Sharkfest 2021 keynote talk) -
1581:
262:
1571:
1093:
747:
1293:"1986 12 Network General Large Brochure : Free Download, Borrow, and Streaming"
1563:
1085:
247:
218:
94:
1585:
1499:
1439:
336:
143:
123:
119:
71:
1523:. Vol. 15, no. 19. InfoWorld Media Group, Inc. 1993-05-10. p. 85.
1073:
913:
801:
314:
310:
182:
178:
155:
1539:
1273:
1051:
1613:
1555:
1097:
1567:
851:
325:
1500:"The BSD Packet Filter: A New Architecture for User-level Packet Capture"
1089:
779:
151:
56:
823:
Communications Machinery Corporation's DRN-1700 LanScan Ethernet Monitor
167:
147:
66:
51:
43:
1560:
Proceedings [1988] 13th Conference on Local Computer Networks
868:
761:
318:
131:
1390:. Vol. 11, no. 6. InfoWorld Media Group, Inc. p. S14.
1247:. Vol. 12, no. 35. InfoWorld Media Group, Inc. p. 54.
1228:. Vol. 14, no. 39. InfoWorld Media Group, Inc. p. 45.
333:
Pressing F10 initiated capture and a real-time display of activity.
268:
1384:"LAN Analyzers: Powerful Tools Useful For Serious Network Analysis"
1119:. Vol. 8, no. 48. InfoWorld Media Group, Inc. p. 25.
840:
817:
174:
1277:
258:
159:
1113:"Nestar Says Firm's Acquisition To Improve LAN and PBX Links"
847:
and other capture mechanisms provided by the operating system
1015:"Network General Corp. annual reports 1989-1993, 1995, 1997"
211:, which had been developed in collaboration with Datapoint.
1368:
Network General Token Ring Sniffer V 1.20 Addendum Apr 1987
1132:
Network General R 4903 ARCNET Line Analyzer Manual Sep 1986
796:
303:
options control which aspects of the packets are displayed
1167:
Network General Ethernet Sniffer Introduction Apr 1987
283:
packets are captured, stored, counted, and summarized
1595:"LAN management: What's the right tool for the job?"
1199:"Sniffer Gains Distributed Management Capabilities"
1053:"Presenting Network General Corporation", July 1992
829:
Digital Equipment Corporation's LAN Traffic Monitor
1151:Network General Token Ring Sniffer V 1.0 Dec 1986
222:IBM PC ARCNET Sniffer daughterboard potted module
1611:
1241:"The Watchdog Sniffs Out LAN Traffic Statistics"
826:Hewlett-Packard's HP-4972A LAN Protocol Analyzer
1437:
1400:
1074:"Distributing computing at the personal level"
733:earlier packets stored in the capture buffer.
257:The Sniffer was implemented above Microsoft’s
1154:. Network General Corporation. December 1986.
1030:"Network General smells success with Sniffer"
340:Example sniffer screen during packet capture
1465:"Understanding and Using Computer Networks"
1421:LANalyzer EX5000E Ethernet Network Analyzer
1260:Nestar ARCNET Sniffer Internal Descriptions
300:filters control which packets are displayed
820:'s 1984 Nutcracker, and its 1986 LANalyzer
286:filters control which packets are captured
233:
1183:Network General Ethernet Sniffer Jun 1988
936:
215:broadcast and was received by the chip.
1592:
1553:
1401:Satyanarayanan, M (September 22, 1984).
1027:
335:
324:
267:
237:
217:
197:
193:
1403:"The Excelan Nutcracker: An Evaluation"
1196:
997:"Network General Corporation FY97 10-K"
979:"Network General Corporation FY96 10-K"
961:"Network General Corporation FY95 10-K"
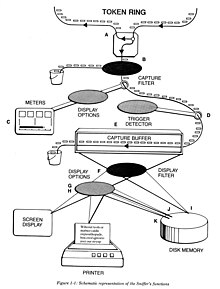
276:The two major modes of operation were:
1612:
1497:
1072:Prins, G.A. (November–December 1979).
737:1987 as part of Sniffer version 1.20.
1556:"Benchmarking LAN protocol analyzers"
1482:"Quick and Accurate LAN Measurements"
1381:
1287:
1285:
1219:
1144:
1142:
1110:
1071:
939:"Merger will hone net analysis focus"
142:The Sniffer was the first product of
1498:McCann, Steven (December 19, 1992).
