643:. This is a story of buried treasure that was described in 1819–21 by use of a ciphered text that was keyed to the Declaration of Independence. Here each ciphertext character was represented by a number. The number was determined by taking the plaintext character and finding a word in the Declaration of Independence that started with that character and using the numerical position of that word in the Declaration of Independence as the encrypted form of that letter. Since many words in the Declaration of Independence start with the same letter, the encryption of that character could be any of the numbers associated with the words in the Declaration of Independence that start with that letter. Deciphering the encrypted text character
1445:. This was deciphered rather quickly by the die hard viewers by showing a "Slurm" ad with the word "Drink" in both plain English and the Alien language thus giving the key. Later, the producers created a second alien language that used a combination of replacement and mathematical Ciphers. Once the English letter of the alien language is deciphered, then the numerical value of that letter (0 for "A" through 25 for "Z" respectively) is then added (modulo 26) to the value of the previous letter showing the actual intended letter. These messages can be seen throughout every episode of the series and the subsequent movies.
1581:, January 31, 2007: "Back at Munich headquarters, he told prosecutors, he learned of an encryption code he alleged was widely used at Siemens to itemize bribe payments. He said it was derived from the phrase "Make Profit," with the phrase's 10 letters corresponding to the numbers 1-2-3-4-5-6-7-8-9-0. Thus, with the letter A standing for 2 and P standing for 5, a reference to "file this in the APP file" meant a bribe was authorized at 2.55 percent of sales. - A spokesman for Siemens said it has no knowledge of a "Make Profit" encryption system."
536:
415:
2568:
525:
1069:
25:
786:) which enabled the calculation of the length of the keyword in a Vigenère ciphered message. Once this was done, ciphertext letters that had been enciphered under the same alphabet could be picked out and attacked separately as a number of semi-independent simple substitutions - complicated by the fact that within one alphabet letters were separated and did not form complete words, but simplified by the fact that usually a
1122:
516:, 27.6 letters of ciphertext are required to crack a mixed alphabet simple substitution. In practice, typically about 50 letters are needed, although some messages can be broken with fewer if unusual patterns are found. In other cases, the plaintext can be contrived to have a nearly flat frequency distribution, and much longer plaintexts will then be required by the cryptanalyst.
295:
738:. The tableau is usually 26×26, so that 26 full ciphertext alphabets are available. The method of filling the tableau, and of choosing which alphabet to use next, defines the particular polyalphabetic cipher. All such ciphers are easier to break than once believed, as substitution alphabets are repeated for sufficiently large plaintexts.
245:. In a transposition cipher, the units of the plaintext are rearranged in a different and usually quite complex order, but the units themselves are left unchanged. By contrast, in a substitution cipher, the units of the plaintext are retained in the same sequence in the ciphertext, but the units themselves are altered.
1140:(for some governments this was approximately the 1950s or 1960s; for other organizations it was a decade or more later; for individuals it was no earlier than 1975), mechanical implementations of polyalphabetic substitution ciphers were widely used. Several inventors had similar ideas about the same time, and
854:
In a polygraphic substitution cipher, plaintext letters are substituted in larger groups, instead of substituting letters individually. The first advantage is that the frequency distribution is much flatter than that of individual letters (though not actually flat in real languages; for example, 'OS'
693:(1312–1359), contained the first published discussion of the substitution and transposition of ciphers, as well as the first description of a polyalphabetic cipher, in which each plaintext letter is assigned more than one substitute. Polyalphabetic substitution ciphers were later described in 1467 by
650:
Another homophonic cipher was described by Stahl and was one of the first attempts to provide for computer security of data systems in computers through encryption. Stahl constructed the cipher in such a way that the number of homophones for a given character was in proportion to the frequency of the
555:
sheet containing letter, syllable and word substitution tables, sometimes homophonic, that typically converted symbols into numbers. Originally the code portion was restricted to the names of important people, hence the name of the cipher; in later years, it covered many common words and place names
793:
As such, even today a Vigenère type cipher should theoretically be difficult to break if mixed alphabets are used in the tableau, if the keyword is random, and if the total length of ciphertext is less than 27.67 times the length of the keyword. These requirements are rarely understood in practice,
631:
Since more than 26 characters will be required in the ciphertext alphabet, various solutions are employed to invent larger alphabets. Perhaps the simplest is to use a numeric substitution 'alphabet'. Another method consists of simple variations on the existing alphabet; uppercase, lowercase, upside
770:
26.) A keyword is then used to choose which ciphertext alphabet to use. Each letter of the keyword is used in turn, and then they are repeated again from the beginning. So if the keyword is 'CAT', the first letter of plaintext is enciphered under alphabet 'C', the second under 'A', the third under
1171:
from amongst the huge number of possible combinations resulting from the rotation of several letter disks. Since one or more of the disks rotated mechanically with each plaintext letter enciphered, the number of alphabets used was astronomical. Early versions of these machine were, nevertheless,
461:
Although the traditional keyword method for creating a mixed substitution alphabet is simple, a serious disadvantage is that the last letters of the alphabet (which are mostly low frequency) tend to stay at the end. A stronger way of constructing a mixed alphabet is to generate the substitution
912:
in 1854. In this cipher, a 5 x 5 grid is filled with the letters of a mixed alphabet (two letters, usually I and J, are combined). A digraphic substitution is then simulated by taking pairs of letters as two corners of a rectangle, and using the other two corners as the ciphertext (see the
238:, in a defined manner, with the help of a key; the "units" may be single letters (the most common), pairs of letters, triplets of letters, mixtures of the above, and so forth. The receiver deciphers the text by performing the inverse substitution process to extract the original message.
1607:
771:'T', the fourth under 'C' again, and so on, or if the keyword is 'RISE', the first letter of plaintext is enciphered under alphabet 'R', the second under 'I', the third under 'S', the fourth under 'E', and so on. In practice, Vigenère keys were often phrases several words long.
628:. In these ciphers, plaintext letters map to more than one ciphertext symbol. Usually, the highest-frequency plaintext symbols are given more equivalents than lower frequency letters. In this way, the frequency distribution is flattened, making analysis more difficult.
