61:. Development of the device started in 1952 and lasted a decade. The machine had nine rotors, each with 41 contacts. There were 26 keyboard inputs and outputs, leaving 15 wires to "loop back" through the rotors via a different path. Moreover, each rotor wire could be selected from one of two paths. The movement of the rotors was irregular and controlled by switches. There were two plugboards with the machine; one to scramble the input, and one for the loop-back wires. The machine also used a technique called reinjection (also called reentry), which increased its security exponentially. The machine could be set up in around 10 different configurations.
1041:
1069:
24:
30:
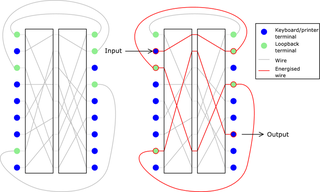
A diagram of a loopback-rotor construction; in this simplified example, two rotors with nine contacts each are used. There are six inputs and outputs, leaving three loop-back wires.
1021:
851:
546:
263:
704:
218:
71:, was alarmed when he read Hagelin's patent on the machine. Friedman realized that the machine was more secure than the NSA's
1106:
188:
126:
256:
697:
148:
900:
249:
230:
Cipher A. Deavours and Louis Kruh, "Machine
Cryptography and Modern Cryptanalysis", Artech House, 1985, p199.
690:
1130:
1016:
971:
784:
895:
1099:
1011:
642:
561:
1001:
991:
846:
326:
68:
551:
118:
Codeknacker gegen
Codemacher: die faszinierende Geschichte der Verschlüsselung; [Sachbuch]
82:
Only twelve of these machines were manufactured, and it was adopted by only one department of the
1125:
996:
986:
789:
749:
742:
732:
727:
627:
286:
737:
488:
351:
346:
116:
1044:
890:
836:
622:
617:
592:
397:
392:
1092:
1006:
930:
655:
341:
301:
8:
769:
650:
536:
213:
875:
859:
806:
935:
925:
796:
184:
122:
83:
870:
64:
336:
174:
1080:
1076:
945:
865:
826:
774:
759:
437:
422:
387:
331:
291:
79:, and Friedman called on Hagelin to terminate the program, which CryptoAG did.
1119:
1026:
981:
940:
920:
816:
779:
754:
483:
278:
58:
50:
976:
821:
811:
801:
764:
713:
503:
180:
76:
955:
541:
407:
915:
885:
880:
841:
516:
207:
905:
54:
950:
910:
665:
660:
571:
556:
511:
463:
442:
23:
1068:
831:
632:
612:
576:
566:
493:
366:
361:
356:
316:
296:
607:
602:
597:
531:
526:
478:
473:
468:
458:
432:
417:
402:
371:
321:
75:
and unbreakable. Friedman and
Hagelin were good friends from
172:
521:
427:
412:
311:
152:
95:
72:
149:"The Scandalous History of the Last Rotor Cipher Machine"
852:
Cryptographically secure pseudorandom number generator
233:
173:Cipher A. Deavours; Louis Kruh (1 January 1985).
1117:
166:
142:
140:
138:
1100:
698:
257:
176:Machine Cryptography and Modern Cryptanalysis
114:
210:— photographs and a brief description
135:
1107:
1093:
705:
691:
264:
250:
214:Notice of a past eBay auction of an HX-63
108:
1075:This cryptography-related article is a
219:John Savard's discussion on the machine
1118:
67:, the first chief cryptologist of the
686:
245:
1063:
146:
271:
69:U.S. National Security Agency (NSA)
13:
224:
22:
14:
1142:
201:
1067:
1040:
1039:
712:
147:Paul, Jon D. (August 31, 2021).
901:Information-theoretic security
1:
101:
1079:. You can help Knowledge by
7:
1017:Message authentication code
972:Cryptographic hash function
785:Cryptographic hash function
121:. W3l GmbH. pp. 208–.
89:
10:
1147:
1062:
896:Harvest now, decrypt later
1035:
1012:Post-quantum cryptography
964:
720:
682:
641:
585:
502:
451:
380:
277:
241:
237:
35:
21:
1002:Quantum key distribution
992:Authenticated encryption
847:Random number generation
997:Public-key cryptography
987:Symmetric-key algorithm
790:Key derivation function
750:Cryptographic primitive
743:Authentication protocol
733:Outline of cryptography
728:History of cryptography
738:Cryptographic protocol
489:Siemens and Halske T52
27:
891:End-to-end encryption
837:Cryptojacking malware
552:Sectéra Secure Module
115:Klaus Schmeh (2008).