1238:
887:
752:Ethernet (thick, thin, twisted pair)
297:packets are analyzed and interpreted
254:, and stored for later examination.
122:developed and first sold in 1986 by
120:network packet and protocol analyzer
16:Network packet and protocol analyzer
13:
1462:
1282:
1232:
1139:
14:
1631:
1531:
1222:"Expert Sniffer to Diagnose WANs"
1007:
832:Tektronix's TMA802 Media Analyzer
209:Standard Microsystems Corporation
1554:Haugdahl, J. S. (October 1988).
313:that were originally created by
34:
25:
1593:Chartoff, Marvin (1987-12-14).
1509:
1491:
1474:
1456:
1431:
1412:
1394:
1375:
1359:
1334:
1310:
1267:
1251:
1213:
1190:
1174:
1158:
1123:
1104:
1065:
937:Musthaler, Linda (1994-02-21).
1371:. Network General. 1987-04-01.
1186:. Network General. 1988-06-01.
1170:. Network General. 1987-04-01.
1135:. Network General. 1986-09-25.
1044:
1021:
989:
971:
953:
930:
906:
881:
864:Comparison of packet analyzers
808:
188:
1:
1220:Busse, Torsten (1992-09-28).
1028:Petrosky, Mary (1987-06-22).
1017:– via Internet Archive.
874:
785:Synchronous Data Link Control
146:, founded on May 13, 1986 by
137:
1601:. Vol. 4, no. 50.
1274:NestarSystems/ARCNET_Sniffer
1263:. Nestar Systems. 1982–1984.
1205:. Vol. 8, no. 13.
1197:Smalley, Eric (1991-04-01).
1111:Flynn, Laurie (1986-11-24).
1036:. Vol. 4, no. 25.
945:. Vol. 11, no. 8.
7:
1382:Glass, Brett (1989-02-06).
857:
202:IBM PC ARCNET Sniffer board
144:Network General Corporation
124:Network General Corporation
10:
1636:
1541:SF16 - Len Shustek Keynote
1239:Taft, Peter (1990-08-27).
850:LANWatch, originally from
791:Asynchronous Transfer Mode
1440:"4972A Protocol Analyzer"
888:Joch, Alan (2001-07-23).
103:
93:
85:
77:
65:
42:
33:
24:
1603:International Data Group
1207:International Data Group
1038:International Data Group
947:International Data Group
242:Token-Ring Sniffer, 1986
234:Network General Sniffer
918:www.computerhistory.org
628:PUP address translation
439:Banyan VINES StreetTalk
430:Banyan VINES Matchmaker
329:Sniffer menu navigation
1568:10.1109/LCN.1988.10251
1517:"LANWatch Version 3.0"
845:Berkeley Packet Filter
341:
330:
273:
252:Deep Packet Inspection
243:
223:
203:
194:Nestar ARCNET Sniffer
1078:Electronics and Power
433:Banyan VINES Ntwk Mgr
427:Banyan VINES Loopback
412:Banyan VINES File Svc
339:
328:
319:Datapoint Corporation
271:
241:
221:
201:
1562:. pp. 375–384.
1438:HP Computer Museum.
1090:10.1049/ep.1979.0422
688:Vitalink bridge mgmt
457:Bridge terminal srvr
442:Banyan VINES Svr Svc
294:“display”, in which
280:“capture”, in which
1470:. p. 3-26.
21:
1001:SEC Edgar database
983:SEC Edgar database
965:SEC Edgar database
890:"Network Sniffers"
451:Bridge bridge mgmt
342:
331:
274:
263:Compaq Portable II
246:The Sniffer was a
244:
224:
204:
44:Original author(s)
19:
1620:Network analyzers
661:Symbolics private
616:Nestar PlanSeries
445:Banyan VINES Talk
409:Banyan VINES Echo
406:Banyan VINES AFRP
272:Sniffer data flow
113:
112:
109:protocol analyzer
89:C, 8086 assembler
1627:
1606:
1589:
1550:
1549:
1548:
1525:
1524:
1513:
1507:
1506:
1504:
1495:
1489:
1488:
1486:
1478:
1472:
1471:
1469:
1460:
1454:
1453:
1451:
1450:
1444:www.hpmuseum.net
1435:
1429:
1428:
1427:. Excelan. 1986.