1534: – lossless data compression algorithms which operate by looking for matches between the text to be compressed and a set of strings (“dictionary”) maintained by the encoder; such a match is substituted by a reference to the string’s position in the set
1253:; his work was first published in the late 1940s. In its most common implementation, the one-time pad can be called a substitution cipher only from an unusual perspective; typically, the plaintext letter is combined (not substituted) in some manner (e.g.,
1604:
389:
and to help avoid transmission errors. These blocks are called "groups", and sometimes a "group count" (i.e. the number of groups) is given as an additional check. Five-letter groups are often used, dating from when messages used to be transmitted by
1315:
Substitution ciphers as discussed above, especially the older pencil-and-paper hand ciphers, are no longer in serious use. However, the cryptographic concept of substitution carries on even today. From an abstract perspective, modern bit-oriented
667:, while imprisoned by Elizabeth I, during the years from 1578 to 1584 used homophonic ciphers with additional encryption using a nomenclator for frequent prefixes, suffixes, and proper names while communicating with her allies including
422:
Such features make little difference to the security of a scheme, however – at the very least, any set of strange symbols can be transcribed back into an A-Z alphabet and dealt with as normal.
1390:
is actually a substitution cipher, although it is pronounced phonetically (i.e. "you" in
English is translated to "oui" in Al Bhed, but is pronounced the same way that "oui" is pronounced in
333:. Traditionally, mixed alphabets may be created by first writing out a keyword, removing repeated letters in it, then writing all the remaining letters in the alphabet in the usual order.
197:
760:, the first row of the tableau is filled out with a copy of the plaintext alphabet, and successive rows are simply shifted one place to the left. (Such a simple tableau is called a
1022:
264:
uses a number of substitutions at different positions in the message, where a unit from the plaintext is mapped to one of several possibilities in the ciphertext and vice versa.
1271:
once, and kept entirely secret from all except the sender and intended receiver. When these conditions are violated, even marginally, the one-time pad is no longer unbreakable.
190:
893:
mentioned above, della Porta actually proposed such a system, with a 20 x 20 tableau (for the 20 letters of the
Italian/Latin alphabet he was using) filled with 400 unique
887:
855:
is much more common than 'RÑ' in
Spanish). Second, the larger number of symbols requires correspondingly more ciphertext to productively analyze letter frequencies.
1497:, there are substitution ciphers hidden throughout the game in which the player must find code books to help decipher them and gain access to a surplus of supplies.
1279:
key material. US cryptanalysts, beginning in the late 40s, were able to, entirely or partially, break a few thousand messages out of several hundred thousand. (See
647:(which is a number) is as simple as looking up the Xth word of the Declaration of Independence and using the first letter of that word as the decrypted character.
2548:
2378:
593:
from the early fifteenth century to the late eighteenth century; most conspirators were and have remained less cryptographically sophisticated. Although
1477:
there are three substitution ciphers; Gnommish, Centaurean and
Eternean, which run along the bottom of the pages or are somewhere else within the books.
607:
was simply to make the tables larger. By the late eighteenth century, when the system was beginning to die out, some nomenclators had 50,000 symbols.
917:
main article for a diagram). Special rules handle double letters and pairs falling in the same row or column. Playfair was in military use from the
632:
down, etc. More artistically, though not necessarily more securely, some homophonic ciphers employed wholly invented alphabets of fanciful symbols.
385:
Usually the ciphertext is written out in blocks of fixed length, omitting punctuation and spaces; this is done to disguise word boundaries from the
1805:
842:
can also be seen, from a sufficiently abstract perspective, to be a form of polyalphabetic cipher in which all the effort has gone into making the
477:
of the ciphertext. This allows formation of partial words, which can be tentatively filled in, progressively expanding the (partial) solution (see
622:
An early attempt to increase the difficulty of frequency analysis attacks on substitution ciphers was to disguise plaintext letter frequencies by
603:
were systematically breaking nomenclators by the mid-sixteenth century, and superior systems had been available since 1467, the usual response to
730:
In a polyalphabetic cipher, multiple cipher alphabets are used. To facilitate encryption, all the alphabets are usually written out in a large
2231:
1418:
204:
481:
for a demonstration of this). In some cases, underlying words can also be determined from the pattern of their letters; for example, the
713:(see below; ca. 1500 but not published until much later). A more sophisticated version using mixed alphabets was described in 1563 by
1196:
began. Traffic protected by essentially all of the German military
Enigmas was broken by Allied cryptanalysts, most notably those at
1624:
801:
The
Gronsfeld cipher. This is identical to the Vigenère except that only 10 alphabets are used, and so the "keyword" is numerical.
89:
1438:
1462:, or a letter-to-number simple substitution cipher. The season 1 finale encodes a message with all three. In the second season,
61:
1200:, beginning with the German Army variant used in the early 1930s. This version was broken by inspired mathematical insight by
404:". These can be any characters that decrypt to obvious nonsense, so that the receiver can easily spot them and discard them.
1798:
1337:
1086:
1044:
661:, used the earliest known example of a homophonic substitution cipher in 1401 for correspondence with one Simone de Crema.
68:
42:
425:
In lists and catalogues for salespeople, a very simple encryption is sometimes used to replace numeric digits by letters.
610:
Nevertheless, not all nomenclators were broken; today, cryptanalysis of archived ciphertexts remains a fruitful area of
469:), this cipher is not very strong, and is easily broken. Provided the message is of reasonable length (see below), the
248:
There are a number of different types of substitution cipher. If the cipher operates on single letters, it is termed a
2224:
1706:
1108:
108:
75:
2021:
2606:
1353:
2011:
1260:
The one-time pad is, in most cases, impractical as it requires that the key material be as long as the plaintext,
1791:
1024:(to ensure decryption is possible). A mechanical version of the Hill cipher of dimension 6 was patented in 1929.
2016:
57:
2427:
1722:
Toemeh, Ragheb (2014). "Certain investigations in
Cryptanalysis of classical ciphers Using genetic algorithm".