26:
1007:Quantum cryptography
931:Trusted timestamping
656:Intel SHA extensions
770:Cryptographic nonce
651:AES instruction set
18:
1131:Cryptography stubs
876:Subliminal channel
860:Pseudorandom noise
807:Key (cryptography)
208:Jerry Proc's pages
28:
16:
1088:
1087:
1057:
1056:
1053:
1052:
936:Key-based routing
926:Trapdoor function
797:Digital signature
678:
677:
674:
673:
643:Computer hardware
388:Bazeries cylinder
190:978-0-89006-161-9
183:. pp. 199–.
128:978-3-937137-89-6
84:French Government
43:
42:
1138:
1109:
1102:
1095:
1071:
1064:
1043:
1042:
871:Insecure channel
707:
700:
693:
684:
683:
266:
259:
252:
243:
242:
239:
238:
235:
234:
195:
194:
170:
164:
163:
161:
159:
144:
133:
132:
112:
65:William Friedman
49:was an advanced
19:
15:
1146:
1145:
1141:
1140:
1139:
1137:
1136:
1135:
1116:
1115:
1114:
1113:
1060:
1058:
1049:
1031:
960:
716:
711:
670:
637:
581:
498:
484:Lorenz SZ 40/42
447:
376:
273:
272:Cipher machines
270:
227:
225:Further reading
204:
199:
198:
191:
171:
167:
157:
155:
145:
136:
129:
113:
109:
104:
92:
31:
12:
11:
5:
1144:
1134:
1133:
1128:
1126:Rotor machines
1112:
1111:
1104:
1097:
1089:
1086:
1085:
1072:
1055:
1054:
1051:
1050:
1048:
1047:
1036:
1033:
1032:
1030:
1029:
1024:
1022:Random numbers
1019:
1014:
1009:
1004:
999:
994:
989:
984:
979:
974:
968:
966:
962:
961:
959:
958:
953:
948:
946:Garlic routing
943:
938:
933:
928:
923:
918:
913:
908:
903:
898:
893:
888:
883:
878:
873:
868:
866:Secure channel
863:
857:
856:
855:
844:
839:
834:
829:
827:Key stretching
824:
819:
814:
809:
804:
799:
794:
793:
792:
787:
777:
775:Cryptovirology
772:
767:
762:
760:Cryptocurrency
757:
752:
747:
746:
745:
735:
730:
724:
722:
718:
717:
710:
709:
702:
695:
687:
680:
679:
676:
675:
672:
671:
669:
668:
663:
658:
653:
647:
645:
639:
638:
636:
635:
630:
625:
620:
615:
610:
605:
600:
595:
589:
587:
583:
582:
580:
579:
574:
569:
564:
559:
554:
549:
544:
539:
534:
529:
524:
519:
514:
508:
506:
500:
499:
497:
496:
491:
486:
481:
476:
471:
466:
461:
455:
453:
449:
448:
446:
445:
440:
438:Reihenschieber
435:
430:
425:
423:Jefferson disk
420:
415:
410:
405:
400:
395:
390:
384:
382:
378:
377:
375:
374:
369:
364:
359:
354:
349:
344:
339:
334:
329:
324:
319:
314:
309:
304:
299:
294:
289:
283:
281:
279:Rotor machines
275:
274:
269:
268:
261:
254:
246:
232:
231:
226:
223:
222:
221:
216:
211:
203:
202:External links
200:
197:
196:
189:
165:
134:
127:
106:
105:
103:
100:
99:
98:
91:
88:
86:(about 1960).