1426:
1416:
1410:
1409:
1407:
1398:
1392:
1391:
1379:
1373:
1372:
1363:
1357:
1356:
1354:
1353:
1346:Internet Archive
1338:
1332:
1331:
1329:
1328:
1322:Internet Archive
1314:
1308:
1307:
1305:
1304:
1297:Internet Archive
1289:
1280:
1271:
1265:
1264:
1255:
1249:
1248:
1236:
1230:
1229:
1217:
1211:
1210:
1194:
1188:
1187:
1178:
1172:
1171:
1162:
1156:
1155:
1146:
1137:
1136:
1127:
1121:
1120:
1108:
1102:
1101:
1069:
1063:
1062:
1061:
1060:
1048:
1042:
1041:
1025:
1019:
1018:
1011:
1005:
1004:
1003:. June 27, 1997.
993:
987:
986:
985:. July 25, 1996.
975:
969:
968:
967:. June 28, 1995.
957:
951:
950:
934:
928:
927:
925:
924:
910:
904:
903:
901:
900:
885:
755:Datapoint ARCnet
436:Banyan VINES SPP
424:Banyan VINES LLC
418:Banyan VINES FTP
415:Banyan VINES FRP
248:promiscuous mode
127:and developers.
95:Operating system
38:
29:
22:
18:
1635:
1634:
1630:
1629:
1628:
1626:
1625:
1624:
1610:
1609:
1578:
1546:
1544:
1538:
1534:
1529:
1528:
1515:
1514:
1510:
1502:
1496:
1492:
1484:
1480:
1479:
1475:
1467:
1461:
1457:
1448:
1446:
1436:
1432:
1424:
1418:
1417:
1413:
1405:
1399:
1395:
1380:
1376:
1365:
1364:
1360:
1351:
1349:
1340:
1339:
1335:
1326:
1324:
1316:
1315:
1311:
1302:
1300:
1299:. December 1986
1291:
1290:
1283:
1272:
1268:
1257:
1256:
1252:
1237:
1233:
1218:
1214:
1195:
1191:
1180:
1179:
1175:
1164:
1163:
1159:
1148:
1147:
1140:
1129:
1128:
1124:
1109:
1105:
1070:
1066:
1058:
1056:
1050:
1049:
1045:
1026:
1022:
1013:
1012:
1008:
995:
994:
990:
977:
976:
972:
959:
958:
954:
935:
931:
922:
920:
912:
911:
907:
898:
896:
886:
882:
877:
860:
811:
730:
568:IONET VCS TRANS
490:DEC LAN monitor
487:DEC bridge mgmt
421:Banyan VINES IP
236:
196:
191:
140:
118:was a computer
78:Initial release
72:Network General
61:
17:
12:
11:
5:
1633:
1623:
1622:
1608:
1607:
1590:
1576:
1551:
1533:
1532:External links
1530:
1527:
1526:
1508:
1490:
1473:
1463:Pabrai, Uday.
1455:
1430:
1411:
1393:
1374:
1358:
1333:
1309:
1281:
1266:
1250:
1231:
1212:
1189:
1173:
1157:
1138:
1122:
1103:
1064:
1043:
1020:
1006:
988:
970:
952:
929:
905:
879:
878:
876:
873:
872:
871:
866:
859:
856:
855:
854:
848:
834:
833:
830:
827:
824:
821:
810:
807:
806:
805:
802:IBM PC Network
799:
794:
788:
782:
777:
772:
767:
766:Corvus Omninet
764:
759:
756:
753:
750:
745:
744:IBM Token-Ring
729:
728:
725:
722:
719:
716:
713:
710:
707:
704:
701:
698:
695:
692:
689:
686:
683:
680:
677:
674:
671:
668:
665:
662:
659:
656:
653:
650:
647:
644:
641:
638:
635:
632:
629:
626:
625:Novell Netware
623:
620:
617:
614:
611:
608:
605:
602:
599:
596:
593:
590:
587:
584:
581:
578:
575:
572:
569:
566:
565:IONET VCS DATA
563:
562:IONET VCS CMND
560:
557:
554:
551:
548:
545:
542:
539:
536:
533:
530:
527:
524:
521:
518:
515:
512:
509:
506:
503:
500:
497:
494:
491:
488:
485:
482:
479:
476:
473:
470:
467:
464:
461:
458:
455:
452:
449:
446:
443:
440:
437:
434:
431:
428:
425:
422:
419:
416:
413:
410:
407:
404:
401:
398:
395:
394:AppleTalk RTMP
392:
389:
386:
383:
380:
379:AppleTalk ECHO
377:
374:
371:
368:
365:
362:
361:AppleTalk ADSP
359:
355:
311:Miller Columns
307:
306:
305:
304:
301:
298:
292:
291:
290:
287:
284:
235:
232:
195:
192:
190:
187:
183:protocol stack
179:IBM PC Network
156:Nestar Systems
139:
136:
111:
110:
107:
101:
100:
97:
91:
90:
87:
83:
82:
79:
75:
74:
69:
63:
62:
60:
59:
54:
48:
46:
40:
39:
31:
30:
15:
9:
6:
4:
3:
2:
1632:
1621:
1618:
1617:
1615:
1605:. p. 37.