1640:" Proceedings of the national computer conference and exposition (AFIPS '73), pp. 123–126, New York, USA, 1973.
1090:
313:—can be demonstrated by writing out the alphabet in some order to represent the substitution. This is termed a
158:
46:
1298:
812:
is replaced by a backwards one, mathematically equivalent to ciphertext = key - plaintext. This operation is
714:
1356:". There, the cipher remained undeciphered for years if not decades; not due to its difficulty, but because
453:
Examples: MAT would be used to represent 120, PAPR would be used for 5256, and OFTK would be used for 7803.
2601:
2217:
1637:
1325:
1177:
993:
2543:
2498:
2311:
719:
2031:
2596:
2422:
1502:
1364:
2538:
1769:
955:, is a polygraphic substitution which can combine much larger groups of letters simultaneously using
558:
414:
1506:, the language of Ente Isla, called Entean, uses a substitution cipher with the ciphertext alphabet
1466:
are used in place of the various monoalphabetic ciphers, each using a key hidden within its episode.
745:. First published in 1585, it was considered unbreakable until 1863, and indeed was commonly called
400:
If the length of the message happens not to be divisible by five, it may be padded at the end with "
2528:
2518:
2373:
1698:
1321:
478:
2523:
2513:
2316:
2276:
2269:
2259:
2254:
1578:
1079:
1040:
82:
35:
407:
The ciphertext alphabet is sometimes different from the plaintext alphabet; for example, in the
2264:
1550:
1153:
1028:
964:
694:
590:
474:
267:
The first ever published description of how to crack simple substitution ciphers was given by
2571:
2417:
2363:
2142:
1833:
1692:
1329:
680:
154:
2067:
1434:
contained a substitution cipher in which all 26 letters were replaced by symbols and called
865:
742:
325:
ciphers, respectively) or scrambled in a more complex fashion, in which case it is called a
2533:
2457:
2173:
2077:
2003:
1304:
1181:
979:
664:
242:
150:
8:
2296:
2192:
2187:
2101:
1470:
1173:
731:
698:
668:
654:
624:
597:
575:
552:
547:. Named after the public official who announced the titles of visiting dignitaries, this
465:
Although the number of possible substitution alphabets is very large (26! ≈ 2, or about
2402:
2386:
2333:
2168:
2087:
1993:
1925:
1673:
1412:
1144:
were patented four times in 1919. The most important of the resulting machines was the
983:
937:
909:
831:
767:
276:
180:
1856:
1545:
1463:
1332:
alphabet. In addition, block ciphers often include smaller substitution tables called
1219:
machines were ever broken during or near the time when these systems were in service.
757:
2462:
2452:
2323:
2137:
2057:
2026:
1920:
1851:
1702:
1677:
1493:
1435:
824:
775:
1043:
steps like a Hill cipher, with non-linear substitution steps, ultimately leads to a
2397:
1814:
1727:
1663:
1531:
1422:
1295:
1242:
929:
513:
509:
482:
1668:
1651:
1454:, during the credit roll, there is one of three simple substitution ciphers: A -3
1192:
solved versions of the Enigma machine (those without the "plugboard") well before
794:
and so Vigenère enciphered message security is usually less than might have been.
1958:
1915:
1884:
1866:
1611:
1485:
1442:
1391:
1386:
1349:
1275:
one-time pad messages sent from the US for a brief time during World War II used
1201:
963:: A = 0, B =1, and so on. (In a variation, 3 extra symbols are added to make the
918:
914:
905:
834:, where the key is made very long by using a passage from a book or similar text.
805:
783:
750:
690:
411:, the ciphertext consists of a set of symbols derived from a grid. For example:
2472:
2392:
2353:
2301:
2286:
2177:
2072:
1953:
1846:
1841:
1526:
1280:
1246:
1238:
1197:
1145:
1048:
960:
956:
952:
820:
686:
658:
535:
529:
401:
1745:
778:
published a method (probably discovered secretly and independently before the
2590:
2553:
2508:
2467:
2447:
2343:
2306:
2281:
2129:
1983:
1963:
1943:
1894:
1874:
1614:", afips, pp. 565, 1973 Proceedings of the National Computer Conference, 1973
1455:
1450:
1357:
1141:
1125:
941:
839:
706:
640:
604:
470:
408:
318:
302:
1039:
step to defeat this attack. The combination of wider and wider weak, linear
473:
can deduce the probable meaning of the most common symbols by analyzing the
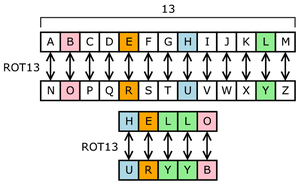
305:, a type of substitution cipher. In ROT13, the alphabet is rotated 13 steps.
2503:
2348:
2338:
2328:
2291:
2240:
2062:
1973:
1879:
1555:
1317:
1272:
1250:
1234:
1228:
1193:
1189:
1052:
971:
967:
933:
922:
762:
600:
571:
219:
162:
1772:
Breaking A Monoalphabetic
Encryption System Using a Known Plaintext Attack
1051:), so it is possible – from this extreme perspective – to consider modern
766:, and mathematically corresponds to adding the plaintext and key letters,
2482:
2147:
2114:
2109:
1978:
1488:, substitution ciphers serve as an important form of coded communication.
1474:
1133:
948:
779:
636:
2442:
2412:
2407:
2368:
2181:
2163:
1968:
1899:
1731:
1520:
1276:
1093: in this section. Unsourced material may be challenged and removed.
1036:
897:. However the system was impractical and probably never actually used.
594:
567:
524:
502:
391:
359:
235:
227:
1510:, leaving only A, E, I, O, U, L, N, and Q in their original positions.
2432:
2119:
1403:
1373:
1149:
975:
843:
586:
582:
386:
346:
231:
1458:(hinted by "3 letters back" at the end of the opening sequence), an
1167:
All of these were similar in that the substituted letter was chosen
1068:
816:, whereby the same table is used for both encryption and decryption.