41:
40:
37:
33:
32:
29:
9:
6:
4:
3:
2:
1143:
1132:
1129:
1127:
1124:
1123:
1121:
1110:
1105:
1103:
1098:
1096:
1091:
1090:
1084:
1082:
1078:
1073:
1070:
1066:
1065:
1061:
1046:
1038:
1037:
1034:
1028:
1027:Steganography
1025:
1023:
1020:
1018:
1015:
1013:
1010:
1008:
1005:
1003:
1000:
998:
995:
993:
990:
988:
985:
983:
982:Stream cipher
980:
978:
975:
973:
970:
969:
967:
963:
957:
954:
952:
949:
947:
944:
942:
941:Onion routing
939:
937:
934:
932:
929:
927:
924:
922:
921:Shared secret
919:
917:
914:
912:
909:
907:
904:
902:
899:
897:
894:
892:
889:
887:
884:
882:
879:
877:
874:
872:
869:
867:
864:
861:
858:
853:
850:
849:
848:
845:
843:
840:
838:
835:
833:
830:
828:
825:
823:
820:
818:
817:Key generator
815:
813:
810:
808:
805:
803:
800:
798:
795:
791:
788:
786:
783:
782:
781:
780:Hash function
778:
776:
773:
771:
768:
766:
763:
761:
758:
756:
755:Cryptanalysis
753:
751:
748:
744:
741:
740:
739:
736:
734:
731:
729:
726:
725:
723:
719:
715:
708:
703:
701:
696:
694:
689:
688:
685:
681:
667:
664:
662:
659:
657:
654:
652:
649:
648:
646:
644:
640:
634:
631:
629:
626:
624:
621:
619:
616:
614:
611:
609:
606:
604:
601:
599:
596:
594:
591:
590:
588:
584:
578:
575:
573:
570:
568:
565:
563:
560:
558:
555:
553:
550:
548:
545:
543:
540:
538:
535:
533:
530:
528:
525:
523:
520:
518:
515:
513:
510:
509:
507:
505:
501:
495:
492:
490:
487:
485:
482:
480:
477:
475:
472:
470:
467:
465:
462:
460:
457:
456:
454:
450:
444:
441:
439:
436:
434:
431:
429:
426:
424:
421:
419:
416:
414:
411:
409:
406:
404:
401:
399:
396:
394:
391:
389:
386:
385:
383:
379:
373:
370:
368:
365:
363:
360:
358:
355:
353:
350:
348:
345:
343:
340:
338:
335:
333:
330:
328:
325:
323:
320:
318:
315:
313:
310:
308:
305:
303:
300:
298:
295:
293:
290:
288:
285:
284:
282:
280:
276:
267:
262:
260:
255:
253:
248:
247:
244:
240:
236:
229:
228:
220:
217:
215:
212:
209:
206:
205:
192:
186:
182:
178:
177:
169:
158:September 15,
154:
150:
143:
141:
139:
130:
124:
120:
119:
111:
107:
97:
94:
93:
87:
85:
80:
78:
74:
70:
66:
62:
60:
59:Boris Hagelin
56:
52:
51:rotor machine
48:
39:rotor machine
38:
34:
25:
20:
1081:expanding it
1074:
1059:
977:Block cipher
822:Key schedule
812:Key exchange
802:Kleptography
765:Cryptosystem
714:Cryptography
504:Secure voice
306:
297:M-125 Fialka
181:Artech House
175:
168:
156:. Retrieved
117:
110:
81:
77:World War II
63:
53:designed by
46:
44:
965:Mathematics
956:Mix network
452:Teleprinter
408:Cipher disk
1120:Categories
916:Ciphertext
886:Decryption
881:Encryption
842:Ransomware
517:FASCINATOR
381:Mechanical
102:References
906:Plaintext
55:Crypto AG
1045:Category
951:Kademlia
911:Codetext
854:(CSPRNG)
666:IBM 4764
661:IBM 4758
628:Pinwheel
90:See also
57:founder
721:General
572:STU-III
557:SIGSALY
512:BID 150
464:BID 770
443:Scytale
367:Singlet
327:Mercury
832:Keygen
633:Rockex
623:Purple
613:Noreen
577:VINSON
567:STU-II
537:NESTOR
494:SIGTOT
362:SIGCUM
357:SIGABA
317:Lacida
302:Hebern
292:Enigma
187:
125:
862:(PRN)
608:KL-51
603:KL-43
598:KG-84
586:Other
532:KY-68
527:KY-58
479:KW-37
474:KW-26
469:DUDEK
459:5-UCO
433:M-209
418:Kryha
403:CD-57
372:Typex
352:SG-41
347:SG-39
322:M-325
307:HX-63
47:HX-63
17:HX-63
1077:stub
593:JADE
547:SCIP
542:OMNI
522:KY-3
428:M-94
413:HC-9
398:C-52
393:C-36
332:NEMA
312:KL-7
185:ISBN
160:2021
153:IEEE
123:ISBN
96:KL-7
73:KL-7
45:The
36:Type
618:Red
562:STE
342:RED
337:OMI
287:CCM
1122::
179:.
151:.
137:^
1108:e
1101:t
1094:v
1083:.
706:e
699:t
692:v
265:e
258:t
251:v
193:.
162:.
131:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.