1604:
1600:
1599:Network World
1596:
1591:
1587:
1583:
1579:
1577:0-8186-0891-9
1573:
1569:
1565:
1561:
1557:
1552:
1543:
1542:
1536:
1535:
1522:
1518:
1512:
1501:
1494:
1483:
1477:
1466:
1459:
1445:
1441:
1434:
1423:
1422:
1415:
1404:
1397:
1389:
1385:
1378:
1370:
1369:
1362:
1347:
1343:
1337:
1323:
1319:
1313:
1298:
1294:
1288:
1286:
1279:
1275:
1270:
1262:
1261:
1254:
1246:
1242:
1235:
1227:
1223:
1216:
1208:
1204:
1203:Network World
1200:
1193:
1185:
1184:
1177:
1169:
1168:
1161:
1153:
1152:
1145:
1143:
1134:
1133:
1126:
1118:
1114:
1107:
1099:
1095:
1091:
1087:
1083:
1079:
1075:
1068:
1055:
1054:
1047:
1040:. p. 15.
1039:
1035:
1034:Network World
1031:
1024:
1016:
1010:
1002:
998:
992:
984:
980:
974:
966:
962:
956:
949:. p. 35.
948:
944:
943:Network World
940:
933:
919:
915:
909:
895:
894:Computerworld
891:
884:
880:
870:
867:
865:
862:
861:
853:
849:
846:
842:
839:
838:
837:
831:
828:
825:
822:
819:
816:
815:
814:
803:
800:
798:
795:
792:
789:
786:
783:
781:
778:
776:
773:
771:
768:
765:
763:
760:
757:
754:
751:
749:
746:
743:
742:
741:
738:
734:
726:
723:
720:
717:
715:Xerox PUP ARP
714:
711:
708:
705:
702:
699:
697:X.75 internet
696:
693:
690:
687:
684:
681:
678:
675:
672:
669:
666:
663:
660:
657:
654:
651:
648:
645:
642:
639:
636:
633:
630:
627:
624:
621:
618:
615:
613:Nestar ARCnet
612:
609:
606:
603:
600:
598:ISO Transport
597:
594:
591:
588:
585:
582:
579:
576:
573:
570:
567:
564:
561:
558:
555:
552:
549:
546:
543:
540:
537:
535:ECMA internet
534:
531:
528:
525:
522:
519:
516:
513:
510:
507:
504:
501:
498:
495:
492:
489:
486:
483:
481:Datapoint RMS
480:
478:Datapoint RIO
477:
475:Datapoint RCL
474:
472:Datapoint DLL
471:
468:
466:Cronus direct
465:
462:
459:
456:
453:
450:
447:
444:
441:
438:
435:
432:
429:
426:
423:
420:
417:
414:
411:
408:
405:
402:
399:
397:AppleTalk ZIP
396:
393:
391:AppleTalk PAP
390:
388:AppleTalk NBP
387:
385:AppleTalk LAP
384:
382:AppleTalk KSP
381:
378:
376:AppleTalk DDP
375:
373:AppleTalk ATP
372:
370:AppleTalk ASP
369:
367:AppleTalk ARP
366:
364:AppleTalk AFP
363:
360:
357:
356:
354:
350:
346:
338:
334:
327:
323:
320:
316:
315:Mark S Miller
312:
302:
299:
296:
295:
293:
288:
285:
282:
281:
279:
278:
277:
270:
266:
264:
260:
255:
253:
249:
240:
231:
228:
220:
216:
212:
210:
200:
186:
184:
180:
176:
171:
169:
164:
161:
157:
153:
149:
145:
135:
133:
128:
125:
121:
117:
108:
106:
102:
98:
96:
92:
88:
84:
81:December 1986
80:
76:
73:
70:
68:
64:
58:
55:
53:
50:
49:
47:
45:
41:
37:
32:
28:
23:
1598:
1559:
1545:, retrieved
1540:
1520:
1511:
1493:
1476:
1458:
1447:. Retrieved
1443:
1433:
1420:
1414:
1396:
1387:
1377:
1367:
1361:
1350:. Retrieved
1348:. April 1991
1345:
1336:
1325:. Retrieved
1321:
1312:
1301:. Retrieved
1296:
1269:
1259:
1253:
1244:
1234:
1225:
1215:
1209:. p. 4.