24:
2477:
2437:
1889:
1430:
1185:
1168:
1137:
466:
268:
140:
566:
in modern parlance) were not distinguished in the ciphertext. The
1398:
1381:
709:
for "hidden writing") introduced the now more standard form of a
611:
172:
Varies (typically 88 bits for mixed alphabet simple substitution)
928:
Several other practical polygraphics were introduced in 1901 by
862:
of letters would take a substitution alphabet 676 symbols long (
2358:
2082:
1948:
1822:
1459:
1291:
1287:
1264:
1212:
1205:
1157:
1032:
987:
651:
character, thus making frequency analysis much more difficult.
548:
322:
317:. The cipher alphabet may be shifted or reversed (creating the
275:
written around 850 CE. The method he described is now known as
252:; a cipher that operates on larger groups of letters is termed
1290:
equipment, the one-time pad was used for messages sent on the
2052:
2047:
1988:
1333:
1216:
1161:
1121:
894:
724:
298:
1650:
Lasry, George; Biermann, Norbert; Tomokiyo, Satoshi (2023).
1237:, is unique. It was invented near the end of World War I by
986:
26. The components of the matrix are the key, and should be
1540:
1448:
At the end of every season 1 episode of the cartoon series
808:. This is practically the same as the Vigenère, except the
260:
uses fixed substitution over the entire message, whereas a
1211:
As far as is publicly known, no messages protected by the
543:
One once-common variant of the substitution cipher is the
1254:
501:. Many people solve such ciphers for recreation, as with
294:
1652:"Deciphering Mary Stuart's lost letters from 1578-1584"
1245:
in the US. It was mathematically proven unbreakable by
2379:
Cryptographically secure pseudorandom number generator
1128:
machine as used by the German military in World War II
639:
is a type of homophonic cipher, one example being the
1649:
996:
868:
1775:
1536:
Pages displaying wikidata descriptions as a fallback
1257:) with the key material character at that position.
1328:) can be viewed as substitution ciphers on a large
49:. Unsourced material may be challenged and removed.
1638:A homophonic cipher for computational cryptography
1605:A homophonic cipher for computational cryptography
1016:
881:
273:A Manuscript on Deciphering Cryptographic Messages
2588:
1286:In a mechanical implementation, rather like the
970:.) A block of n letters is then considered as a
1694:Passwords: Philology, Security, Authentication
1360:, instead considering it childish scribblings.
1156:also developed and used rotor machines (e.g.,
2225:
1799:
1575:At Siemens, witnesses cite pattern of bribery
1407:series is a substitution cipher from English.
198:
823:, which mixes plaintext with a key to avoid
1625:Coding for Data and Computer Communications
944:(probably the first practical trigraphic).
904:(pairwise substitution), was the so-called
727:for "On concealed characters in writing").
528:The forged nomenclator message used in the
16:System to replace plaintext with ciphertext
2232:
2218:
1813:
1806:
1792:
990:provided that the matrix is invertible in
689:(1355-1418), based on the earlier work of
309:Substitution of single letters separately—
241:Substitution ciphers can be compared with
205:
191:
1667:
1310:
1148:, especially in the versions used by the
1109:Learn how and when to remove this message
999:
109:Learn how and when to remove this message
1120:
534:
523:
293:
1055:as a type of polygraphic substitution.
959:. Each letter is treated as a digit in
846:as long and unpredictable as possible.
797:Other notable polyalphabetics include:
581:Nomenclators were the standard fare of
2589:
1721:
1690:
556:as well. The symbols for whole words (
2213:
1787:
1421:is also a substitution cipher of the
1343:
1233:One type of substitution cipher, the
1017:{\displaystyle \mathbb {Z} _{26}^{n}}
1746:"Message Protector patent US1845947"
1091:adding citations to reliable sources
1062:
741:One of the most popular was that of
340:" gives us the following alphabets:
47:adding citations to reliable sources
18:
1136:and the widespread availability of
1035:, so it must be combined with some
1027:The Hill cipher is vulnerable to a
13:
413:
14:
2618:
1763:
1352:breaks a substitution cipher in "
674:
562:in modern parlance) and letters (
382:SIAA ZQ LKBA. VA ZOA RFPBLUAOAR!
376:flee at once. we are discovered!
2567:
2566:
2239:
1358:no one suspected it to be a code
1354:The Adventure of the Dancing Men
1338:substitution–permutation network
1067:
1045:substitution–permutation network
336:Using this system, the keyword "
23:
1222:
1180:early found vulnerabilities in
1078:needs additional citations for
539:A French nomenclator code table
34:needs additional citations for
2428:Information-theoretic security
1738:
1715:
1684:
1643:
1630:
1617:
1597:
1594:, University of Illinois, 1974
1584:
1573:David Crawford / Mike Esterl,
1567:
1417:spoken by native Saurians and
849:
753:for "indecipherable cipher").
519:
462:alphabet completely randomly.
397:SIAAZ QLKBA VAZOA RFPBL UAOAR
159:Homophonic substitution cipher
1:
1669:10.1080/01611194.2022.2160677
1561:
1152:from approximately 1930. The
1058:
715:Giovanni Battista della Porta
617:
1556:Musical Substitution Ciphers
1367:, the writing system in the
978:, and multiplied by a n x n
7:
2544:Message authentication code
2499:Cryptographic hash function
2312:Cryptographic hash function
1770:Monoalphabetic Substitution
1514:
1500:In the anime adaptation of
891:De Furtivis Literarum Notis
720:De Furtivis Literarum Notis
456:
10:
2623:
2423:Harvest now, decrypt later
1508:AZYXEWVTISRLPNOMQKJHUGFDCB
1503:The Devil Is a Part-Timer!
1365:Standard Galactic Alphabet
1226:
678:
505:puzzles in the newspaper.
366:ZEBRASCDFGHIJKLMNOPQTUVWXY
353:ABCDEFGHIJKLMNOPQRSTUVWXYZ
250:simple substitution cipher
2562:
2539:Post-quantum cryptography
2491:
2247:
2209:
2156:
2128:
2100:
2040:
2002:
1934:
1908:
1865:
1832:
1821:
1783:
1779:
1592:On Computational Security
1031:because it is completely
940:(both digraphic) and the
747:le chiffre indéchiffrable
734:, traditionally called a
589:, and advanced political
440:
430:
418:An example pigpen message
358:
345:
289:
186:
176:
168:
146:
136:
131:
126:
2529:Quantum key distribution
2519:Authenticated encryption
2374:Random number generation
1699:Harvard University Press
284:
2607:History of cryptography
2524:Public-key cryptography
2514:Symmetric-key algorithm
2317:Key derivation function
2277:Cryptographic primitive
2270:Authentication protocol
2260:Outline of cryptography
2255:History of cryptography
1579:The Wall Street Journal
1491:In the 2013 video game
1428:The television program
900:The earliest practical
2265:Cryptographic protocol
1815:Classical cryptography
1691:Lennon, Brian (2018).
1551:Topics in cryptography
1311:In modern cryptography
1303:established after the
1182:Hebern's rotor machine
1129:
1029:known-plaintext attack
1018:
951:, invented in 1929 by
883:
882:{\displaystyle 26^{2}}
697:in the form of disks.
695:Leone Battista Alberti
540:
532:
475:frequency distribution
419:
306:
234:are replaced with the
2418:End-to-end encryption
2364:Cryptojacking malware
1484:, the third novel by
1401:'s alphabet from the
1142:rotor cipher machines
1124:
1019:
884:
681:Polyalphabetic cipher
538:
527:
497:all have the pattern
441:Ciphertext alphabets
417:
315:substitution alphabet
297:
262:polyalphabetic cipher
258:monoalphabetic cipher
243:transposition ciphers
155:Polyalphabetic cipher
58:"Substitution cipher"
2534:Quantum cryptography
2458:Trusted timestamping
2174:Index of coincidence
2078:Reservehandverfahren
1305:Cuban Missile Crisis
1087:improve this article
994:
866:
665:Mary, Queen of Scots
151:Transposition cipher
43:improve this article
2602:Fictional languages
2297:Cryptographic nonce
2193:Kasiski examination
2188:Information leakage
1748:. February 14, 1929
1523:with Centiban Table
1471:Artemis Fowl series
1371:video games and in
1174:William F. Friedman
1013:
938:four-square ciphers
790:had been employed.
699:Johannes Trithemius
669:Michel de Castelnau
655:Francesco I Gonzaga
612:historical research
576:Louis XIV of France
311:simple substitution
224:substitution cipher
127:General Information
123:
122:Substitution cipher
2403:Subliminal channel
2387:Pseudorandom noise
2334:Key (cryptography)
2169:Frequency analysis
2068:Rasterschlüssel 44
1610:2016-04-09 at the
1441:2022-12-25 at the
1413:Starfox Adventures
1344:In popular culture
1249:, probably during
1130:
1014:
997:
910:Charles Wheatstone
908:, invented by Sir
879:
832:running key cipher
743:Blaise de Vigenère
541:
533:
479:frequency analysis
420:
307:
277:frequency analysis
230:in which units of
181:Frequency analysis
121:
2597:Classical ciphers
2584:
2583:
2580:
2579:
2463:Key-based routing
2453:Trapdoor function
2324:Digital signature
2205:
2204:
2201:
2200:
2096:
2095:
1627:. Springer, 2005.
1494:BioShock Infinite
1415:: Dinosaur Planet
1176:of the US Army's
1119:
1118:
1111:
776:Friedrich Kasiski
508:According to the
451:
450:
431:Plaintext digits
371:
370:
331:deranged alphabet
215:
214:
132:Technical Details
119:
118:
111:
93:
2614:
2570:
2569:
2398:Insecure channel
2234:
2227:
2220:
2211:
2210:
1830:
1829:
1808:
1801:
1794:
1785:
1784:
1781:
1780:
1777:
1776:
1758:
1757:
1755:
1753:
1742:
1736:
1735:
1719:
1713:
1712:
1688:
1682:
1681:
1671:
1647:
1641:
1636:Fred A. Stahl. "
1634:
1628:
1621:
1615:
1603:Stahl, Fred A. "
1601:
1595:
1590:Stahl, Fred A.,
1588:
1582:
1571:
1537:
1532:Dictionary coder
1509:
1464:Vigenère ciphers
1436:"Alien Language"
1423:English alphabet
1410:The language in
1267:, used once and
1243:Joseph Mauborgne
1114:
1107:
1103:
1100:
1094:
1071:
1063:
1023:
1021:
1020:
1015:
1012:
1007:
1002:
932:, including the
930:Felix Delastelle
902:digraphic cipher
888:
886:
885:
880:
878:
877:
585:correspondence,
510:unicity distance
446:
436:
428:
427:
367:
354:
343:
342:
339:
207:
200:
193:
124:
120:
114:
107:
103:
100:
94:
92:
51:
27:
19:
2622:
2621:
2617:
2616:
2615:
2613:
2612:
2611:
2587:
2586:
2585:
2576:
2558:
2487:
2243:
2238:
2197:
2152:
2124:
2092:
2036:
1998:
1930:
1904:
1867:Polybius square
1861:
1825:
1817:
1812:
1766:
1761:
1751:
1749:
1744:
1743:
1739:
1720:
1716:
1709:
1689:
1685:
1648:
1644:
1635:
1631:
1623:David Salomon.