1202:
1192:
1182:
1176:
1166:
1160:
1150:
1131:
1125:
1116:
1106:
1081:
1077:
1067:
1057:, retrieved
1052:
1046:
1033:
1023:
1009:
1000:
991:
982:
973:
964:
955:
942:
932:
921:. Retrieved
917:
908:
897:. Retrieved
893:
883:
852:FTP Software
843:, using the
835:
812:
739:
735:
731:
694:X.25 level 3
610:NBS internet
511:DECNET FOUND
502:DECNET CTERM
351:
347:
343:
332:
308:
275:
256:
245:
229:
225:
213:
205:
172:
165:
141:
129:
115:
114:
67:Developer(s)
1084:(11): 765.
809:Competitors
780:Frame Relay
700:Xerox BOOTP
622:NetBIOS TCP
592:ISO Session
583:ISO Network
523:DECNET NICE
517:DECNET LAVC
499:DEC NetBIOS
454:Bridge CS-1
189:Development
152:Len Shustek
138:Background
116:The Sniffer
57:Len Shustek
1547:2021-08-17
1449:2021-02-18
1352:2021-06-04
1327:2021-06-03
1303:2021-06-03
1059:2021-11-17
923:2021-02-16
899:2021-02-16
875:References
721:Xerox TFTP
607:Micom test
529:DECNET SCP
526:DECNET NSP
520:DECNET MOP
514:DECNET LAT
508:DECNET DRP
505:DECNET DAP
469:Cronus VLN
168:Token Ring
148:Harry Saal
86:Written in
52:Harry Saal
1521:InfoWorld
1388:InfoWorld
1245:InfoWorld
1226:InfoWorld
1117:InfoWorld
1098:0013-5127
869:Wireshark
762:AppleTalk
748:Token Bus
724:Xerox XNS
718:Xerox RIP
712:Xerox PUP
706:Xerox GGP
703:Xerox EGP
679:TRING MAC
676:TRING LLC
673:TRING DLC
655:Sun RSTAT
643:Sun MOUNT
577:ISO ASN.1
559:IONET VCS
463:ComDesign
132:Wireshark
1614:Category
858:See also
709:Xerox ND
682:TRING RI
649:Sun PMAP
604:Loopback
595:ISO SMTP
589:ISO ROSE
580:ISO CMIP
574:ISO ACSE
496:DEC LAVC
493:DEC LAST
460:Chaosnet
403:AT&T
841:tcpdump
818:Excelan
804:(Sytek)
758:Starlan
652:Sun RPC
646:Sun NFS
619:NetBIOS
586:ISO PPP
553:IBM SNA
550:IBM SMB
541:Excelan
484:DEC 911
358:3COM 3+
175:StarLAN
20:Sniffer
1586:336848
1584:
1574:
1278:GitHub
1096:
787:(SDLC)
727:Xyplex
667:Telnet
658:Sun YP
259:MS-DOS
177:, and
160:ARCNET
99:MS-DOS
1582:S2CID
1503:(PDF)
1485:(PDF)
1468:(PDF)
1425:(PDF)
1406:(PDF)
793:(ATM)
634:RUnix
448:BOOTP
1572:ISBN
1094:ISSN
797:X.25
775:ISDN
770:FDDI
691:X.25
670:TFTP
640:SNAP
637:SMTP
601:LOOP
556:ICMP
150:and
105:Type
1564:doi
1276:on
1086:doi
685:U-B
664:TCP
631:RPL
547:GGP
544:FTP
538:EGP
532:DNS
400:ARP
317:at
1616::
1597:.
1580:.
1570:.
1558:.
1519:.
1442:.
1386:.
1344:.
1320:.
1295:.
1284:^
1243:.
1224:.
1201:.
1141:^
1115:.
1092:.
1082:25
1080:.
1076:.
1032:.
999:.
981:.
963:.
941:.
916:.
892:.
571:IP
134:.
1588:.
1566::
1505:.
1487:.
1452:.
1408:.
1355:.
1330:.
1306:.
1100:.
1088::
926:.
902:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.