1622:
1618:
1612:Wayback Machine
1602:
1598:
1589:
1585:
1572:
1568:
1564:
1546:Vigenère cipher
1535:
1517:
1507:
1486:Kristin Cashore
1443:Wayback Machine
1387:Final Fantasy X
1350:Sherlock Holmes
1346:
1313:
1231:
1225:
1202:Marian Rejewski
1150:German military
1132:Between around
1115:
1104:
1098:
1095:
1084:
1072:
1061:
1008:
1003:
998:
995:
992:
991:
915:Playfair cipher
906:Playfair cipher
889:). In the same
873:
869:
867:
864:
863:
852:
806:Beaufort cipher
784:Charles Babbage
758:Vigenère cipher
691:Ibn al-Durayhim
683:
677:
620:
522:
459:
444:
434:
398:
383:
377:
365:
352:
337:
292:
287:
226:is a method of
217:
211:
147:Related Methods
115:
104:
98:
95:
52:
50:
40:
28:
17:
12:
11:
5:
2620:
2610:
2609:
2604:
2599:
2582:
2581:
2578:
2577:
2575:
2574:
2563:
2560:
2559:
2557:
2556:
2551:
2549:Random numbers
2546:
2541:
2536:
2531:
2526:
2521:
2516:
2511:
2506:
2501:
2495:
2493:
2489:
2488:
2486:
2485:
2480:
2475:
2473:Garlic routing
2470:
2465:
2460:
2455:
2450:
2445:
2440:
2435:
2430:
2425:
2420:
2415:
2410:
2405:
2400:
2395:
2393:Secure channel
2390:
2384:
2383:
2382:
2371:
2366:
2361:
2356:
2354:Key stretching
2351:
2346:
2341:
2336:
2331:
2326:
2321:
2320:
2319:
2314:
2304:
2302:Cryptovirology
2299:
2294:
2289:
2287:Cryptocurrency
2284:
2279:
2274:
2273:
2272:
2262:
2257:
2251:
2249:
2245:
2244:
2237:
2236:
2229:
2222:
2214:
2207:
2206:
2203:
2202:
2199:
2198:
2196:
2195:
2190:
2185:
2171:
2166:
2160:
2158:
2154:
2153:
2151:
2150:
2145:
2140:
2134:
2132:
2126:
2125:
2123:
2122:
2117:
2112:
2106:
2104:
2098:
2097:
2094:
2093:
2091:
2090:
2085:
2080:
2075:
2073:Reihenschieber
2070:
2065:
2060:
2055:
2050:
2044:
2042:
2038:
2037:
2035:
2034:
2029:
2024:
2019:
2014:
2008:
2006:
2000:
1999:
1997:
1996:
1991:
1986:
1981:
1976:
1971:
1966:
1961:
1956:
1951:
1946:
1940:
1938:
1932:
1931:
1929:
1928:
1923:
1918:
1912:
1910:
1906:
1905:
1903:
1902:
1897:
1892:
1887:
1882:
1877:
1871:
1869:
1863:
1862:
1860:
1859:
1854:
1849:
1844:
1838:
1836:
1834:Polyalphabetic
1827:
1819:
1818:
1811:
1810:
1803:
1796:
1788:
1774:
1773:
1765:
1764:External links
1762:
1760:
1759:
1737:
1714:
1707:
1701:. p. 26.
1683:
1662:(2): 101–202.
1642:
1629:
1616:
1596:
1583:
1565:
1563:
1560:
1559:
1558:
1553:
1548:
1543:
1538:
1529:
1527:Copiale cipher
1524:
1516:
1513:
1512:
1511:
1498:
1489:
1478:
1467:
1446:
1426:
1408:
1395:
1378:
1369:Commander Keen
1361:
1345:
1342:
1312:
1309:
1281:Venona project
1247:Claude Shannon
1239:Gilbert Vernam
1227:Main article:
1224:
1221:
1198:Bletchley Park
1117:
1116:
1075:
1073:
1066:
1060:
1057:
1049:Feistel cipher
1011:
1006:
1001:
957:linear algebra
953:Lester S. Hill
876:
872:
858:To substitute
851:
848:
840:stream ciphers
836:
835:
828:
821:autokey cipher
817:
802:
703:Steganographia
701:, in his book
687:Al-Qalqashandi
679:Main article:
676:
675:Polyalphabetic
673:
659:Duke of Mantua
619:
616:
530:Babington Plot
521:
518:
458:
455:
449:
448:
442:
438:
437:
432:
396:
381:
375:
369:
368:
363:
356:
355:
350:
327:mixed alphabet
291:
288:
286:
283:
213:
212:
210:
209:
202:
195:
187:
184:
183:
178:
174:
173:
170:
166:
165:
148:
144:
143:
138:
134:
133:
129:
128:
117:
116:
31:
29:
22:
15:
9:
6:
4:
3:
2:
2619:
2608:
2605:
2603:
2600:
2598:
2595:
2594:
2592:
2573:
2565:
2564:
2561:
2555:
2554:Steganography
2552:
2550:
2547:
2545:
2542:
2540:
2537:
2535:
2532:
2530:
2527:
2525:
2522:
2520:
2517:
2515:
2512:
2510:
2509:Stream cipher
2507:
2505:
2502:
2500:
2497:
2496:
2494:
2490:
2484:
2481:
2479:
2476:
2474:
2471:
2469:
2468:Onion routing
2466:
2464:
2461:
2459:
2456:
2454:
2451:
2449:
2448:Shared secret
2446:
2444:
2441:
2439:
2436:
2434:
2431:
2429:
2426:
2424:
2421:
2419:
2416:
2414:
2411:
2409:
2406:
2404:
2401:
2399:
2396:
2394:
2391:
2388:
2385:
2380:
2377:
2376:
2375:
2372:
2370:
2367:
2365:
2362:
2360:
2357:
2355:
2352:
2350:
2347:
2345:
2344:Key generator
2342:
2340:
2337:
2335:
2332:
2330:
2327:
2325:
2322:
2318:
2315:
2313:
2310:
2309:
2308:
2307:Hash function
2305:
2303:
2300:
2298:
2295:
2293:
2290:
2288:
2285:
2283:
2282:Cryptanalysis
2280:
2278:
2275:
2271:
2268:
2267:
2266:
2263:
2261:
2258:
2256:
2253:
2252:
2250:
2246:
2242:
2235:
2230:
2228:
2223:
2221:
2216:
2215:
2212:
2208:
2194:
2191:
2189:
2186:
2183:
2179:
2175:
2172:
2170:
2167:
2165:
2162:
2161:
2159:
2157:Cryptanalysis
2155:
2149:
2146:
2144:
2141:
2139:
2136:
2135:
2133:
2131:
2130:Steganography
2127:
2121:
2118:
2116:
2113:
2111:
2108:
2107:
2105:
2103:
2099:
2089:
2086:
2084:
2081:
2079:
2076:
2074:
2071:
2069:
2066:
2064:
2061:
2059:
2056:
2054:
2051:
2049:
2046:
2045:
2043:
2039:
2033:
2030:
2028:
2025:
2023:
2020:
2018:
2015:
2013:
2010:
2009:
2007:
2005:
2004:Transposition
2001:
1995:
1992:
1990:
1987:
1985:
1982:
1980:
1977:
1975:
1972:
1970:
1967:
1965:
1962:
1960:
1957:
1955:
1952:
1950:
1947:
1945:
1942:
1941:
1939:
1937:
1933:
1927:
1924:
1922:
1919:
1917:
1914:
1913:
1911:
1907:
1901:
1898:
1896:
1893:
1891:
1888:
1886:
1883:
1881:
1878:
1876:
1873:
1872:
1870:
1868:
1864:
1858:
1855:
1853:
1850:
1848:
1845:
1843:
1840:
1839:
1837:
1835:
1831:
1828:
1824:
1820:
1816:
1809:
1804:
1802:
1797:
1795:
1790:
1789:
1786:
1782:
1778:
1771:
1768:
1767:
1747:
1741:
1733:
1729:
1725:
1718:
1710:
1708:9780674985377
1704:
1700:
1696:
1695:
1687:
1679:
1675:
1670:
1665:
1661:
1657:
1653:
1646:
1639:
1633:
1626:
1620:
1613:
1609:
1606:
1600:
1593:
1587:
1580:
1576:
1570:
1566:
1557:
1554:
1552:
1549:
1547:
1544:
1542:
1539:
1533:
1530:
1528:
1525:
1522:
1519:
1518:
1505:
1504:
1499:
1496:
1495:
1490:
1487:
1483:
1479:
1476:
1472:
1468:
1465:
1461:
1460:Atbash cipher
1457:
1456:Caesar cipher
1453:
1452:
1451:Gravity Falls
1447:
1444:
1440:
1437:
1433:
1432:
1427:
1424:
1420:
1416:
1414:
1409:
1406:
1405:
1400:
1396:
1393:
1389:
1388:
1383:
1379:
1376:
1375:
1370:
1366:
1362:
1359:
1355:
1351:
1348:
1347:
1341:
1339:
1335:
1331:
1327:
1323:
1319:
1318:block ciphers
1308:
1306:
1302:
1301:
1297:
1293:
1289:
1284:
1282:
1278:
1274:
1270:
1266:
1263:
1258:
1256:
1252:
1248:
1244:
1240:
1236:
1230:
1220:
1218:
1214:
1209:
1207:
1203:
1199:
1195:
1191:
1187:
1183:
1179:
1175:
1170:
1165:
1163:
1159:
1155:
1151:
1147:
1143:
1139:
1135:
1127:
1126:Enigma cipher
1123:
1113:
1110:
1102:
1099:February 2017
1092:
1088:
1082:
1081:
1076:This section
1074:
1070:
1065:
1064:
1056:
1054:
1053:block ciphers
1050:
1046:
1042:
1038:
1034:
1030:
1025:
1009:
1004:
989:
985:
981:
977:
973:
969:
966:
962:
958:
954:
950:
945:
943:
942:trifid cipher
939:
935:
931:
926:
924:
920:
916:
911:
907:
903:
898:
896:
892:
874:
870:
861:
856:
847:
845:
841:
833:
829:
826:
822:
818:
815:
811:
807:
803:
800:
799:
798:
795:
791:
789:
785:
781:
777:
772:
769:
765:
764:
759:
754:
752:
748:
744:
739:
737:
733:
728:
726:
722:
721:
717:in his book,
716:
712:
708:
707:Ancient Greek
704:
700:
696:
692:
688:
682:
672:
670:
666:
662:
660:
656:
652:
648:
646:
642:
641:Beale ciphers
638:
633:
629:
627:
626:
615:
613:
608:
606:
605:cryptanalysis
602:
601:cryptanalysts
599:
596:
592:
588:
584:
579:
577:
573:
569:
565:
561:
560:
554:
551:uses a small
550:
546:
537:
531:
526:
517:
515:
511:
506:
504:
500:
496:
492:
488:
484:
480:
476:
472:
468:
463:
454:
443:
439:
433:
429:
426:
423:
416:
412:
410:
409:pigpen cipher
405:
403:
395:
393:
388:
380:
379:enciphers to
374:
364:
361:
357:
351:
348:
344:
341:
334:
332:
328:
324:
320:
316:
312:
304:
303:Caesar cipher
300:
296:
282:
280:
278:
274:
270:
265:
263:
259:
255:
251:
246:
244:
239:
237:
233:
229:
225:
221:
208:
203:
201:
196:
194:
189:
188:
185:
182:
179:
177:Cryptanalysis
175:
171:
167:
164:
160:
156:
152:
149:
145:
142:
139:
135:
130:
125:
113:
110:
102:
91:
88:
84:
81:
77:
74:
70:
67:
63:
60: –
59:
55:
54:Find sources:
48:
44:
38:
37:
32:This article
30:
26:
21:
20:
2504:Block cipher
2349:Key schedule
2339:Key exchange
2329:Kleptography
2292:Cryptosystem
2241:Cryptography
2063:One-time pad
1936:Substitution
1935:
1750:. Retrieved
1740:
1723:
1717:
1693:
1686:
1659:
1655:
1645:
1632:
1619:
1599:
1591:
1586:
1574:
1569:
1501:
1492:
1481:
1449:
1429:
1411:
1402:
1385:
1384:language in
1372:
1368:
1314:
1299:
1285:
1268:
1261:
1259:
1251:World War II
1235:one-time pad
1232:
1229:One-time pad
1223:One-time pad
1210:
1190:Dillwyn Knox
1169:electrically
1166:
1131:
1105:
1096:
1085:Please help
1080:verification
1077:
1026:
946:
927:
923:World War II
901:
899:
890:
859:
857:
853:
837:
814:self-inverse
813:
810:tabula recta
809:
796:
792:
788:tabula recta
787:
773:
763:tabula recta
761:
755:
746:
740:
735:
729:
718:
710:
702:
685:The work of
684:
663:
653:
649:
644:
634:
630:
623:
621:
609:
598:intelligence
580:
572:Great Cipher
563:
557:
544:
542:
507:
498:
494:
490:
486:
471:cryptanalyst
464:
460:
452:
424:
421:
406:
399:
384:
378:
372:
335:
330:
326:
314:
310:
308:
281:
272:
266:
261:
257:
253:
249:
247:
240:
223:
220:cryptography
216:
163:One-time pad
105:
96:
86:
79:
72:
65:
53:
41:Please help
36:verification
33:
2492:Mathematics
2483:Mix network
2115:Code talker
1994:Running key
1926:Four-square
1752:November 9,
1732:10603/26543
1656:Cryptologia
1475:Eoin Colfer
1336:. See also
1172:breakable.
1134:World War I
949:Hill cipher
850:Polygraphic
825:periodicity
780:Crimean War
637:book cipher
545:nomenclator
520:Nomenclator
373:A message
254:polygraphic
2591:Categories
2443:Ciphertext
2413:Decryption
2408:Encryption
2369:Ransomware
2164:Cryptogram
2058:Kama Sutra
2027:Rail fence
2022:Myszkowski
1969:Chaocipher
1921:Two-square
1900:VIC cipher
1852:Trithemius
1724:Shodhganga
1562:References
1521:Ban (unit)
1482:Bitterblue
1296:Washington
1277:non-random
1059:Mechanical
1037:non-linear
976:dimensions
618:Homophonic
595:government
591:conspiracy
583:diplomatic
568:Rossignols
503:cryptogram
445:MAKEPROFIT
435:1234567890
360:Ciphertext
236:ciphertext
228:encrypting
99:March 2009
69:newspapers
2433:Plaintext
2088:Solitaire
1826:by family
1678:256720092
1404:Babylon 5
1374:Minecraft
1186:GC&CS
1138:computers
1041:diffusive
844:keystream
774:In 1863,
625:homophony
587:espionage
578:was one.
559:codewords
392:telegraph
387:plaintext
362:alphabet
349:alphabet
347:Plaintext
232:plaintext
2572:Category
2478:Kademlia
2438:Codetext
2381:(CSPRNG)
2176:(Units:
2012:Columnar
1959:Beaufort
1916:Playfair
1890:Tap code
1885:Nihilist
1857:Vigenère
1608:Archived
1515:See also
1439:Archived
1431:Futurama
1300:hot line
1262:actually
1047:(e.g. a
921:through
919:Boer War
574:used by
457:Security
269:Al-Kindi
169:Key Size
141:Al-Kindi
137:Inventor
2248:General
1954:Autokey
1842:Alberti
1823:Ciphers
1469:In the
1419:Krystal
1399:Minbari
1382:Al Bhed
1334:S-boxes
1320:(e.g.,
961:base 26
838:Modern
756:In the
736:tableau
711:tableau
514:English
483:English
467:88 bits
447:
83:scholar
2359:Keygen
2143:Grille
2083:Slidex
2017:Double
1984:Pigpen
1964:Caesar
1949:Atbash
1944:Affine
1909:Square
1895:Trifid
1875:ADFGVX
1847:Enigma
1705:
1676:
1392:French
1330:binary
1292:Moscow
1288:Rockex
1273:Soviet
1265:random
1213:SIGABA
1206:Poland
1184:, and
1158:SIGABA
1154:Allies
1146:Enigma
1033:linear
988:random
984:modulo
980:matrix
972:vector
895:glyphs
768:modulo
751:French
564:cipher
549:cipher
493:, and
485:words
338:zebras
323:Atbash
319:Caesar
290:Simple
85:
78:
71:
64:
56:
2389:(PRN)
2138:Bacon
2102:Codes
2053:DRYAD
2048:BATCO
2041:Other
2032:Route
1989:ROT13
1974:Great
1880:Bifid
1674:S2CID
1363:The
1324:, or
1217:Typex
1162:Typex
974:of n
968:prime
965:basis
934:bifid
860:pairs
732:table
725:Latin
499:ABACD
495:paper
491:ninth
487:tater
402:nulls
301:is a
299:ROT13
285:Types
90:JSTOR
76:books
2180:and
2148:Null
2120:Poem
2110:Book
1979:Hill
1754:2013
1703:ISBN
1541:Leet
1397:The
1380:The
1269:only
1241:and
1215:and
1194:WWII
1160:and
947:The
936:and
830:The
819:The
804:The
635:The
553:code
321:and
256:. A
222:, a
62:news
2182:Nat
2178:Ban
1728:hdl
1664:doi
1480:In
1473:by
1326:AES
1322:DES
1255:XOR
1204:in
1188:'s
1178:SIS
1164:).
1089:by
782:by
512:of
329:or
271:in
218:In
45:by
2593::
1726:.
1697:.
1672:.
1660:47
1658:.
1654:.
1577:,
1394:).
1340:.
1307:.
1283:)
1208:.
1005:26
982:,
925:.
871:26
671:.
657:,
614:.
570:'
489:,
394::
279:.
161:,
157:,
153:,
2233:e
2226:t
2219:v
2184:)
1807:e
1800:t
1793:v
1756:.
1734:.
1730::
1711:.
1680:.
1666::
1425:.
1377:.
1294:-
1112:)
1106:(
1101:)
1097:(
1083:.
1010:n
1000:Z
875:2
827:.
749:(
723:(
705:(
645:X
206:e
199:t
192:v
112:)
106:(
101:)
97:(
87:·
80:·
73:·
66:·
39:.
Text is available under the Creative Commons Attribution-ShareAlike License. Additional terms may apply.